Investigating Windows
A windows machine has been hacked, its your job to go investigate this windows machine and find clues to what the hacker might have done.
This is a challenge that is exactly what is says on the tin, there are a few challenges around investigating a windows machine that has been previously compromised.
Connect to the machine using RDP. The credentials the machine are as follows:
Username: Administrator
Password: letmein123!
No Hints.
Connect
We can deploy the machine on tryhackme page or connect via RDP
Connect using xfreerdp12
xfreerdp /u:Administrator /p:letmein123! /v:10.10.164.154
Open powershell
What's the version and year of the Windows machine?
Execute the command to get system information
systeminfo
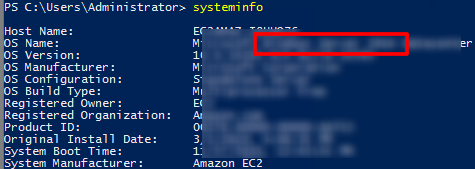
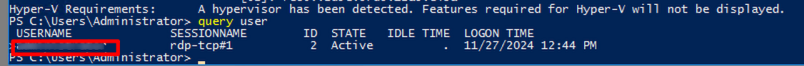
Which user logged in last?
Execute the command to check the logon users
query user
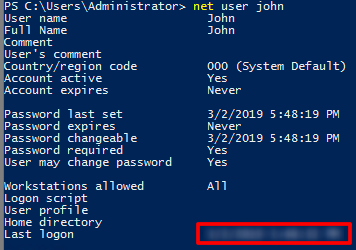
When did John log onto the system last?
Use the command
net user john
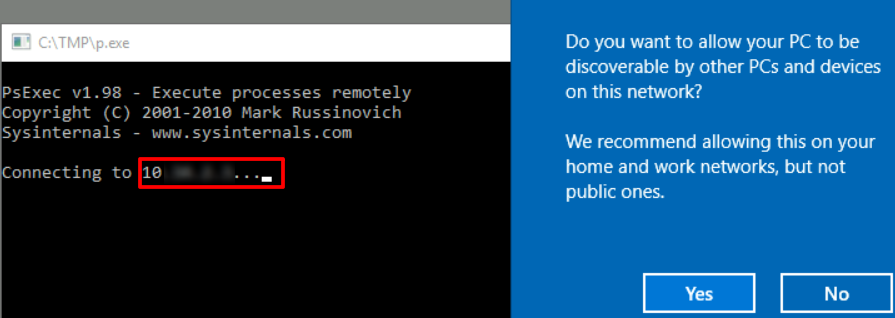
What IP does the system connect to when it first starts?
When the system starts the IP is showed
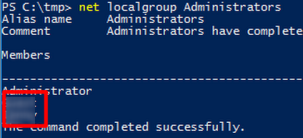
What two accounts had administrative privileges (other than the Administrator user)?
Show users from the administrator group, that user have administrator privileges.
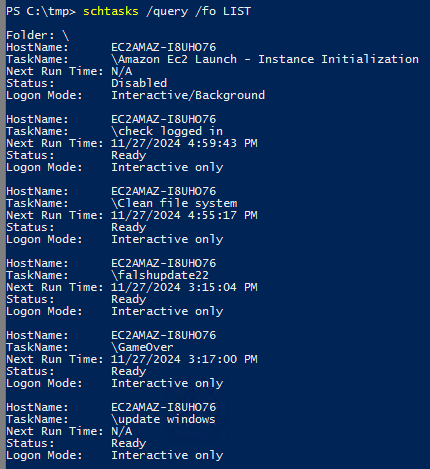
What's the name of the scheduled task that is malicious.
List schedule tasks
schtasks /query /fo /LIST
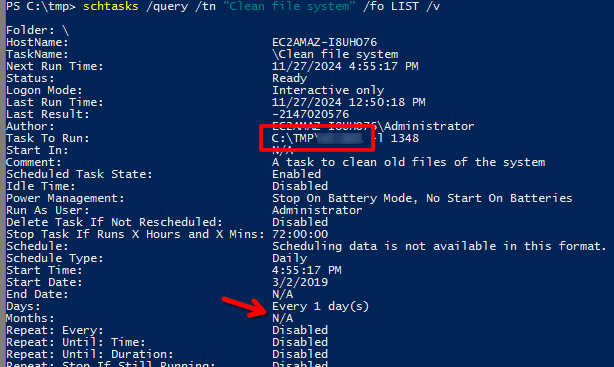
Tog get more info of each of them execute
schtasks /query /tn "TASK_NAME_HERE" /fo LIST /v
You'll notice that one of them is triyng to execute an ps1 file.
What file was the task trying to run daily?
Is one of all interesting tasks Check all of them getting more info with
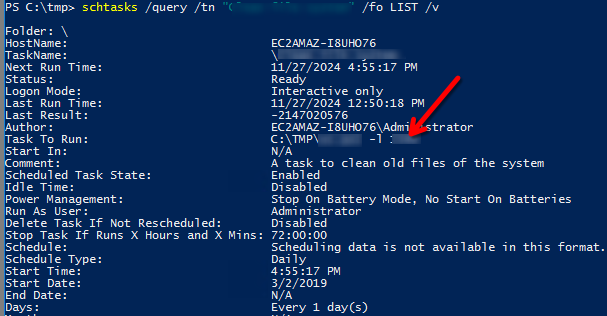
schtasks /query /tn "Clean file system" /fo LIST /v
What port did this file listen locally for?
schtasks /query /tn "Clean file system" /fo LIST /v
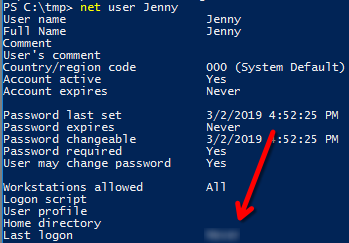
When did Jenny last logon?
net user Jenny
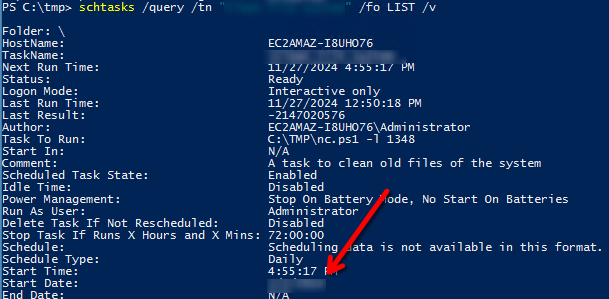
At what date did the compromise take place?
schtasks /query /tn "Clean file system" /fo LIST /v
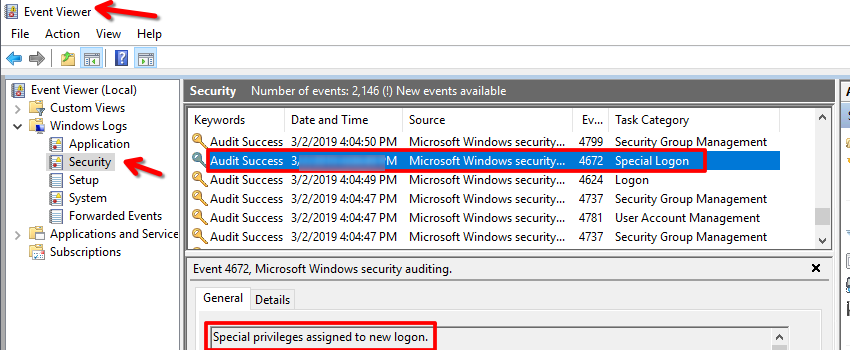
During the compromise, at what time did Windows first assign special privileges to a new logon?
Open the Event Viewer
Select Security
What tool was used to get Windows passwords?
Check the file
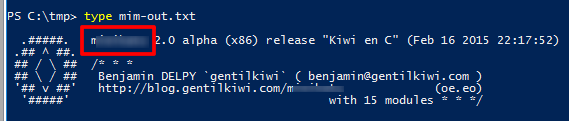
What was the attackers external control and command servers IP?
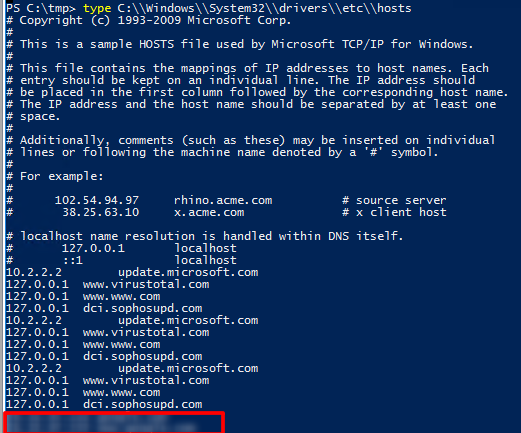
The machine is connecting to external so let's check the Windows Host File Location
type C:\\Windows\\System32\\drivers\\etc\\hosts
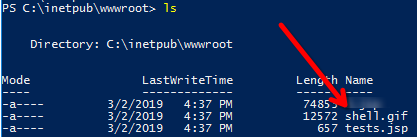
What was the extension name of the shell uploaded via the servers website?
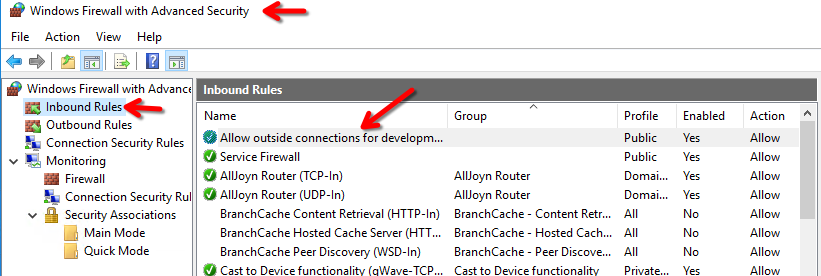
What was the last port the attacker opened?
Check the firewall config, inbound rules and check the port
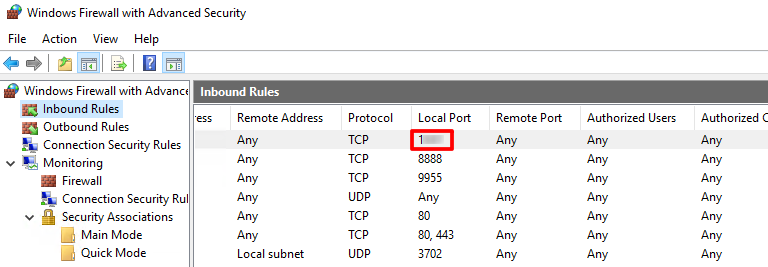
Check for DNS poisoning, what site was targeted?
type C:\\Windows\\System32\\drivers\\etc\\hosts
