Anthem
Exploit a Windows machine in this beginner level challenge.
This task involves you, paying attention to details and finding the 'keys to the castle'.
This room is designed for beginners, however, everyone is welcomed to try it out!
Enjoy the Anthem.
In this room, you don't need to brute force any login page. Just your preferred browser and Remote Desktop.
Active reconnaissance
Port scan
Perform a quick general scan on all ports.
sudo nmap TARGET_IP -n -p- -sS -Pn -vvv --open --min-rate 5000 -oN nmap_scan
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 125
3389/tcp open ms-wbt-server syn-ack ttl 125
80
3389
Enumeration
Perform a deep scan with common scripts only on ports we are interested in.
sudo nmap TARGET_IP -sCV -p 22,80 -oN nmap_enum
OS
Windows; CPE: cpe:/o:microsoft:windows
Port 80 - Umbraco
tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
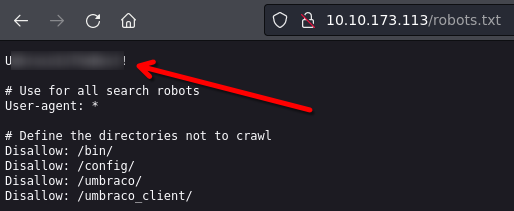
|http-title: Anthem.com - Welcome to our blog
| http-robots.txt: 4 disallowed entries
|/bin/ /config/ /umbraco/ /umbraco_client/
bin
Its empty
config
The same main page
umbraco_client
The same main page
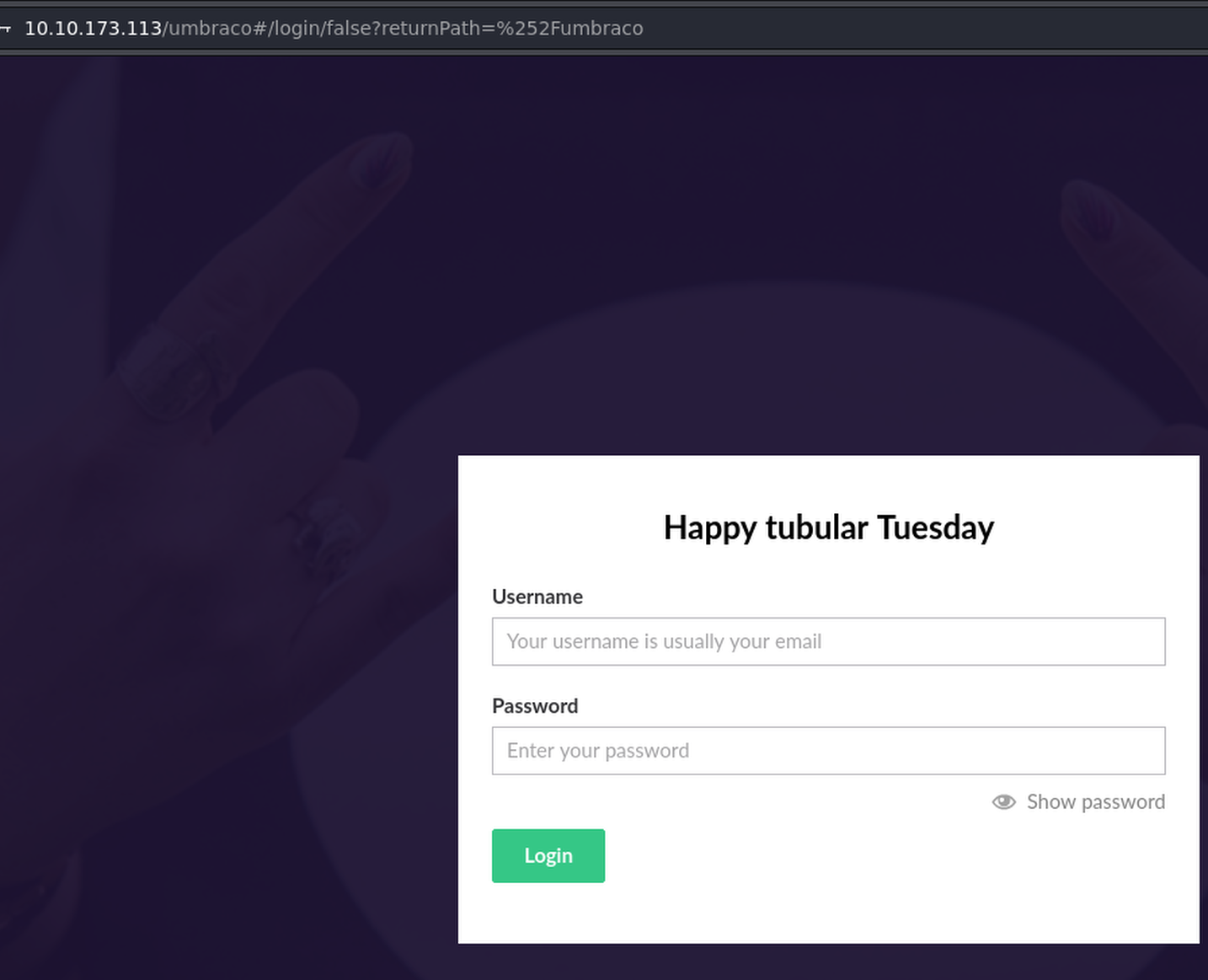
Umbraco
We have a login page
Umbraco
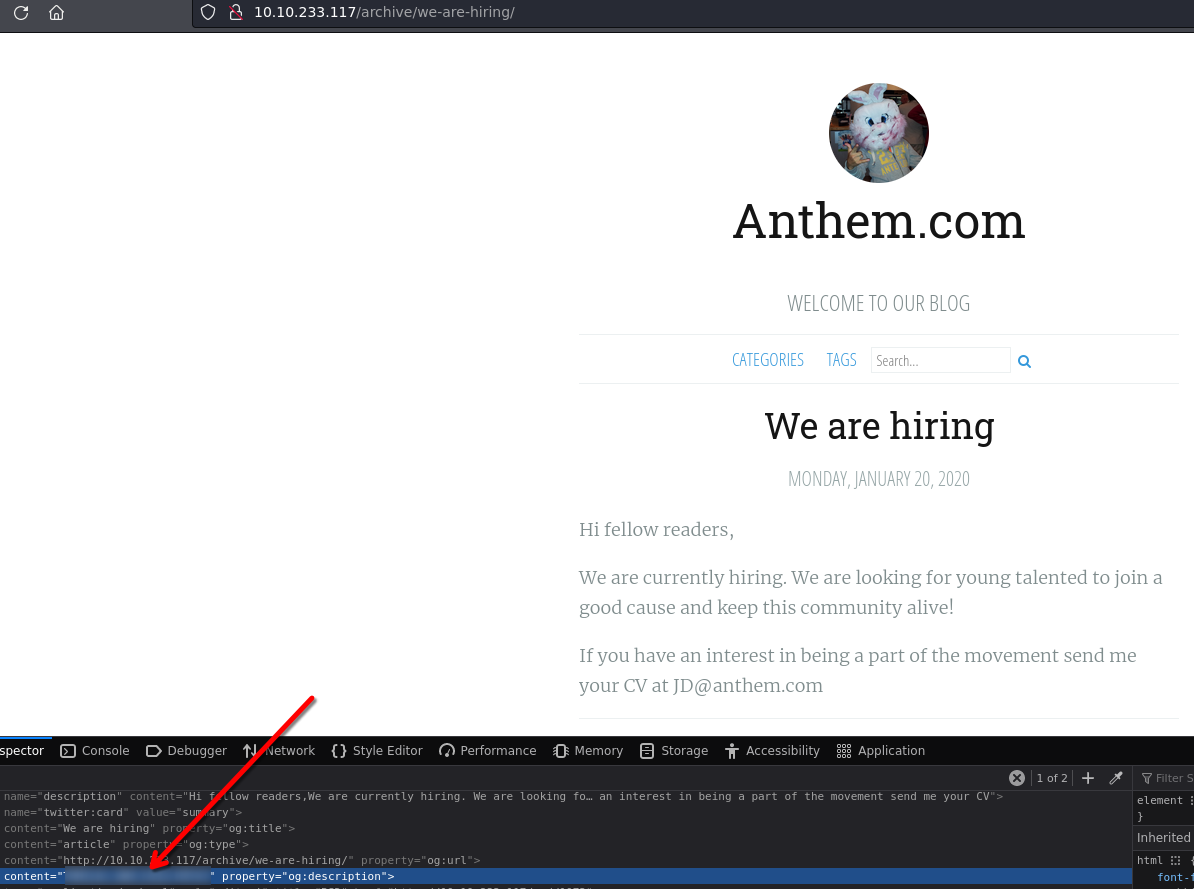
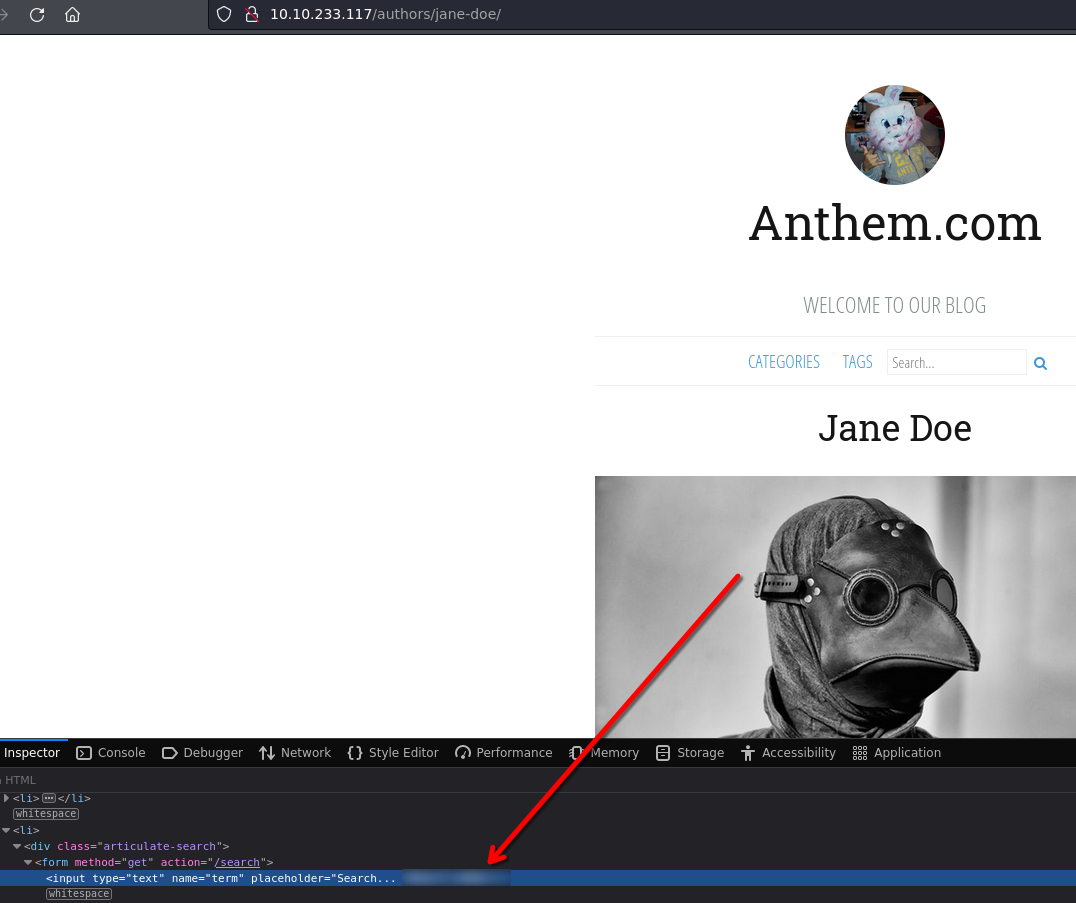
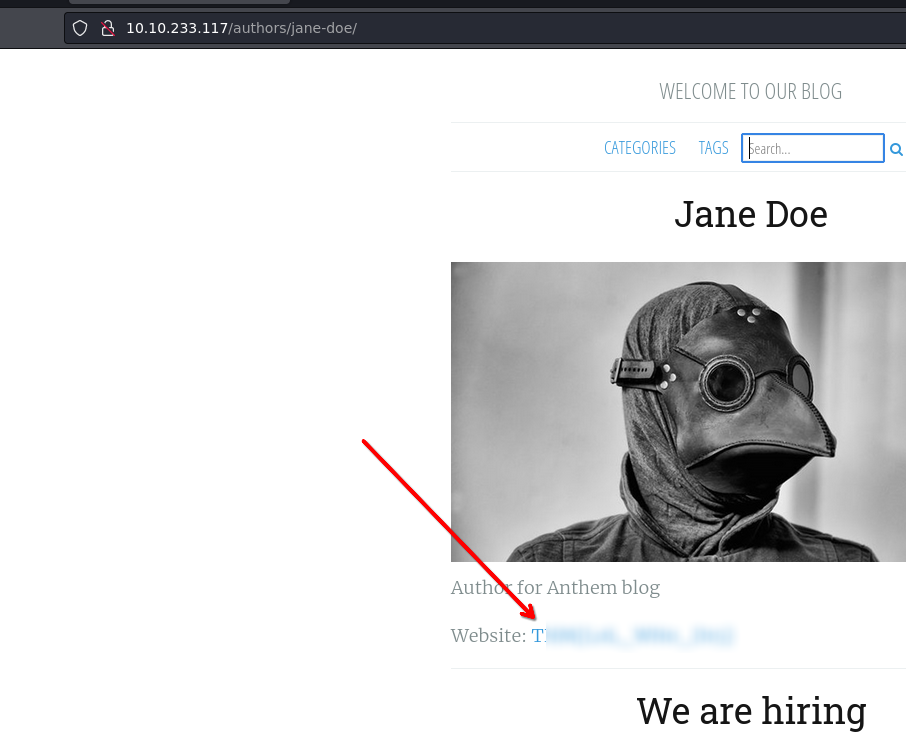
It's the author of the poem
According to the pattern of Jane Doe and its email jd@anthem.com
The email will be sg@anthem.com
Port 3389 - RDP
tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: WIN-LU09299160F
| NetBIOS_Domain_Name: WIN-LU09299160F
| NetBIOS_Computer_Name: WIN-LU09299160F
| DNS_Domain_Name: WIN-LU09299160F
| DNS_Computer_Name: WIN-LU09299160F
| Product_Version: 10.0.17763
|_ System_Time: 2025-01-07T14:18:27+00:00
| ssl-cert: Subject: commonName=WIN-LU09299160F
| Not valid before: 2025-01-06T14:15:34
|Not valid after: 2025-07-08T14:15:34
ssl-date: 2025-01-07T14:19:27+00:00; +1s from scanner timeH
Exploitation
Port 80 - Umbraco
Dashboard
After login with credentials
We have:
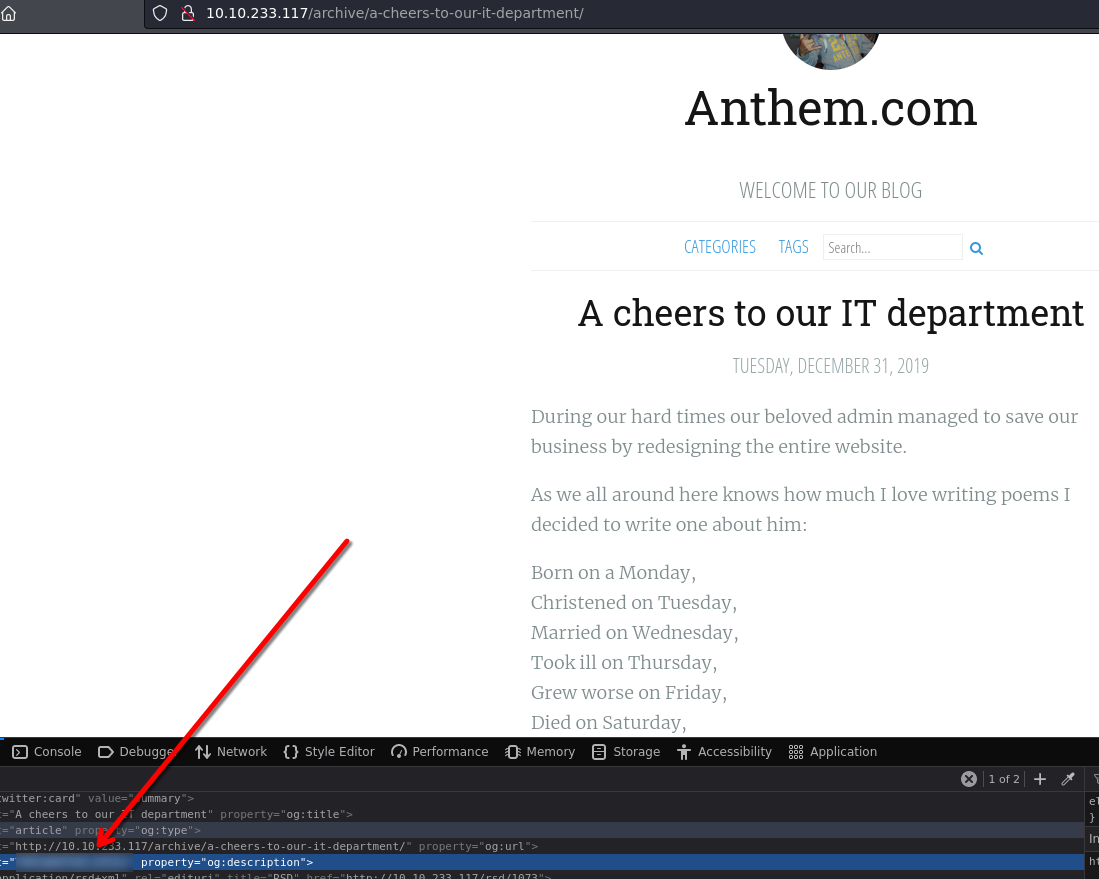
Port 3389 - RDP
xfreerdp /u:sg /p:UmbracoIsTheBest! /v:10.10.233.117 /shell:cmd.exe
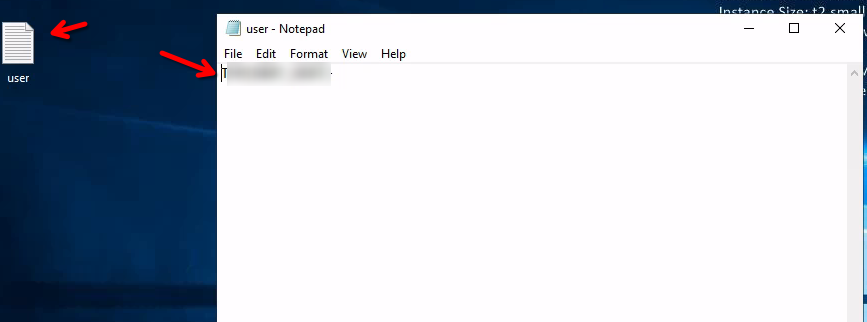
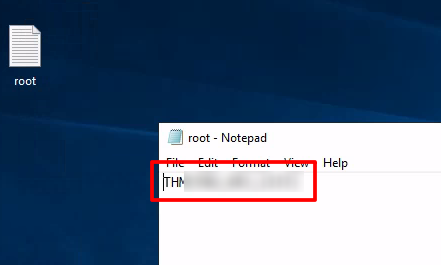
In the hidden folder
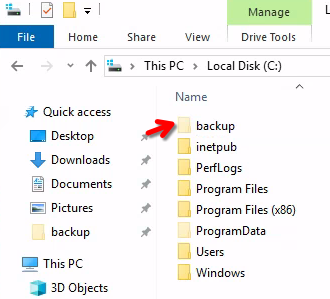
Click on setting of restore file and add our user to the permissions file.
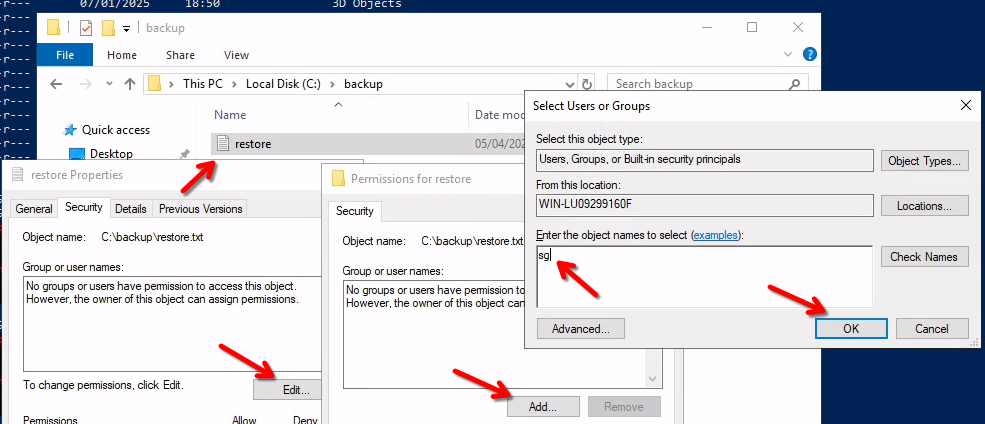
And open the file:
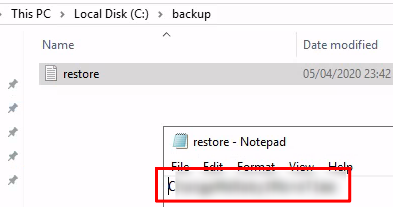
Privilege escalation
Login to the administrator account
xfreerdp /u:Administrator /p:ChangeMeBaby1MoreTime /v:10.10.233.117