SSH
- Secure Shell
- Default port 22
- Cryptographic remote access protocol
- We will need to confirm the fingerprint of the SSH server’s public key to avoid MITM attack
Username and password Authentication
ssh bandit0@bandit.labs.overthewire.org -p 2220
ssh bandit0@bandit.labs.overthewire.org -p 2220 -oHostKeyAlgorithms=+ssh-rsa
sshpass -p 'password' ssh bandit0@bandit.labs.overthewire.org -p 2220
RSA keys Authentication
- Data encrypted with the private key can be decrypted with the public key, and vice versa.
- tends to be slower and uses larger keys
Enable service daemon
sudo systemctl start sshd
Create keys
Create pair of keys RSA keys in `/home/USER/.ssh
ssh-keygen
id_rsa (private) (400 permissions required to remote connection)
id_rsa.pub (public)
Connect from M2 to M1 without password
1### Method 1
The public key (id_rsa.pub) of computer 2 has to be in the file authorized_keys in the computer 1
The process to do this depend on some factors but If the authorized_keys file doesn't exist, we can simply copy the entire id_rsa.pub and change the name, but if the authorized_keys exists could content another authorized keys that we shouldn't delete. In this case we could add our key in the bottom of the authorized_keys like below:
- On the computer 2
Copy the content of the file/home/USER/.ssh/id_rsa.pub
cat /home/USER/.ssh/id_rsa.pub

Copy to the clipboard
- On the computer 1
Usingechopaste the code and add or replace theauthorized_keys
echo "ssh-rsa AAAA......gv7v......y2w/oJ0= kali@kali" >> authorized_keys
E.g. This is the new authorized_keysof the computer 1
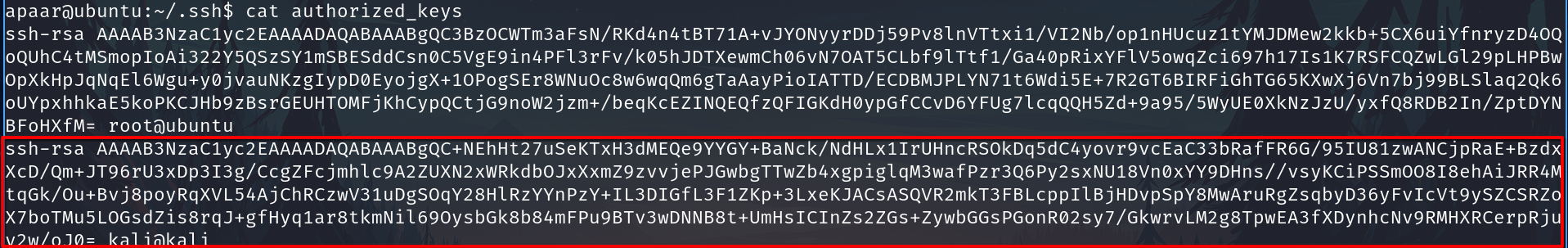
- On the computer 2
All is ready, now to connect without password execute:
ssh USER_OF_COMPUTER_1@IP_COF_COMPUTER_1
Method 2
Automated version of the method 1 but we need to introduce the password of the computer 1 at least once.
- On the computer 2
ssh-copy-id -i ~/.ssh/id_rsa.pub COMPUTER_1_USERNAME@COMPUTER_1_IP
After this our id_rsa.pub will copy on authorized_keys of the computer 1.
Method 3
- Set the public key of comp1 like "authorized_keys" on its machine (Could not work depending on configuration)
To let to any connect to comp1 if the computer2 has the private key of comp1.
cp id_rsa.pub authorized_keys
- Copy the private key (
id_rsa) from C1 to C2 - From C2 connect using that private key file of C1 (
id_rsa) (the permission should be600)
ssh -i id_rsa user@ipaddres
ssh -i root_key -oPubkeyAcceptedKeyTypes=+ssh-rsa -oHostKeyAlgorithms=+ssh-rsa root@10.10.250.21
Port forwarding
80 port from a victim machine which we don't have access will be available in our machine on 127.0.0.1:33
ssh user@"VICTIM_IP" -L 80:127.0.0.1:33
Transfer files
Math
- The key variables that you need to know about for RSA in CTFs are p, q, m, n, e, d, and c.
- “p” and “q” are large prime numbers, “n” is the product of p and q.
- The public key is n and e, the private key is n and d.
- “m” is used to represent the message (in plaintext) and “c” represents the ciphertext (encrypted text).
- https://muirlandoracle.co.uk/2020/01/29/rsa-encryption/
Tools RSA CTFs
https://github.com/Ganapati/RsaCtfTool
https://github.com/ius/rsatool
Errors
- If you get an error saying
Unable to negotiate with <IP> port 22: no matching how to key type found. Their offer: ssh-rsa, ssh-dss - this is because OpenSSH have deprecated ssh-rsa.
- Add
-oHostKeyAlgorithms=+ssh-rsato your command to connect.
Enumeration
Get version and search in launchpad.
sudo nmap -sCV -p22 127.0.0.1
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0)
https://launchpad.net/ubuntu
OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13
Using Metasploit
Exploitation
Exploit libssh
libsshV.0.6.0 - 0.8-0 is vulnerable to an authentication bypass vulnerability in thelibsshserver code that can be exploited to execute commands on the target server.