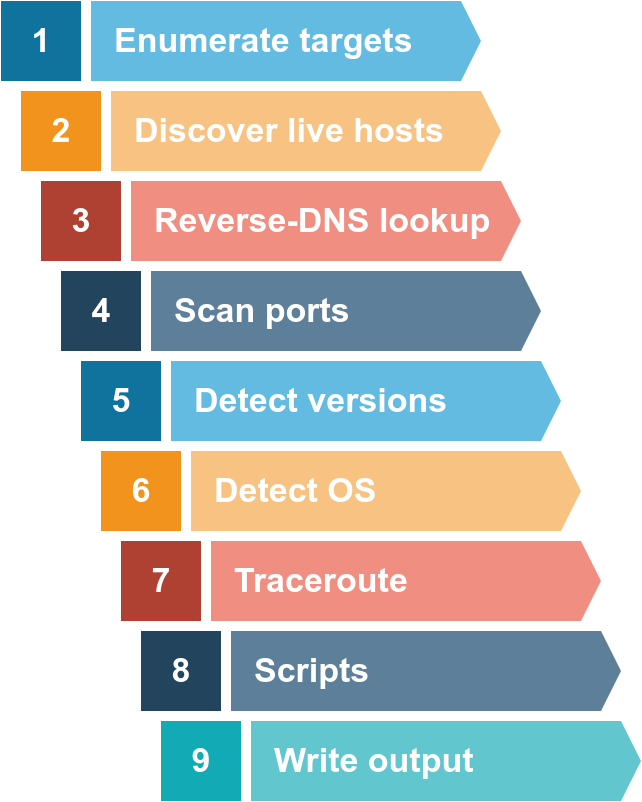
Nmap
- Net inventory, admin service updates, check host and service activity.
- Default tcp ports. 1000 common ports(randomly).
- TCP TCP SYN are the default scans used by Nmap if run with sudo permissions.
- If run without sudo permissions, Nmap defaults to the TCP Connect 3-way handshake scan we saw in the previous task.
| Option | Description |
|---|---|
--script=vuln |
activate all scripts in the "vuln" category |
--reason |
explains how Nmap made its conclusion |
-v |
Verbose |
-vv-vvv |
More verbose |
-d |
debugging |
-dd |
more details for debugging |
-A |
Enable OS detection version detection script scanning and traceroute |
-O |
Try to get OS |
-Pn |
Disable host discovery and scan for open ports |
Host discovery
Nmap Host discovery, ping scan without port scan. #flashcard
nmap -sn 192.168.1.0/24
| Opction | Description |
|---|---|
-sn 192.168.1.0/24-sn 192.168.0.1-254-sn 192.168.0.0/24 |
Host discovery only Ping Scan - disable port scan |
-e eth0 |
Specify interface |
-PU -sn MACHINE_IP/24 |
UDP ping scan |
-PE -sn |
PE = ICMP echo ping scanBarrido Ping ICMP, Ping Scan - disable port scan Scan any ports -- forcing it to rely primarily on ICMP echo packets Also cause nmap to send a TCP SYN packet to port 443, as well as a TCP ACK (or TCP SYN if not run as root) packet to port 80 of the target. |
-PM -sn |
ICMP Address mask scan - queries (ICMP Type 17) and checks address mask reply (ICMP Type 18). use if ICMP is blocked |
-PP -sn |
ICMP timestamp scan - request (ICMP Type 13) |
-PS -sn MACHINE_IP/24-PS21-25 |
TCP SYN Ping scan (root required) |
-PR -sn TARGETS-PR -sn MACHINE_IP/24 |
Only to perform an ARP scan without port-scanning |
-PA -sn MACHINE_IP/24-PA21-25 |
TCP ACK ping scan (root required) |
-PO -sn 192.168.18.1-255 |
IP protocol scan. Use different protocols to test the connectivity |
-n |
No DNS lookup - online hosts (more fast) |
-R |
reverse-DNS lookup for all hosts even for offline hosts |
--dns-servers DNS_SERVER |
use a specific DNS server |
nmap 192.168.0.1nmap host.com |
Get live hosts, open ports, services, packet types, firewalls, info of OS and versions. |
nmap -iL list_of_hosts.txt |
Provide a file as input for your list of targets |
nmap -sL TARGETS |
List of the hosts that Nmap will scan without scanning them |
Port scan
Nmap General Scan #flashcard
sudo nmap IP -n -p- -Pn -sS -vvv --open --min-rate 5000 -oG nmap_scan
Send all ports to the clipboard
grep "Ports:" nmap_scan | sed 's/.*Ports: //;s/, /,/g' | tr ',' '\n' | awk -F'/' '{print $1}' | paste -sd ',' | xsel -ib --trim
| Option | Description |
|---|---|
-sS |
Silent, TCP SYN scan, Stealthy, Fast |
-sT |
TCP Connect Scans using 3-way handshake |
-sU |
UDP scan |
nmap --open |
Just show open ports |
-r |
Scan the ports in consecutive order |
nmap 192.168.1.1/24 |
Scan all devices and port, OPEN at the same time |
nmap 192.168.0.1 192.168.0.4 192.168.0.7 |
Some IPs |
nmap 192.168.0.1-34 |
Range of IPs |
-T<0-5> |
Nmap Speed levels |
--min-rate 5000 |
Set a min of packets per second before to skip the scan (recommend 5000) |
--min-parallelism=100 |
At least 100 probes in parallel; (host discovery or open ports) |
-F |
Fast 100 common ports |
-p 80-p80 |
Specific port |
-top-ports 2000 |
2000 Most used ports |
-p 1-77 -p1-77 |
From 1 to 77 |
-p 22,80 |
port 22 and 80 |
-p- IP |
All 65535 ports |
Advanced port scan (Firewall IDS evasion)
| Option | Description |
|---|---|
| Against Firewall#Stateless | A stateless firewall will check if the incoming packet has the SYN flag set to detect a connection attempt. |
-f |
Fragment IP data into 8 bytes |
-ff |
Fragment IP data into 16 bytes |
--source-port PORT_NUM |
specify source port number |
--data-length 21 |
append random data to reach given length (58 +21) |
--scan-delay <time>ms |
add a delay between packets sent |
--badsum |
generate in invalid checksum for packets |
nmap --mtu 16 |
Change MTU (8 multiple) |
-sN MACHINE_IP |
TCP Null Scan (TCP request is sent with no flags set at all, target host should respond with a RST if the port is closed) |
-sF MACHINE_IP |
TCP FIN Scan (a request is sent with the FIN flag, expects a RST if the port is closed.) |
-sX MACHINE_IP |
TCP Xmas Scan (send a malformed TCP packet (FIN, PSH, and URG flags simultaneously) and expects a RST response for closed ports.) |
| Map out the firewall rules. |
Could ACK and window scans are exposing the firewall rules, not the services. |
-sA MACHINE_IP |
TCP ACK Scan |
-sW MACHINE_IP |
TCP Window Scan |
-sM MACHINE_IP |
TCP Maimon Scan (FIN and ACK bits are set.) |
--scanflags URGACKPSHRSTSYNFIN MACHINE_IP |
Custom TCP Scan |
-S SPOOFED_IP MACHINE_IP -e NET_INTERFACE -Pn -S SPOOFED_IP MACHINE_IP |
Spoofed Source IP |
--spoof-mac SPOOFED_MAC -Pn--spoof-mac Dell -Pn |
Spoofed MAC Address |
nmap -D DECOY_IP,ME MACHINE_IPnmap -D DECOY_IP,RND,ME MACHINE_IP |
Decoy Scan (ME=myIP, RND=randomIP) |
sudo nmap -sI ZOMBIE_IP MACHINE_IP |
Idle (Zombie) Scan |
Post port scan
Nmap Focused scan #flashcard
sudo nmap IP -sCV -p 22,80 -oN targeted
| Option | Description |
|---|---|
-sV |
Deep scan, determine service/version info on open ports force 3-way handshake don't work with -sS |
-sV --version-light |
try the most likely probes (2) |
-sV --version-all |
try all available probes (9) |
-sC |
Scan with the default Nmap scripts |
-sCV |
-sV + -sC |
-O |
detect OS |
--traceroute |
run traceroute to target |
-A |
equivalent to -sV -O -sC --traceroute |
-oN |
save output in normal format |
-oG |
save output in grepable format |
-oX |
save output in XML format |
-oA |
save output in normal, XML and Grepable formats |
NSE
- Nmap Scripting Engine
- It's a Lua interpreter that allows Nmap to execute Nmap scripts written in Lua language.
/usr/share/nmap/scriptsftp-anon.nse- to check anonymous ftp accounthttp-robots.txt.nseto check relevant info about robots files
| Option | Description |
|---|---|
locate .nse | grep smb-*locate .nse | grep ftp-* |
Search specific scripts |
-sC or --script=default |
To execute main Scripts |
-sCV |
like -sV + scripts |
--script=<script-name>--script=scrpt1,scrpt2 |
To run a specific script |
--script "ftp*" |
Run all that start with ftp |
--script |
activate a script |
--script=vuln--script vuln |
Run all "vuln" scripts category/usr/share/nmap/scripts (Intrusive) |
--script="vuln and safe" -sV |
Use the scripts in the "vuln and safe" category |
--script-args |
Some scripts require arguments |
--script=http-enum.nse |
Enum http service |
--script=http-shellshock --script-args "http-shellshock.uri=/URI_SCRIPT_CGI_PATH.cgi" |
Detect ShellShock CVE-2014-6271 |
Categories
| Script Category | Description |
|---|---|
auth |
Authentication related scripts |
broadcast |
Discover hosts by sending broadcast messages |
brute |
Performs brute-force password auditing against logins |
default |
Default scripts, same as -sC |
discovery |
Retrieve accessible information, such as database tables and DNS names |
dos |
Detects servers vulnerable to Denial of Service (DoS) |
exploit |
Attempts to exploit various vulnerable services |
external |
Checks using a third-party service, such as Geoplugin and Virustotal |
fuzzer |
Launch fuzzing attacks |
intrusive |
Intrusive scripts such as brute-force attacks and exploitation Pueden proporcionar información valiosa sobre vulnerabilidades y debilidades en la red. |
malware |
Scans for backdoors |
safe |
Safe scripts that won’t crash the target |
version |
Retrieve service versions |
vuln |
Checks for vulnerabilities or exploit vulnerable services |
Detect the high risk HTTP methods
nmap --script http-methods -p 80 example.com
Active Reconnaissance#Subdomain Brute force
| Option | Description |
|---|---|
--script=droadcast-dns-service-discovery |
DNS discovery |
--script dns-brute |
Brute-force |
--script dns-srv-enum "dns-srv-enum-domain='domain'" |
DNS Enum |
SMB
| Option | Description |
|---|---|
-p445 --script smb-enum-* |
Run smb scripts to enum |
p445 --script smb-enum-* --script-args smbusername=administrator,smbpassword=smbserver_771 |
Run smb scripts to enum with credentials |
--script smb-protocols |
list the supported protocols and dialects of an SMB server. |
--script smb-vuln* -p139,445 |
Check vulns |
--script smb-os-discovery |
|
--script=smb-enum-shares,smb-enum-users |
NetBIOS
| Option | Description |
|---|---|
-sV --script nbstat -p 137 |
NetBIOS enum |
-sV -v --script nbstat |
SNMP
| Option | Desctiption |
|---|---|
-sU -p 161 --script snmp-brute |
Brute-force community strings |
-sU -p 161 --script snmp-* demo.ine.local > snmp _info |
Run all scripts ans save results |
LDAP
| Option | Desctiption |
|---|---|
nmap -sU -p 389 IP |
Simple scan |
nmap -p 389 --script ldap-brute --script-args ldap.base='"cn=users,dc=CEH,dc=com"' IP |
Scripts |
NFS
| Option | Desctiption |
|---|---|
sudo nmap IP -p111,2049 -sV -sC |
Simple scan |
sudo nmap --script nfs* IP -sV -p111,2049 |
Scripts |
SMTP
| Option | Desctiption |
|---|---|
nmap -p 25 --script=smtp* IP |
Output formats
| Option | Desctiption |
|---|---|
-oN |
save output in normal format |
-oG |
save output in grepable format |
-oX |
save output in XML format |
-oA |
save output in normal, XML and Grepable formats |
Port states
- Open:
A service is listening on the specified port. - Closed:
No service is listening on the specified port, although the port is accessible.
By accessible, we mean that it is reachable and is not blocked by a firewall or other security appliances/programs. - Filtered:
Nmap cannot determine if the port is open or closed because the port is not accessible.
This state is usually due to a firewall preventing Nmap from reaching that port. Nmap’s packets may be blocked from reaching the port; alternatively, the responses are blocked from reaching Nmap’s host. - Unfiltered:
Nmap cannot determine if the port is open or closed, although the port is accessible.
This state is encountered when using an ACK scan-sA. - Open|Filtered:
Nmap cannot determine whether the port is open or filtered. - Closed|Filtered:
Nmap cannot decide whether a port is closed or filtered.
Methodology