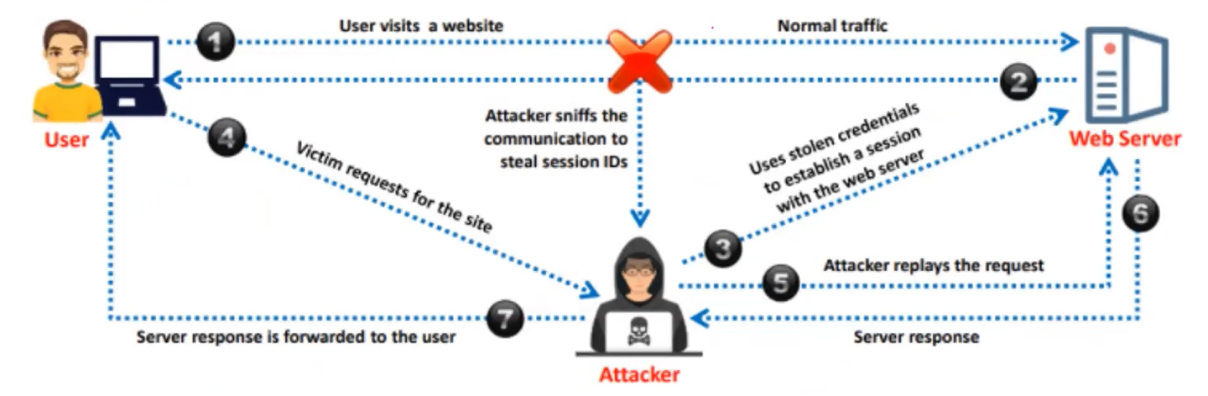
MITM attack
- Man in the middle
- Attacker site between the target and the server
- Can change the info
- Sniffing can be used
- Relatively simple to carry out if the two parties do not confirm the authenticity and integrity of each message.
- Affect cleartext protocols
DNS poisoning
Create a file to emulate DNS record
echo "ATTAQUER_IP *.sportsfoo.com" > dns
ARP poisoning
echo 1 > /proc/sys/net/ipv4/ip forward
Cain & Abel
- Scan MAC adress
- New ARP Poison Routing
- It can be used to monitoring the traffic between two systems and detect this type of attacks
Tools
Mitigation
- Proper authentication along with encryption or signing of the exchanged messages.
- With the help of PKI and trusted root certificates, TLS protects from MITM attack .
- Set static arp tables